One of the most troubling trends in crypto crime right now is the stunning rise in funds stolen from DeFi protocols, and in particular cross-chain bridges. Much of the value stolen from DeFi protocols can be attributed to bad actors affiliated with North Korea, especially elite hacking units like Lazarus Group. We estimate that so far in 2022, North Korea-linked groups have stolen approximately $1 billion of cryptocurrency from DeFi protocols.
But today I had the privilege of joining the Axie Infinity team on stage at AxieCon to deliver some good news: With the help of law enforcement and leading organizations in the cryptocurrency industry, more than $30 million worth of cryptocurrency stolen by North Korean-linked hackers has been seized. This marks the first time ever that cryptocurrency stolen by a North Korean hacking group has been seized, and we’re confident it won’t be the last.
These are the results thus far of our investigation following the March 2022 theft of more than $600 million from Ronin Network, a sidechain built for the play-to-earn game Axie Infinity.
I am proud to say that the Chainalysis Crypto Incident Response team played a role in these seizures, utilizing advanced tracing techniques to follow stolen funds to cash out points and liaising with law enforcement and industry players to quickly freeze funds.
The seizures represent approximately 10% of the total funds stolen from Axie Infinity (accounting for price differences between time stolen and seized), and demonstrate that it is becoming more difficult for bad actors to successfully cash out their ill-gotten crypto gains. We have proven that with the right blockchain analysis tools, world-class investigators and compliance professionals can collaborate to stop even the most sophisticated hackers and launderers. There is still work to be done, but this is a milestone in our efforts to make the cryptocurrency ecosystem safer.
So, how did we do it? Here’s what we can share now.
How the Ronin Bridge was hacked & the stolen funds were laundered
The attack began when the Lazarus Group gained access to five of the nine private keys held by transaction validators for Ronin Network’s cross-chain bridge. They used this majority to approve two transactions, both withdrawals: one for 173,600 ether (ETH) and the other for 25.5 million USD Coin (USDC). They then initiated their laundering process – and Chainalysis began tracing the funds. The laundering of these funds has leveraged over 12,000 different crypto addresses to-date, which demonstrates the hackers’ highly sophisticated laundering capabilities.
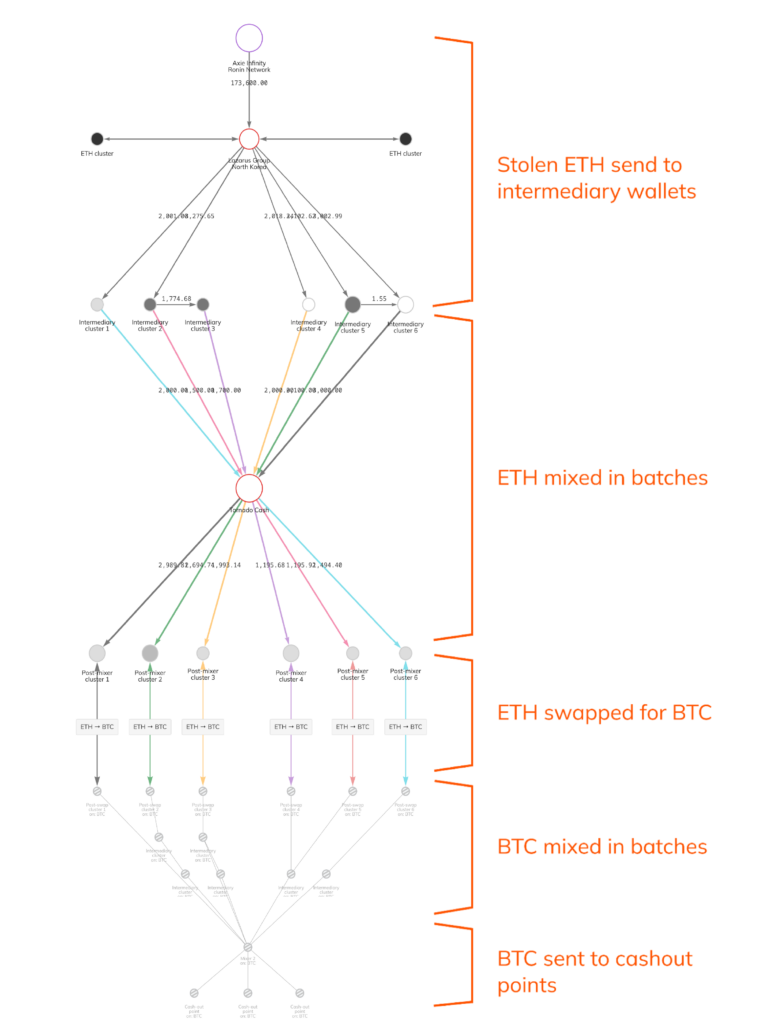
North Korea’s typical DeFi laundering technique has roughly five stages:
- Stolen Ether sent to intermediary wallets
- Ether mixed in batches using Tornado Cash
- Ether swapped for bitcoin
- Bitcoin mixed in batches
- Bitcoin deposited to crypto-to-fiat services for cashout
Lazarus Group has replicated this process with large portions of Ronin’s stolen funds. We can visualize it below using Chainalysis Reactor:
However, the U.S. Treasury’s Office of Foreign Assets Control (OFAC) recently sanctioned Tornado Cash for its role in laundering over $455 million worth of cryptocurrency stolen from Axie Infinity. Since then, Lazarus Group has moved away from the popular Ethereum mixer, instead leveraging DeFi services to chain hop, or switch between several different kinds of cryptocurrencies in a single transaction. Bridges serve an important function to move digital assets between chains and most usage of these platforms is completely legitimate. Lazarus appears to be using bridges in an attempt to obscure source of funds. With Chainalysis tools these cross chain funds movements are easily traced.
We can use Chainalysis Storyline to see an example of how Lazarus Group utilized chain-hopping to launder some of the funds stolen from Axie Infinity:
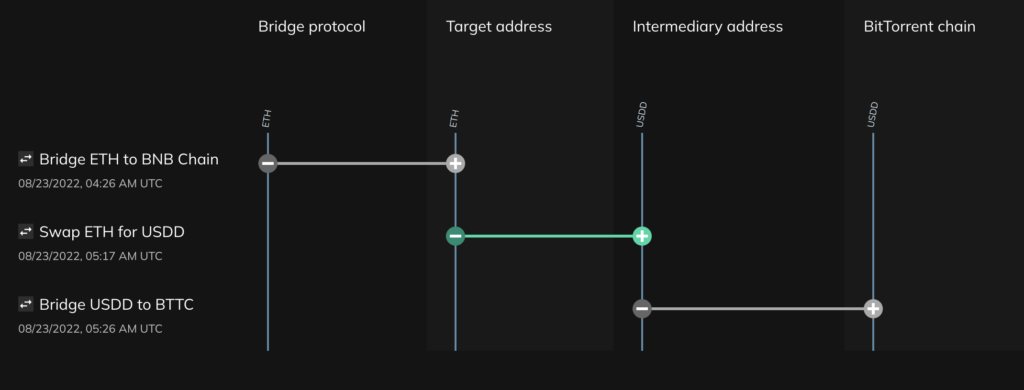
Above, we see that the hacker bridged ETH from the Ethereum blockchain to the BNB chain and then swapped that ETH for USDD, which was then bridged to the BitTorrent chain. Lazarus Group carried out hundreds of similar transactions across several blockchains to launder the funds they stole from Axie Infinity, in addition to the more conventional Tornado Cash-based laundering we covered above.
Transparency and collaboration are key
Cryptocurrency’s transparency is instrumental to investigating hacks like the one suffered by Axie Infinity. Investigators with the right tools can follow the money to understand and disrupt a cybercrime organization’s laundering activities. This would never be possible in traditional financial channels, where money laundering usually involves networks of shell companies and financial institutions in jurisdictions that may not cooperate.
Even so, these seizures would not have been possible without collaboration across the public and private sectors. Much of the funds stolen from Axie Infinity remain unspent in cryptocurrency wallets under the hackers’ control. We look forward to continuing to work with the cryptocurrency ecosystem to prevent them and other illicit actors from cashing out their funds.
