As blockchains have multiplied, so too have cybercriminals’ money laundering strategies. That’s why we’re thrilled to introduce Cross-Chain Investigations to Chainalysis Reactor — the best way to trace cryptocurrencies across blockchains.
How it works
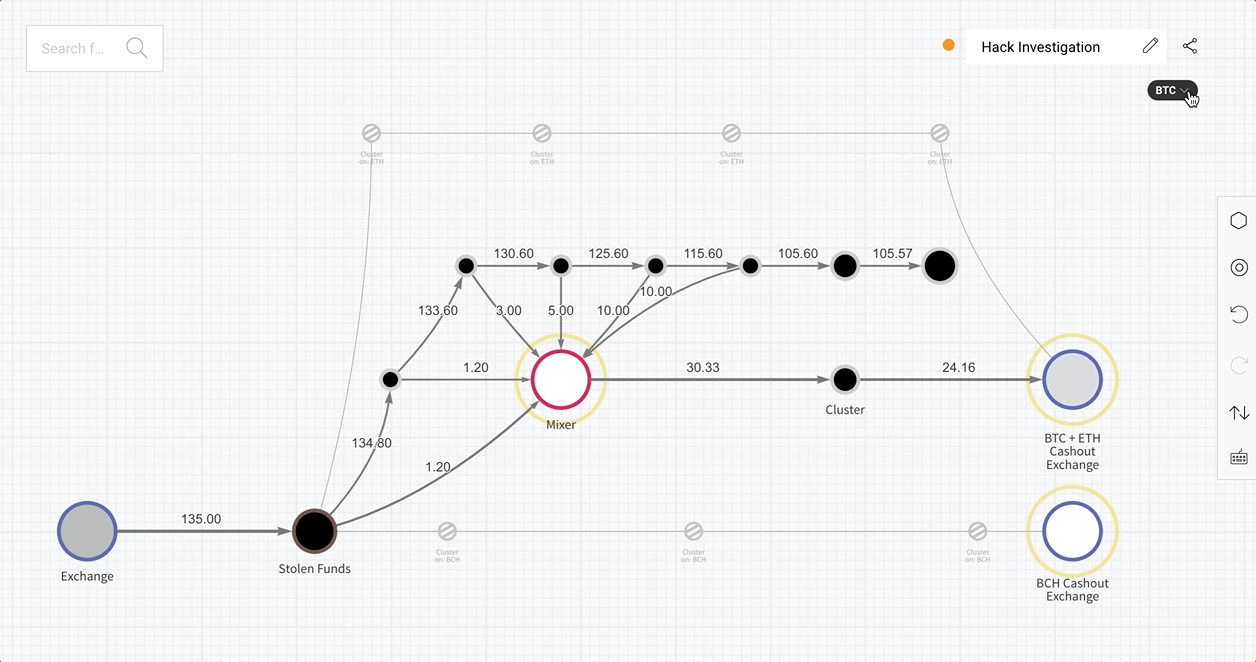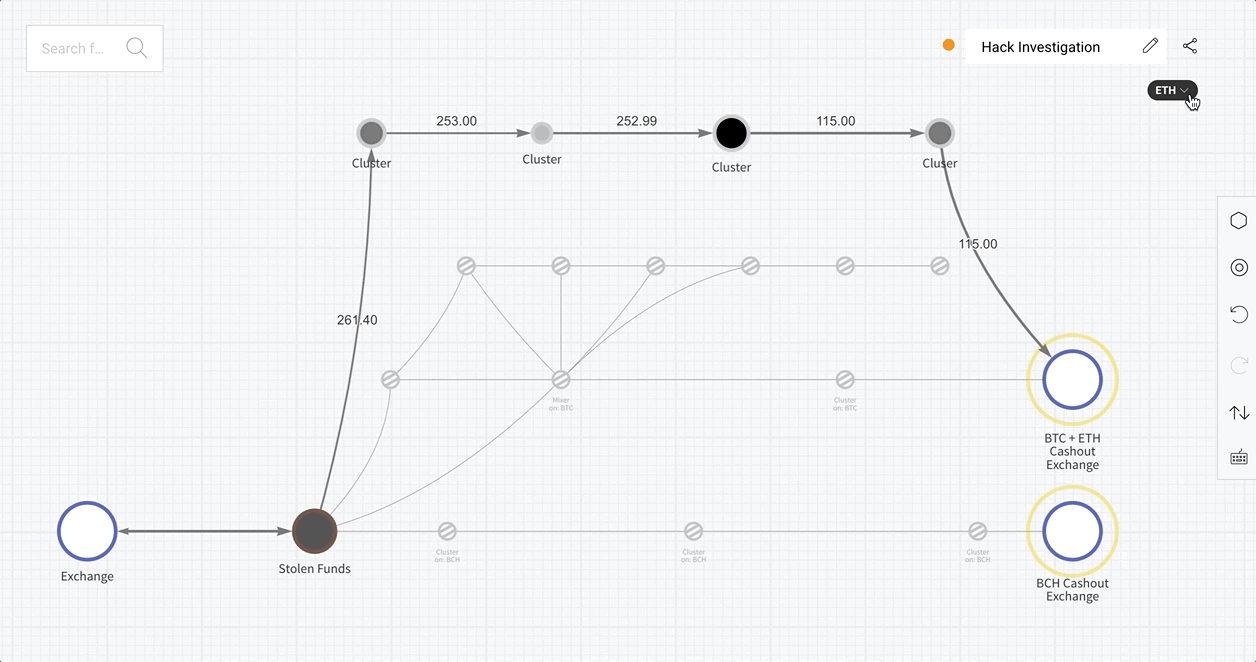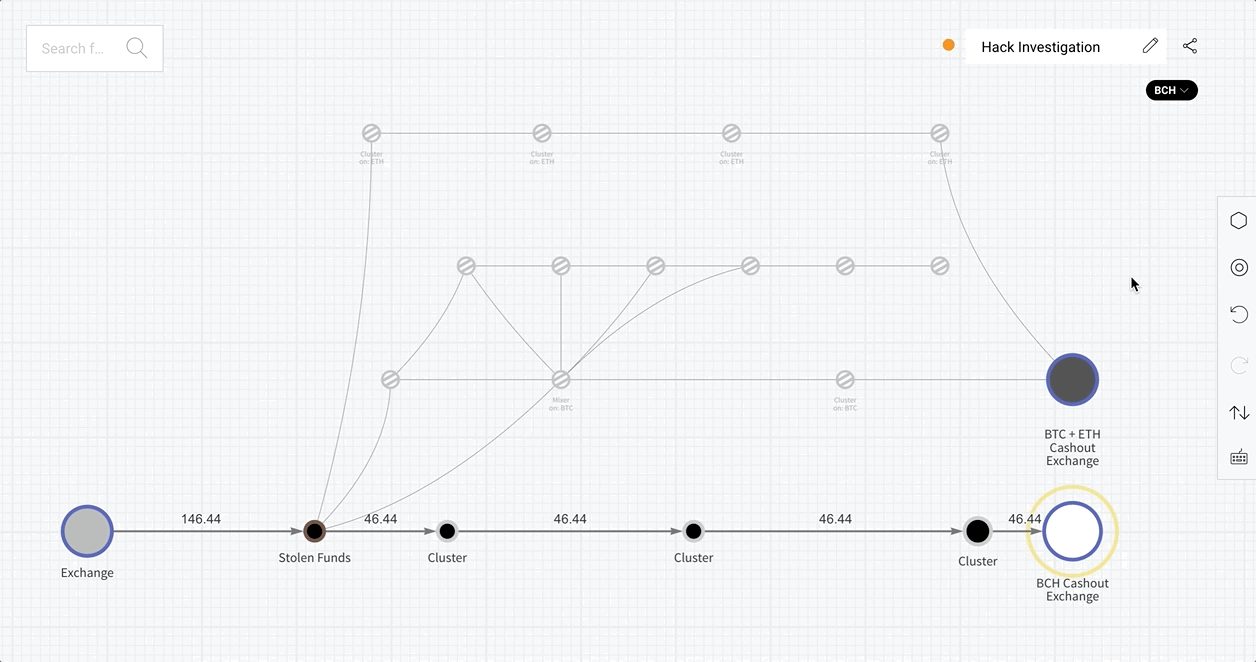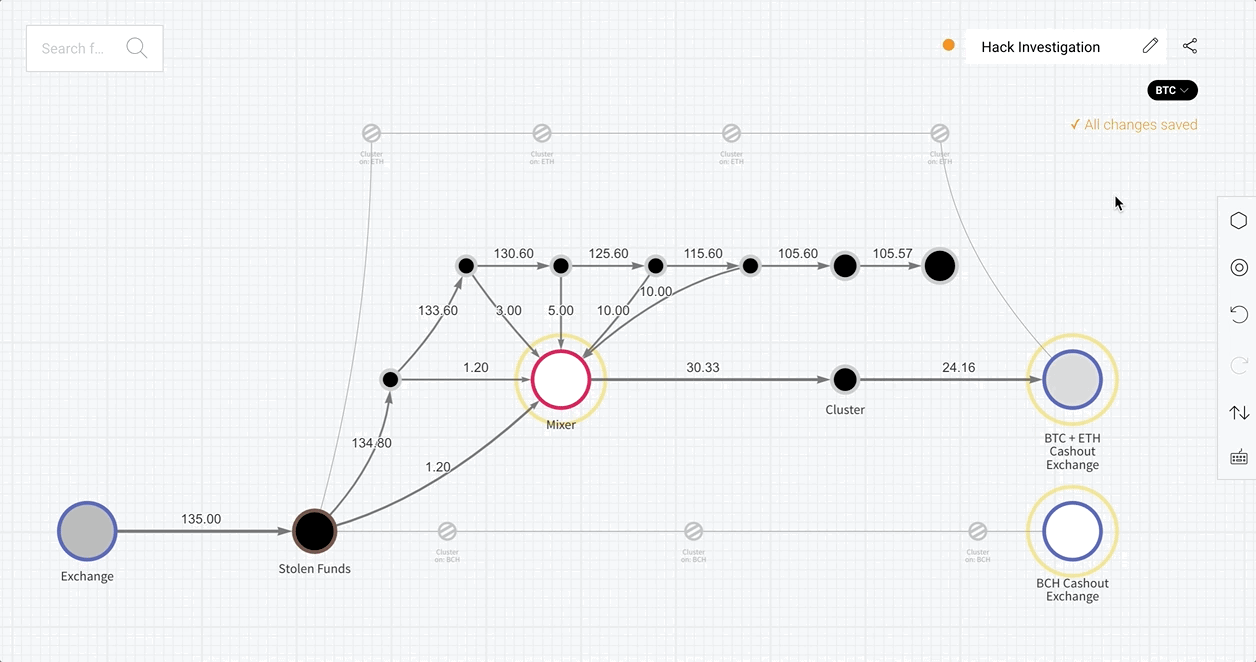
When a Reactor graph involves multiple cryptocurrencies, a dropdown menu now appears under the graph name listing assets associated with the addresses in the graph. Selecting a cryptocurrency from the menu highlights the clusters of addresses that hold or have held that asset in the past.
Clusters that have transacted in the selected asset appear brightened, while those that do not are dimmed, but all are shown in the graph. This allows users to understand the flow of specific assets within the scope of a larger investigation.
With this intuitive graphing solution, cross-chain investigations are more efficient than ever. Let’s see it in action.
Graphing the BadgerDAO Attack With Cross-Chain Investigations
In late 2021, an attacker used a compromised Cloudflare API key to inject malicious code into BadgerDAO’s DeFi application. These scripts, which functioned like a phishing lure, prompted users to allow a foreign address to operate on their tokens.
The attacker collected these approvals over several months before launching the exploit on December 2nd. Within five hours, they transferred roughly $120 million worth of 19 different tokens into addresses they controlled. They then used DeFi protocols to swap the tokens for bitcoin and ether.
After the attack, we began tracing the stolen funds. Here’s what we found out.
The attacker funded the attack with personal ether and tested the token swaps beforehand
In the first malicious cross-chain transfer, the attacker sent 0.009 Ether to the Badger vault in exchange for $51 million in Badger yVault Wrapped Bitcoin (byvWBTC). byvWBTC is a “vault deposit” token redeemable for wrapped Bitcoin (WBTC). WBTC, in turn, is a token redeemable for Bitcoin. Bitcoin—well, you know Bitcoin.
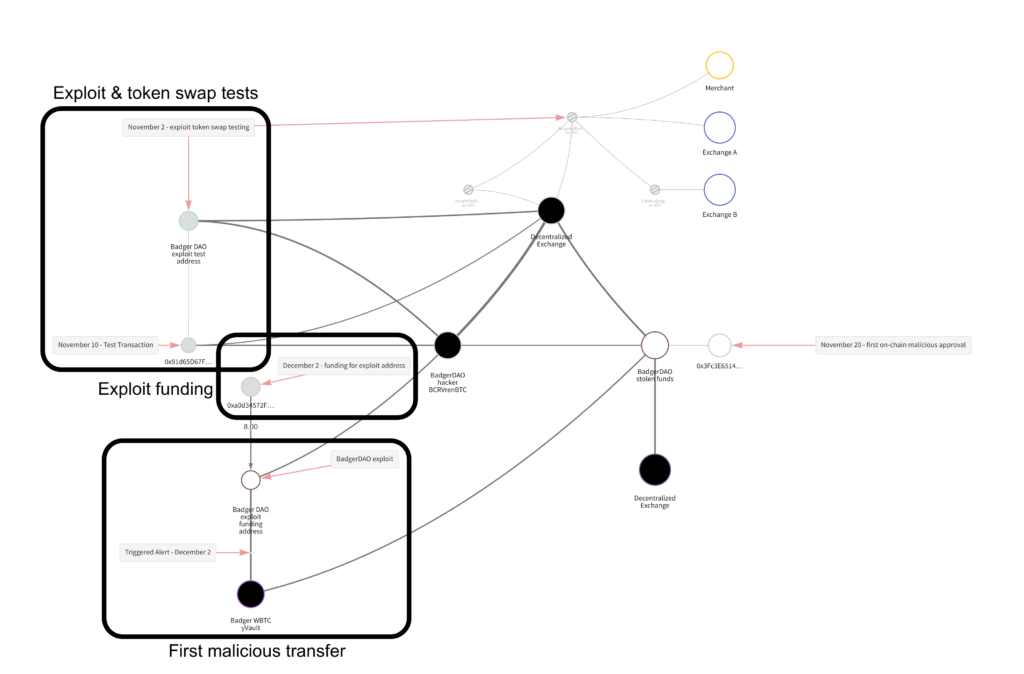
The ether was needed to pay the transaction fees for the malicious cross-chain transfers, and the attacker used their own to do so. Blockchain evidence suggests they practiced making the malicious transfers and swapping the byvWBTC for BTC months beforehand.
The token swaps occurred on multiple DeFi protocols
The attacker liquidated the stolen funds and exited via the Badger Bridge to BTC. This process involved more than a dozen cross-chain transfers on two decentralized exchanges that enabled automated token swaps without collecting Know Your Customer information.
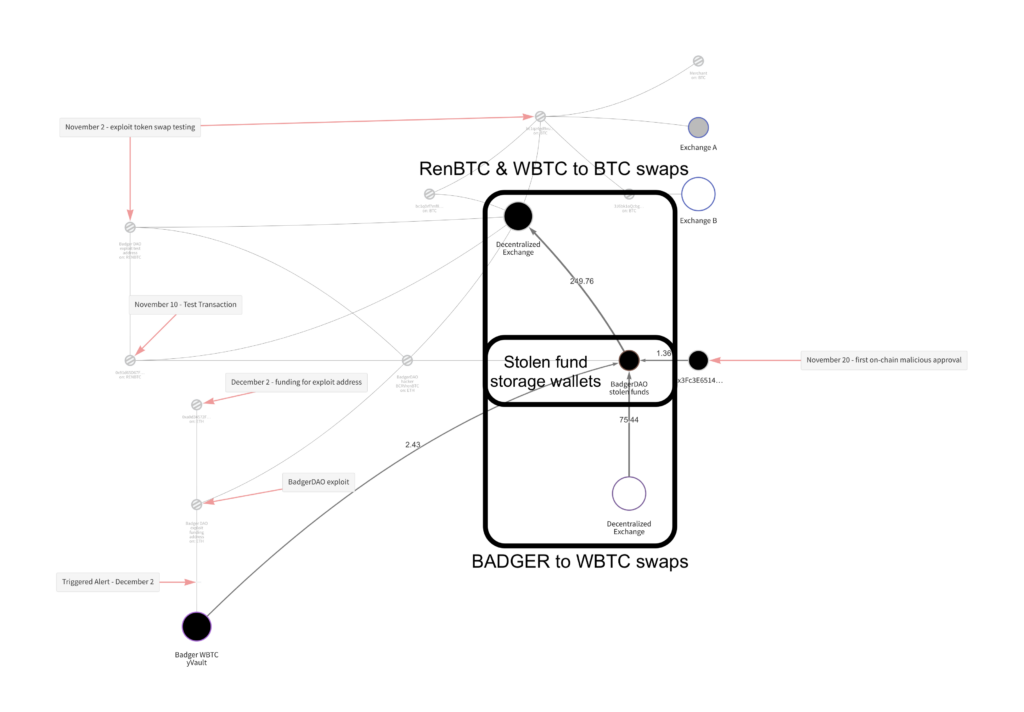
All funds remain in the “stolen funds” cluster
In the info panel below, we can see that 2,101 bitcoin and 150.9 Ether remain unlaundered in a hacker-controlled cluster.
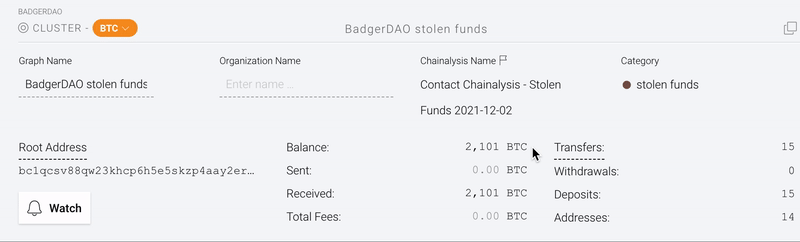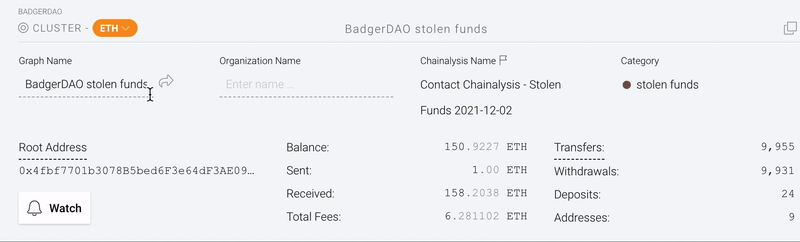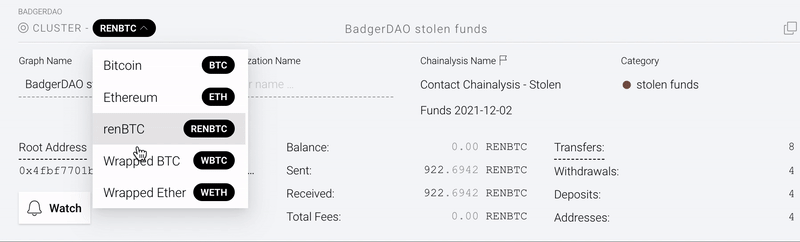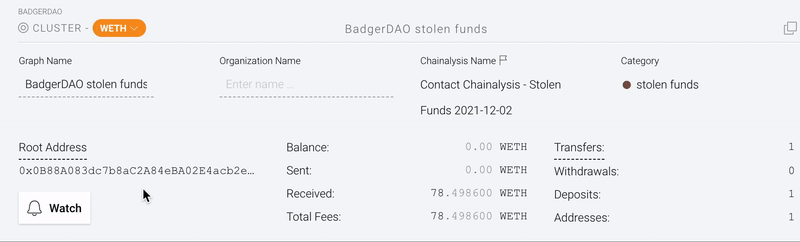
The attacker has not attempted to convert the funds into fiat currency or launder them through a mixer. (Reactor users can click the “Watch” button to receive a real-time alert whenever a flagged cluster initiates a transfer.)
The future is cross-chain
The growth of alternative blockchains— and of smart contracts that make them interoperable — is showing no signs of slowing. Cross-Chain Investigations makes it easy to navigate this complicated ecosystem by housing every case-relevant token in a single graph.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.