This blog is a preview of our 2022 Crypto Crime Report. Sign up here to download your copy now!
Russia is a leading country in cryptocurrency adoption, placing 18th overall on our Global Crypto Adoption Index. But the story of Russia’s cryptocurrency usage isn’t entirely positive. Individuals and groups based in Russia — some of whom have been sanctioned by the United States in recent years — account for a disproportionate share of activity in several forms of cryptocurrency-based crime.
In this section, we’ll delve into two intertwined areas of Russia’s crypto crime ecosystem that, together, have serious implications for cybersecurity, compliance, and national security: ransomware and money laundering.
Russian cybercriminals set the pace for ransomware
Russia has long been home to some of the most skilled hackers in the world. According to cybersecurity investigators like Brian Krebs, this is largely due to the country’s excellence in computer science education, combined with low economic prospects even for those who are skilled in the field. Given this background, it may not be surprising that Russia leads the way in ransomware. But the degree to which Russia-based ransomware strains dominate is quite shocking.
Before we dive into the data, a quick explainer — we generally tie specific ransomware strains to Russian cybercriminals based on one of three criteria:
- Evil Corp. Evil Corp is a Russia-based cybercriminal organization that has been prolific in ransomware, and whose leadership is believed to have ties to the Russian government.
- Avoids CIS countries. The Commonwealth of Independent States (CIS) is an intergovernmental organization of Russian-speaking, former Soviet countries. Many ransomware strains contain code that prevents the encryption of files if it detects the victim’s operating system is located in a CIS country. In other cases, ransomware operators have even given over decryptors to return file access after learning they inadvertently targeted a Russian organization. We can attribute CIS-avoiding strains to Russian cybercriminals, though with a lesser degree of confidence, as some of them may be based in other CIS countries.
- Other connections: language, affiliate location, etc. There are several other ransomware characteristics that can indicate a strain is likely based in Russia. Examples include ransomware strains that share documents and announcements in the Russian language, or whose affiliates are believed to be located in Russia with a high degree of confidence.
Using those three criteria, we show on the pie chart below the share of total ransomware revenue that went to strains affiliated with Russian organizations in 2021.
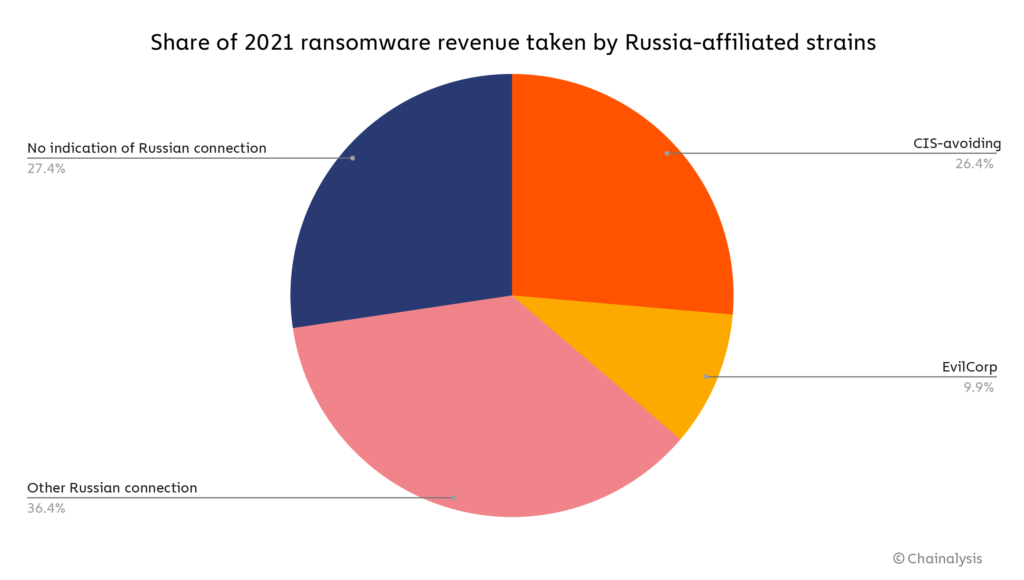
Overall, roughly 74% of ransomware revenue in 2021 — over $400 million worth of cryptocurrency — went to strains we can say are highly likely to be affiliated with Russia in some way.
Blockchain analysis combined with web traffic data also tells us that after ransomware attacks take place, most of the extorted funds are laundered through services primarily catering to Russian users.
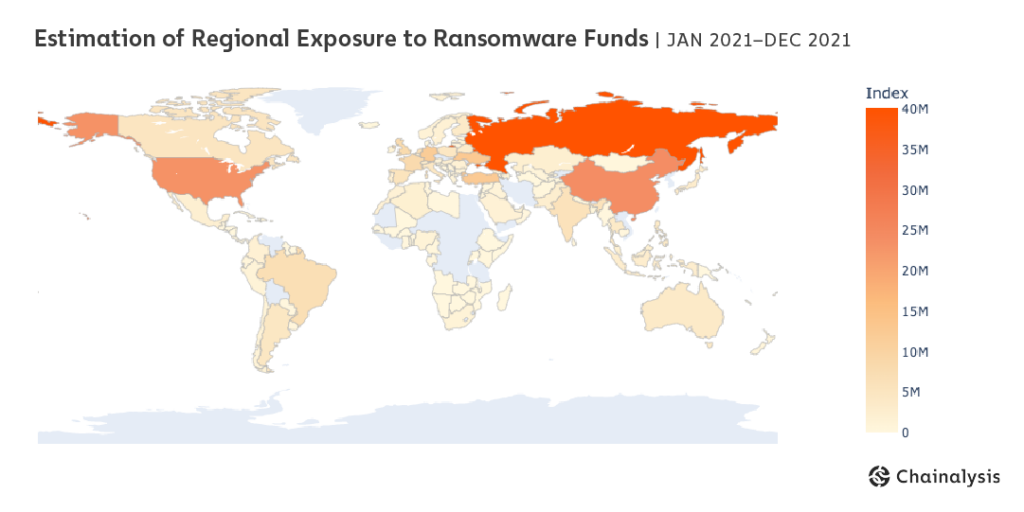
An estimated 13% of funds sent from ransomware addresses to services went to users estimated to be in Russia, more than any other region. That brings us to another point: A huge amount of cryptocurrency-based money laundering, not just of ransomware funds but of funds associated with other forms of cybercrime as well, goes through services with substantial operations in Russia.
Cryptocurrency-based money laundering in Moscow City
Russia is home to several cryptocurrency businesses that have processed substantial transaction volume from illicit addresses. In order to illustrate the scope of the problem, we thought it would be interesting to zoom in on businesses headquartered or with a significant presence in the capital’s financial district, Moscow City. Chainalysis is tracking several dozen cryptocurrency businesses operating in Moscow City alone that facilitate significant amounts of money laundering.
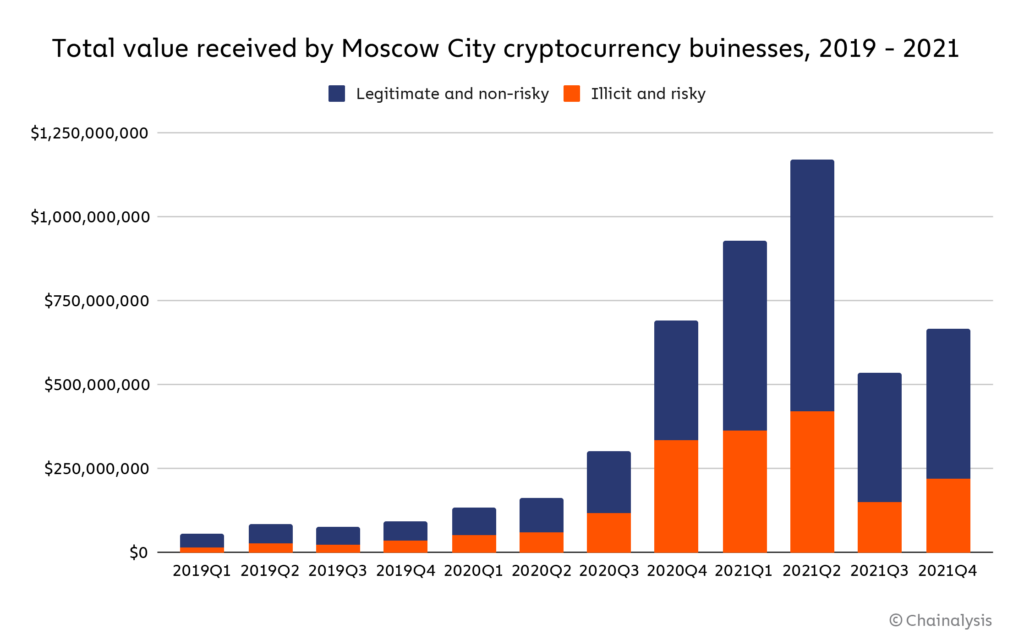
Note: The word “risky” here defines addresses connected to entities that, while not necessarily inherently criminal, are frequently linked to criminal activity, such as high-risk exchanges and mixers.
Collectively, these businesses receive hundreds of millions of dollars’ worth of cryptocurrency per quarter, with totals peaking at nearly $1.2 billion in the second quarter of 2021. In any given quarter, the illicit and risky addresses account for between 29% and 48% of all funds received by Moscow City cryptocurrency businesses. In total, across the three-year period studied, these businesses have received nearly $700 million worth of cryptocurrency from illicit addresses, which represents 13% of all value they’ve received in that time. Where do these illicit funds come from?
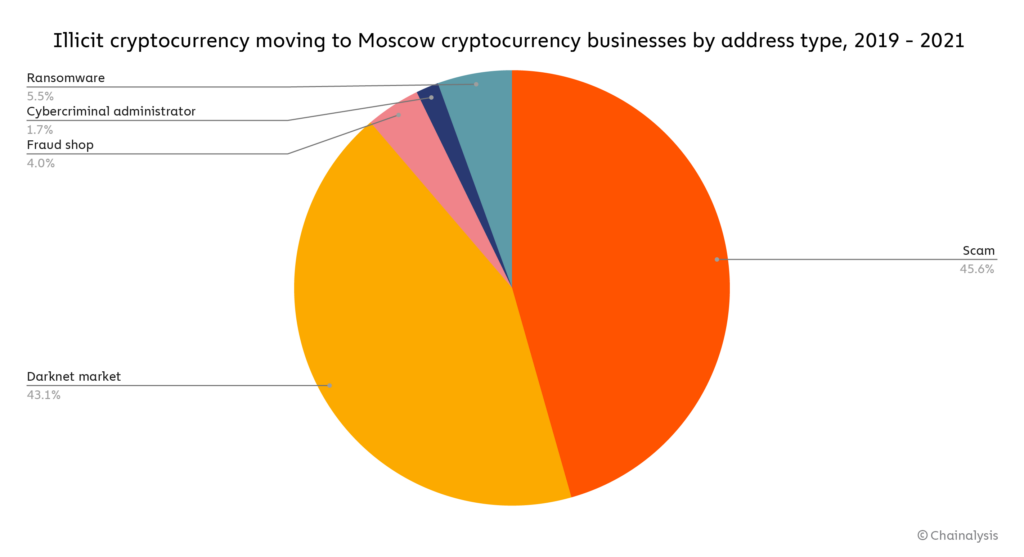
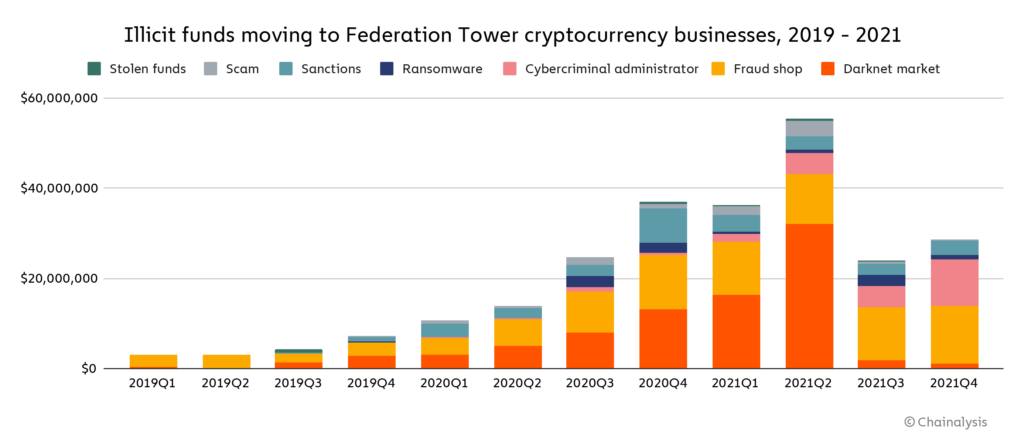
Note: “Cybercriminal administrator” refers to addresses that have been attributed to individuals connected to a cybercriminal organization, such as a darknet market.
Scams at $313 million and darknet markets at $296 million make up the vast majority of illicit cryptocurrency sent to the Moscow City cryptocurrency businesses we track between 2019 and 2021. Ransomware is third at $38 million.
Overall, the Moscow City cryptocurrency businesses we track vary greatly in the role that money laundering plays in their overall business. Some of them are big enough that despite receiving millions of dollars’ worth of funds from illicit addresses, those funds only represent 10% or less of all cryptocurrency they receive. Those instances could be attributed to the business’s lack of knowledge, rather than purposeful criminal activity. But for other Moscow City cryptocurrency businesses, illicit funds make up as much as 30% or more of all cryptocurrency received, which suggests those businesses may be making a concerted effort to serve a cybercriminal clientele.
Interestingly, over half of the businesses described above have reportedly operated in the same Moscow City skyscraper: Federation Tower.
 Credit: Mariano Mantel
Credit: Mariano Mantel
Federation Tower, a two skyscraper complex in the heart of Moscow City, is one of the most prestigious buildings in all of Russia, with several prominent businesses headquartered there and residential units going for upwards of $36 million. However, as outlets like Bloomberg and the New York Times have reported, Federation Tower is home to several cryptocurrency businesses that have facilitated extensive money laundering, accepting funds from addresses involved in various forms of cryptocurrency-based crime — especially scams, darknet markets, and ransomware.
Nothing is more emblematic of the growth of Russia’s crypto crime ecosystem, and of cybercriminals’ ability to operate with apparent impunity, than the presence of so many cryptocurrency businesses linked to money laundering in one of the capital city’s most notable landmarks.
Below, we highlight some of the cryptocurrency businesses with a presence in Moscow City that have facilitated the most money laundering or are otherwise notable:
| Name | Total cryptocurrency value received (2019 – 2021) | Illicit and risky cryptocurrency value received (2019 – 2021) | Illicit and risky share of all value received (2019 – 2021) | Notes |
| Garantex | $2,114,431,000 | $645,223,700 | 31% | Has received over $10 million from ransomware strains including NetWalker, Phoenix Cryptolocker, and Conti. |
| Eggchange | $34,081,220 | $3,705,827 | 11% | Has received hundreds of thousands of dollars’ worth of cryptocurrency from darknet markets, scams, fraud shops, and ransomware operators. Founder Denis Dubnikov was arrested for his alleged role in helping Ryuk ransomware operators launder funds. |
| Cashbank | $45,400,600 | $180,119 | 0.4% | While Cashbank’s detected money laundering activity is relatively low in volume, it advertises on forums frequented by illicit actors and criminals. |
| Buy-bitcoin | $41,604,170 | $11,374,910 | 27% | Has received $2.1 million from darknet markets, $400,000 in stolen funds, and $400,000 from ransomware attackers. |
| Tetchange | $21,903,700 | $4,621,440 | 21% | Has received over $1 million from darknet markets and $600,000 from ransomware attackers. |
| Bitzlato | $2,000,077,000 | $966,254,800 | 48% | Has received $206 million from darknet markets, $224.5 million from scams, and $9 million from ransomware attackers. |
| Suex | $426,189,500 | $158,856,100 | 37% | Has received $24 million from scams, $20 million from darknet markets, and $12 million from ransomware. Sanctioned by OFAC in 2021. |
What’s next for crypto crime in Russia?
Looking ahead, change may be on the way for Russia’s cryptocurrency ecosystem, especially as it relates to crime. In January 2022, Russian police arrested 14 affiliates of the REvil ransomware organization, marking one of the only times the local authorities have taken action against ransomware attackers operating within the country. However, analysts have speculated that the arrests were an act of diplomacy meant to cool tensions with the United States over Russia’s troop buildup on Ukraine’s borders, and may not indicate true commitment to fighting ransomware. At the same time, cryptocurrency’s regulatory status in Russia appears to be in flux, with President Vladimir Putin defending cryptocurrency miners at the same time the country’s national bank recommends an all-out ban on all cryptocurrency activity.
Regardless of what the future holds, it’s important to understand where things stand now: Russian cybercriminal organizations are some of the biggest perpetrators of cryptocurrency-based crime — especially ransomware — and local cryptocurrency businesses provide money laundering services that enable this activity. 2021 saw positive momentum against this issue, from the seizure of funds from ransomware organization DarkSide to the sanctioning of Suex and Chatex. Chainalysis looks forward to working with law enforcement, regulators, and compliance professionals in 2022 to keep that momentum going.
This blog is a preview of our 2022 Crypto Crime Report. Sign up here to download your copy now!
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making investment decisions.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.
