This blog is an excerpt from the Chainalysis 2020 Crypto Crime Report. Click here to download the full document!
On December 13, 2019, the city of New Orleans was forced to declare a state of emergency after its computers were shut down in a ransomware attack. By December 19, the downtime caused by the attack had already cost the city over $1 million. Unfortunately, this story is all too familiar. Local governments around the world, from Baltimore to Johannesburg, have suffered extensive economic damage from ransomware attacks, not to mention hundreds of hospitals, schools, businesses, and even the United States Military.
Ransomware attacks are on the rise, but it’s difficult to calculate their impact. According to statistics posted by the U.S. Department of Homeland Security, more than 4,000 ransomware attacks have taken place daily since 2016, a 300% increase over the approximately 1,000 attacks per day seen in 2015. A report from McAfee Labs in August stated that ransomware attacks more than doubled year over year. These figures likely underestimate the true scope of the problem, as many businesses simply opt to pay the ransom without reporting the attack. In fact, some companies worry that acknowledging a ransomware attack could drive down their share price. In addition to the direct costs of ransom payment estimated below, victimized businesses must also account for the indirect costs of downtime.
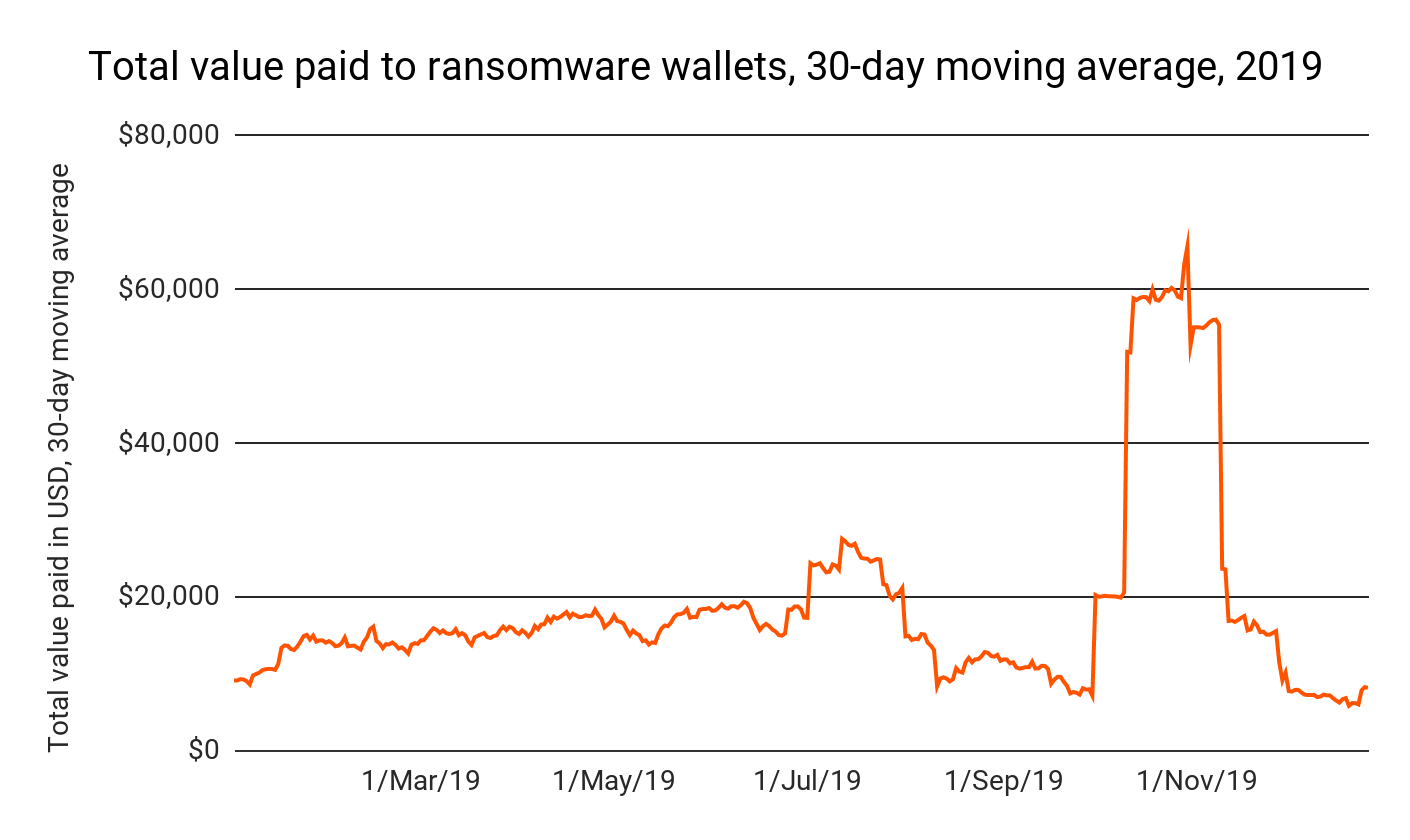
Our data shows a total of just over $6.6 million paid to ransomware-affiliated addresses in 2019, largely driven by an October surge in attacks carried out using the Bitpaymer, Ryuk, and Defray777 ransomware strains. However, this yearly total is almost certainly an underestimate. Even with blockchain analysis, it’s difficult to quantify the number of ransoms paid if victims don’t report attacks.
The problem is compounded by the prevalence of ransomware as a service (RaaS). Many hackers who develop ransomware technology now allow less sophisticated hackers to rent access to it, just as a business would pay a monthly fee for software like Google’s G-Suite. The key difference is that the builders of the ransomware also get a cut of the money from any successful attack. Below is an example of an ad for a new RaaS strain called MegaCortex, explaining the cost structure and process for new buyers to get started.
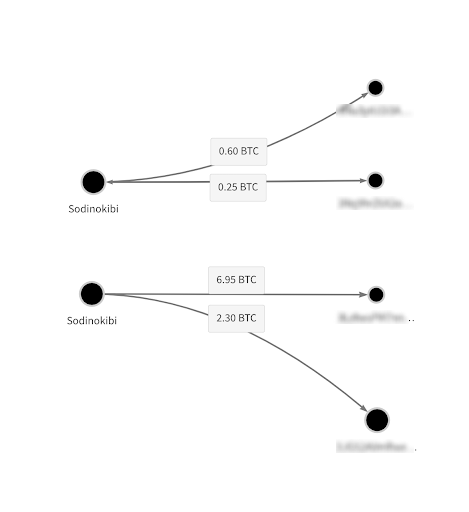
The Chainalysis Reactor graph below shows two examples from one of 2019’s most popular RaaS strains, Sodinokibi. In both cases, the Sodinokibi RaaS user on the left sends 70-75% of ransoms taken to one address, likely their own, and 20-25% to another address, likely controlled by the RaaS vendor.
RaaS has led to more attacks, making it even harder to quantify the full financial impact. RaaS has also drastically changed the nature of ransomware attacks themselves, especially in terms of the size of ransoms requested and typical victim profile. We’ll explore how RaaS attacks differ from traditional ransomware attacks in greater detail later.
Even though we can’t measure the total impact and costs of ransomware, we can analyze the data we do have on a percentage basis to understand the trends that defined 2019 and could continue into 2020.
Let’s start by looking at which regions are suffering the brunt of ransomware attacks. Below, we approximated victims’ location based largely on the location of the exchanges they used to pay ransoms. Assigning exchanges a location is a complex exercise in its own right. Since exchanges typically serve customers across borders, simply knowing where they’re headquartered isn’t enough to understand which market each primarily serves. There’s no single indicator we use to determine an exchange’s market categorization, but some of the factors we use include top fiat trading pairs, timezone analysis of transaction patterns, web traffic origin, company registration, public sourcing information, and direct conversations with the exchanges. Exchanges we place in the “global” category are those whose activity is dispersed across many regions.
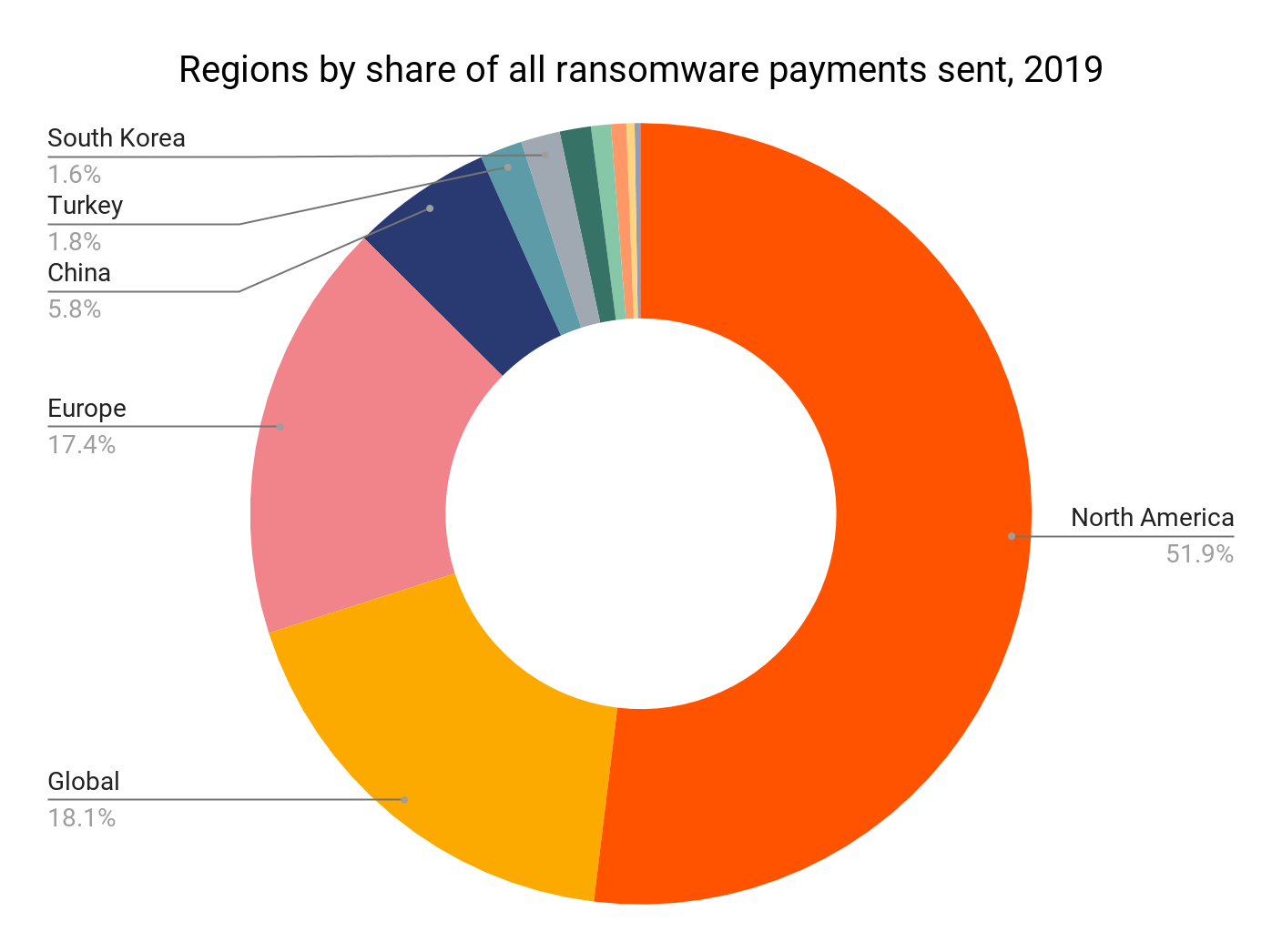
In 2019, 52% of ransomware payments we tracked came from North America, which is a large uptick from just 31% in 2018. Outside reports also support our finding that ransomware attacks increased in North America in 2019. The second-largest share of ransom payments came from users at global exchanges, followed by European exchanges.
While it’s tempting to do so, we decided not to try to approximate ransomware attackers’ geographic locations based on the exchanges they used, as we did for victims. For one thing, attackers are likely attempting to obfuscate their activity and may be more likely to use services less tied to their own location, whereas victims are more likely to choose the exchange or service that’s most convenient when paying ransoms.
As we dug into the data, we also found that ransomware attackers’ cashing out activity is concentrated to just a few exchanges. Below, we’ll look at the most popular exchanges for ransomware attackers over time.
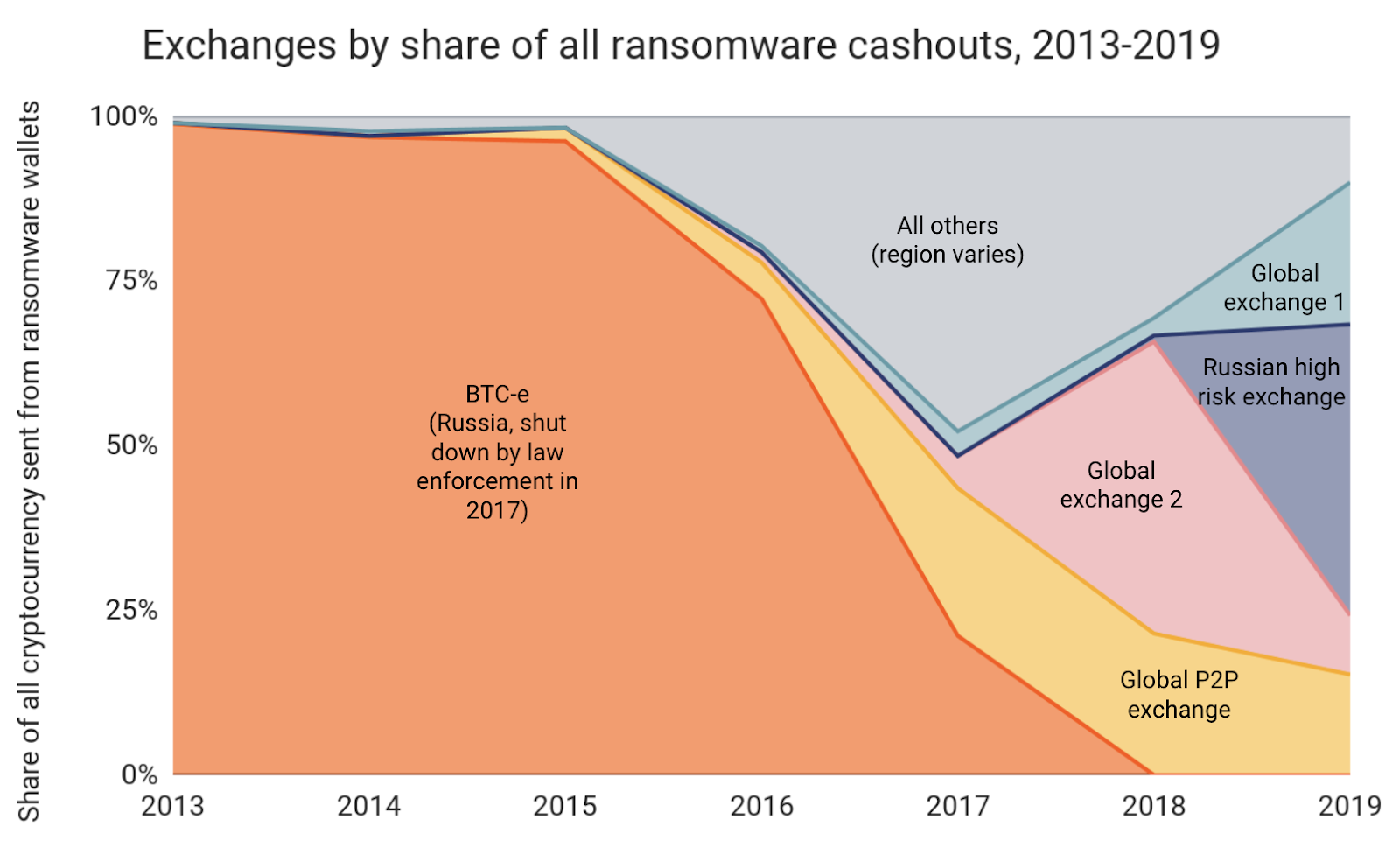
Digging in, we see that nearly all of the funds collected by the top ransomware strains from 2013 through 2016 were cashed out at one exchange: Russia-based BTC-e, which before its shutdown by law enforcement in 2017 was one of the most popular exchanges in the world. Given BTC-e’s global reach, this data alone wouldn’t be enough to conclude that most ransomware attackers in those years were based in Russia. However, we know from on-the-ground intelligence and reporting from security experts that the creators of popular ransomware strains such as CryptoLocker, Locky, and Cerber were in fact based in Russia.
After BTC-e’s shutdown in 2017, ransomware attackers shifted to cashing out at exchanges with large, international user bases, including one popular P2P exchange. This could be purely a function of the same attackers turning to other global exchanges after BTC-e’s shutdown. However, the shift could also reflect the proliferation of RaaS, and how it enables a larger pool of lower-level cybercriminals to launch ransomware attacks. If there’s a growing number of attackers around the world, it makes sense that we’d see a diversification in the number of exchanges attackers use to cash out. But we can’t say for certain. It’s also interesting to note that another Russia-based exchange began receiving substantial funds from ransomware addresses in 2018, soon after BTC-e’s demise. Their share has continued to grow, as that exchange took in nearly 44% of all ransomware funds sent to exchanges in 2019.
Like the exchanges they use to cash out, we know that the ransomware strains favored by attackers also tend to be concentrated to just a few at any given time. You can see this on the chart below, which shows ransomware strains over time by the share of total ransomware payments they collected.
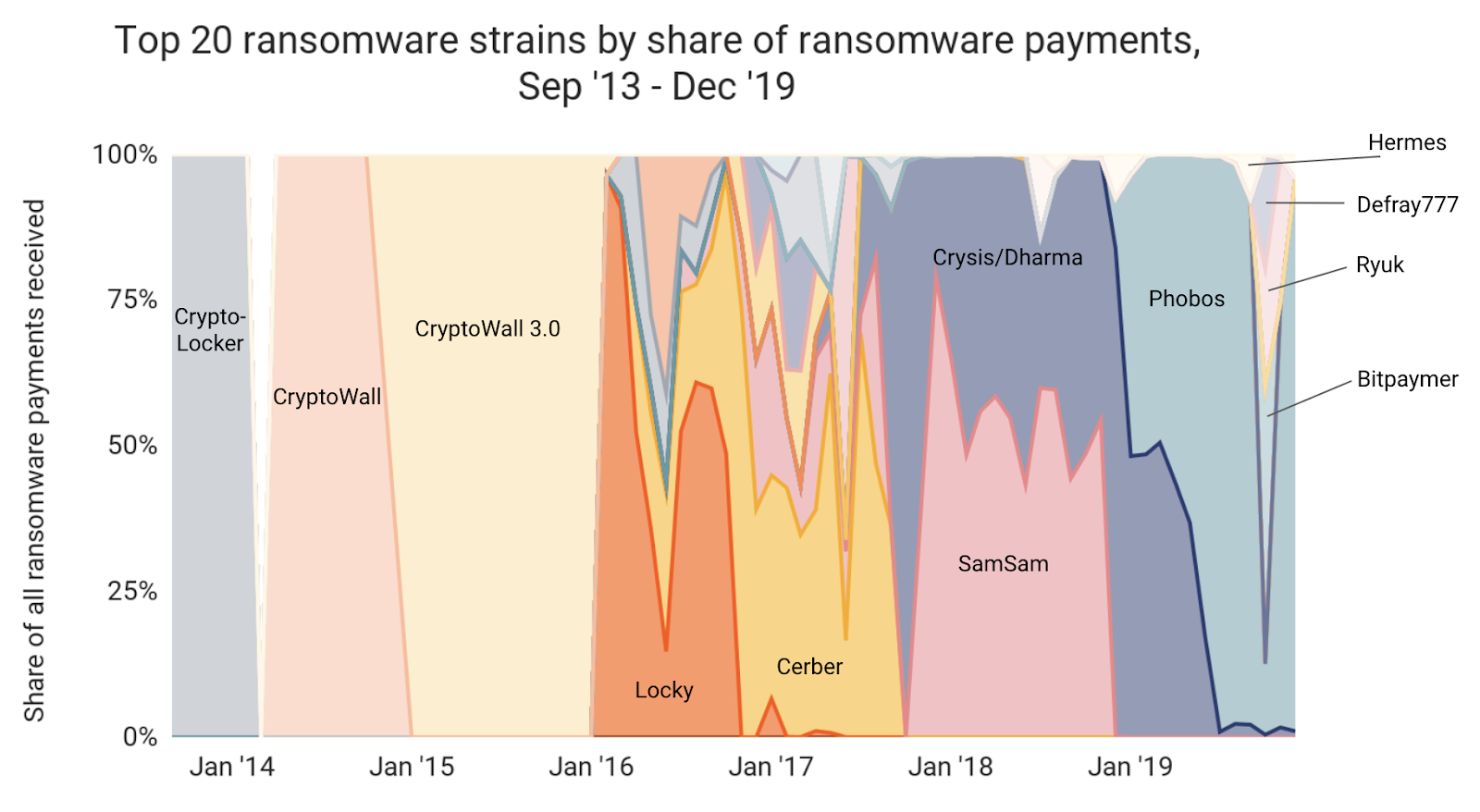
Individual strains tend to dominate for five to seven months at a time, before dying out and being replaced by other strains. But not all strains behave the same way. In the next section, we’ll explore the differences in attack patterns between the two major types of ransomware strains: traditional ransomware and RaaS.
How RaaS differs from ransomware
With RaaS on the rise, two distinct types of ransomware attacks emerge. On one end, we still see traditional, sophisticated, ransomware campaigns targeted at large organizations or, in the case of nation-state aligned hackers, geopolitical targets. On the other end of the spectrum, we see RaaS attacks carried out on smaller organizations by less sophisticated hackers known as affiliates in the hacking world. “The victims definitely tend to be smaller in RaaS,” says Bill Siegel, CEO of Coveware, a ransomware incident response provider. “The affiliates buying RaaS tend to be less sophisticated and have fewer resources, so they go after victims that are the lowest-hanging fruit.”
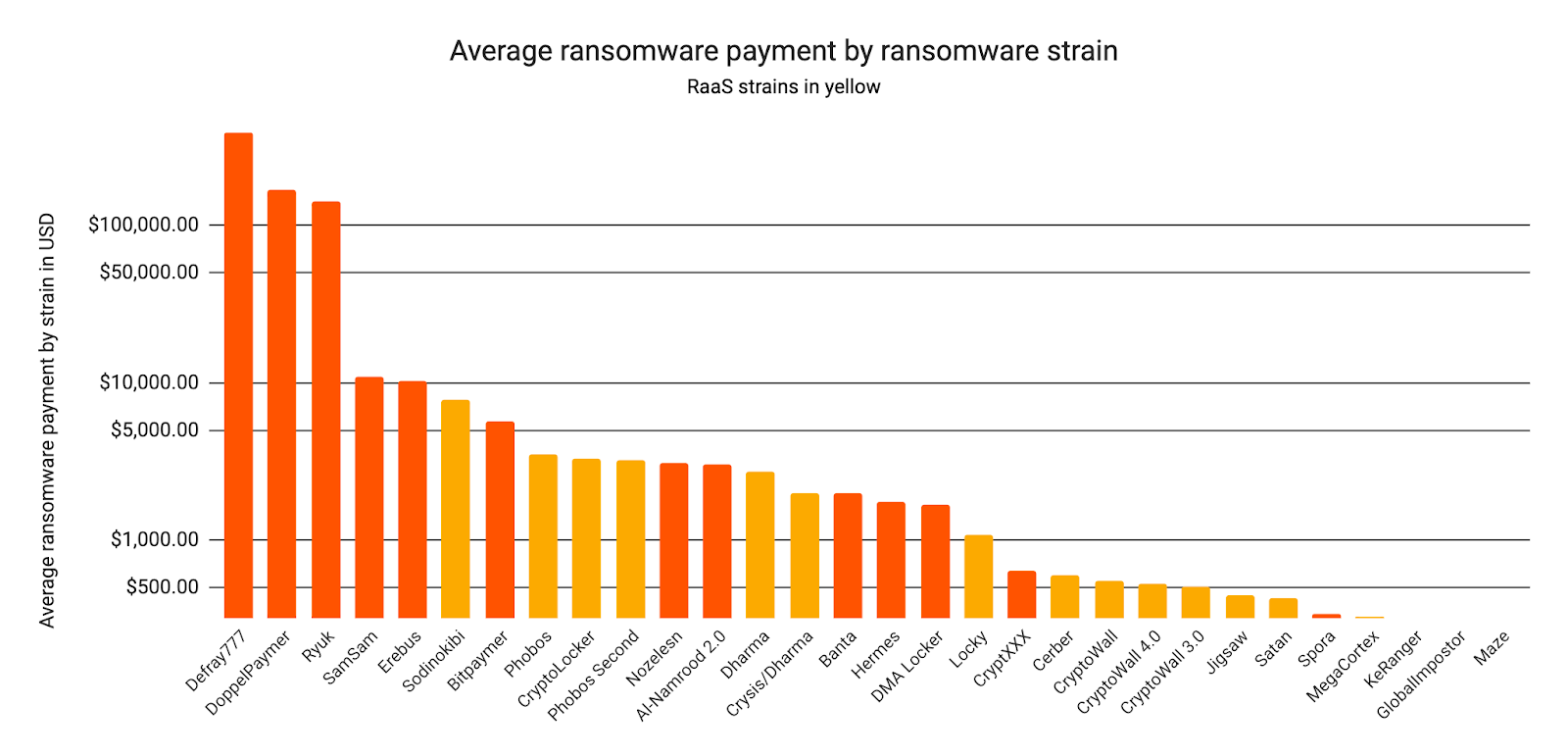
The data bears this out. Above, we see that the RaaS strains highlighted in yellow tend to receive lower average transfers from victims. Sodinokibi, which burst onto the scene in 2019, brings in larger transfers than any other RaaS strain, and is the only RaaS strain to cross the $5,000 average transfer barrier.
Bill and his team watched the growth and spread of Sodinokibi throughout the year first-hand, and their observations lend insight into how RaaS strains spread: “We saw the first Sodinokibi attacks in spring of 2019, which we believe were test runs for the developers and original affiliates. Soon after that, the developers were pitching Sodinokibi to select affiliates on popular hacking forums.”
RaaS developers are able to shift careers from being on the “front lines” to running distribution and recruitment. It’s the same industry, but a different role in the supply chain. Developers can make more money distributing and managing RaaS than they can pulling off attacks on their own.
The affiliates, for their part, seem perfectly willing to test the market and find strains that work for them. “Anecdotally, we definitely hear affiliates posting about their experience with different RaaS strains and looking for providers who give them a bigger cut,” says Bill. We can see possible examples of this in the on-chain data.
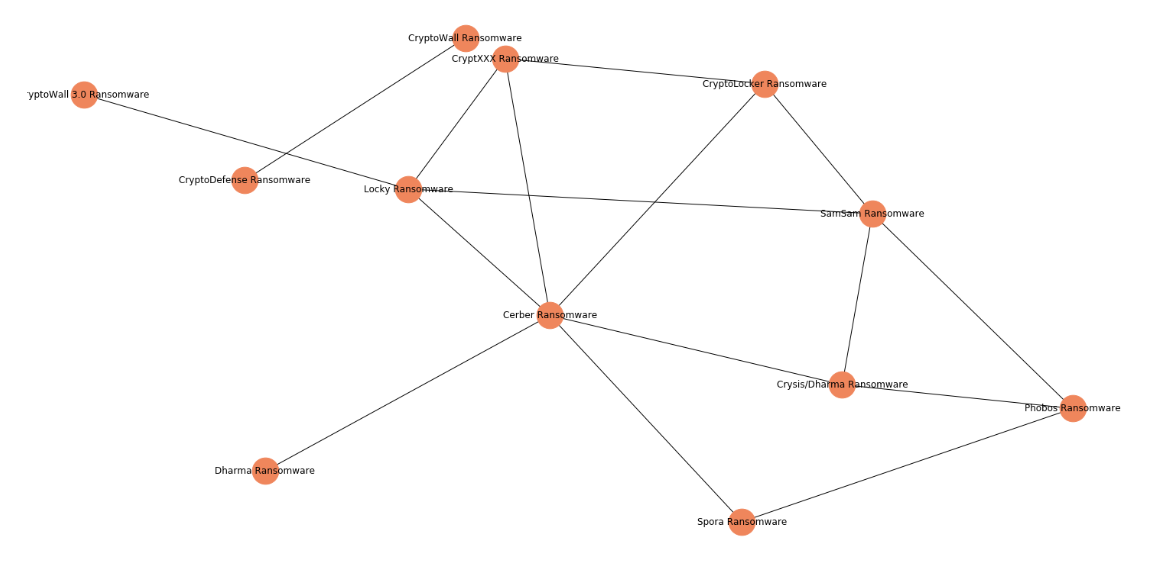
The network graph above shows numerous transfers linking cryptocurrency addresses associated with different ransomware strains. It’s possible that some of those connections are coincidental; for instance, some strains may be linked because attackers utilize the same mixing service. However, the sheer number of connections, combined with our anecdotal knowledge, suggest that some of these transactions are examples of RaaS users shopping around, or even RaaS vendors selling multiple strains. The latter could even suggest that a few large vendors are dominating the market, but we can’t say for certain.
Let’s take a closer look at the connections between two ransomware types – Phobos and Crysis Dharma – using Chainalysis Reactor.
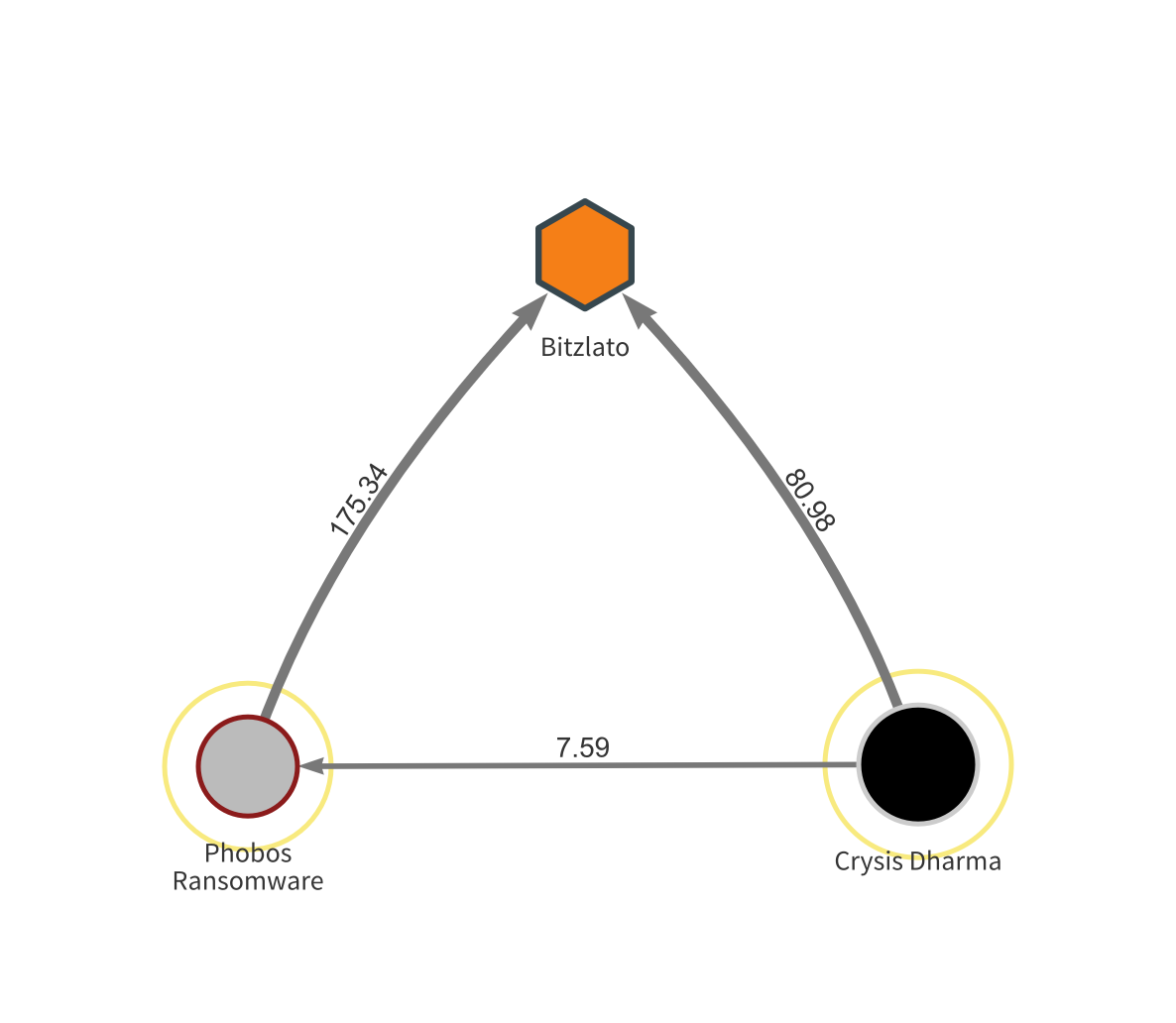
Here, we see an address associated with Crysis Dharma sending funds to one associated with Phobos. Both send significant sums to the same wallet at Bitzlato, a Russian high risk exchange. While we can’t say for certain, our best guess is that both addresses at the bottom are controlled by the same RaaS vendor who sells access to both Phobos and Crysis Dharma, and sends funds from both back to their account at Bitzlato.
The good news and bad news on ransomware
The bad news is that the spread of RaaS to the cybercriminal masses means firms of all shapes and sizes need to be on guard for attacks. There are now more attackers who don’t need to go to the trouble of developing ransomware themselves, meaning it can be profitable for them to attack small organizations that more sophisticated hackers wouldn’t bother to target. The RaaS problem could get worse as the “market” for these malicious viruses matures, with RaaS vendors seeking to differentiate themselves by releasing more and more dangerous strains.
But the good news is that any business can protect itself from ransomware attacks by diligently following a few simple steps. Bill Siegel outlines some of these measures on the Coveware blog. For one, businesses should save three copies of their most important documents: one to their local drive, one to a cloud backup system such as Dropbox, and one to an offline, physical storage unit such as a USB or external hard drive. That way, the files you need can survive in the event you are attacked. In order to prevent attacks from happening, Bill recommends businesses follow best practices such as updating their operating systems frequently to get new security patches, using strong antivirus software, and enabling security measures such as two-factor authentication and password managers.
In the event your business does fall victim to a ransomware attack, Bill outlines a few steps to take immediately. First, you should isolate any affected machines by disconnecting them from any networks they’re connected to, such as wifi or bluetooth, and powering them down. Second, close all remote desktop protocol (RDP) ports, as they’re a common vector for ransomware attacks. Finally, update all administrative and user credentials, so that hackers lose whatever access they have to your systems. From there, you should restore as much of your data as possible from backups. Bill, along with the FBI, recommends not paying ransoms to attackers unless there’s no other way for your business to regain crucial data.
We also implore any company hit with ransomware to report the attack immediately. While it can feel scary to come forward and admit that your business has become a victim, it’s difficult for law enforcement and the cybersecurity industry to understand the full scope of the problem and dedicate the appropriate resources to address it with so many businesses choosing not to report. That fear of scrutiny ultimately helps ransomware attackers stay under the radar and claim more victims. Given the number of prestigious organizations hit with ransomware, from FedEx to Britain’s NHS to countless local governments, we think it’s time to remove the stigma associated with these attacks — clearly, they can happen to any organization.
In the event you’re attacked, you should collect as much evidence as possible, such as screenshots of ransom messages you receive, and send it to investigators so they can know what strain of ransomware you’ve been hit with and start formulating a response. You can also report attacks to Chainalysis directly using our brand new ransomware reporting form. The details you provide can help us collect more data on your attackers and work with law enforcement to stop them.
This blog is an excerpt from the Chainalysis 2020 Crypto Crime Report. Click here to download the full document!
