Governments have seized billions of dollars in cryptocurrency since Bitcoin’s creation. American agencies have seized at least $7.1 billion; London Metropolitan Police has seized half a billion; and law enforcement agencies in Latin America, Europe, and Asia–Pacific have collectively made cybercriminals forfeit billions more. Even private sector asset recovery professionals have begun to return millions to victims worldwide.
But while these forfeitures have generated headlines and compensated victims, how they’ve worked under the hood is less understood. That’s why in this brief guide, we explain:
- What happens when suspicious activity is identified by:
- What the asset forfeiture and realization process looks like
- The importance of training, expertise and third-party services
- How Chainalysis can help
Let’s dive in.
What happens when suspicious activity is identified?
The process for addressing suspicious activity on a cryptocurrency platform differs depending on whether it’s first identified by platforms or by private/public sector investigators.
By cryptocurrency platforms
Platforms like exchanges can use cryptocurrency compliance tools to monitor incoming and outgoing transactions and comply with regulatory obligations. Suspicious activity may be flagged due to how the transactions are being structured, how the value is being moved, or whether the funds’ source or destination is illicit. Most cryptocurrency businesses take one or more of the following steps when a user engages in a suspicious transaction or activity:
- Submit a suspicious activity report to FinCEN (if based in the U.S.) or equivalent required documentation (if based elsewhere)
- Request an explanation from the user
- Restrict the user from transacting larger quantities
- Temporarily freeze the user’s funds
- Ban the user from the platform
Which one (or more) of the above actions are taken varies according to the level of risk introduced by the transaction, the user’s response to any inquiries about it, the user’s previous activities, and the cryptocurrency platform’s regulatory obligations.
Screening transactions and reporting anything suspicious is particularly important when it comes to crypto, because platforms often don’t have control over incoming funds. These transfers are processed by the blockchain network and cannot be stopped; it is only once the deposit has been processed onto an address under the platform’s control that they have any ability to act. So while they can’t prevent payments from, for example, a terrorist financing campaign, they can prevent those funds being cashed into traditional money or transferred elsewhere by the account holder. Furthermore, assuming they have proper KYC/AML procedures in place, they can report the account holder and their activity.
Being able to demonstrate how an organization’s platform screens for and responds to suspicious transactions is one of the best ways to protect its reputation. For more on this subject, see our blog on sanctions compliance strategy.
By private sector investigators
Those who wish to track down and recover their cryptocurrency can also turn to private investigators, lawyers, forensic accountants and enforcement professionals who specialize in returning assets to victims. In some cases businesses have turned to insolvency professionals to investigate and recover assets, such as Grant Thornton’s Cryptopia case.
The process of investigating is much the same in terms of data collection, use of blockchain analytics, and requests for information. However, we are seeing that many cases have subsequently been put before the civil courts, which have made both typical asset preservation orders and pragmatic new approaches to reflect the decentralized, pseudonymous nature of the blockchain.
To date, courts have granted:
- Orders confirming the status of crypto as property to allow the usual remedies available for securing and recovering property to be extended to crypto (including at least in the UK, US, Canada, BVI, New Zealand and Singapore);
- Asset Preservation Orders and Proprietary Injunctions (over specific assets), even against unknown persons where funds have been tracked to a service but the identity of the owner remains unknown;
- Worldwide freezing orders (to freeze all assets of a person who is likely to be enforced against at the end of the proceedings);
- Disclosure orders requiring information about transactions and the identity of account holders. In the U.K., this includes under Bankers Trust Orders (against financial institutions) and Norwich Pharmacal Orders (requiring an innocent third party to provide information where they have unknowingly become involved);
- Service outside of the jurisdiction; to allow orders made in one country to be served in other countries (which is very important given the borderless nature of crypto).
There has been a raft of cases showing how assets can be identified and secured pending trial; however, save for insolvency of exchanges, such as Mount Gox, crypto recovery cases in the private sector only started being reported from around 2018. Many of these settle, or are resolved quickly if there is no contest, presumably where the defendant does not want to abandon any anonymity they have preserved. But we are also now starting to see the first few cases reach the enforcement and recovery stage, including through the use of third party debt orders.
By public sector investigators
When law enforcement investigators have reason to believe that a suspect is engaging in illicit cryptocurrency activity, typically after reports from victims or crypto platforms, they usually do the following:
- Gather relevant cryptocurrency addresses, transaction details, counterparties, and other OSINT;
- Use blockchain analysis tools to determine the nature, origin and destination of the funds. This includes whether they’re deposited at any identified exchanges, whether they’re connected to unlawful activity, and how they are being spent and moved;
- Subpoena/Request information from the identified cryptocurrency business(es) with whom the suspect(s) has transacted and may have an account(s).
Investigators may find these cryptocurrencies were derived from unlawful activities such as narcotics sales, ransomware, frauds or scams. They may also find the cryptocurrencies were commingled with other legitimate sources of cryptocurrency, or that the cryptocurrency transactions are themselves legitimate but that the fiat money used to purchase them was derived from criminal activity.
If the subsequent movement of funds is designed to conceal the true nature and origin of the funds, this may amount to money laundering, making these funds potentially subject to seizure in many jurisdictions.
How does the asset forfeiture & realization process work?
When a sufficient case has been built for the suspect’s indictment and arrest, investigators often coordinate with the business where the digital assets are held to either transfer them into a government-controlled wallet or maintain an indefinite freeze. In some cases, however, the assets remain in the suspect’s personal wallet; they may agree to turn over the funds in exchange for reduced prison time.
Seized cryptocurrencies are typically held in this way until a court verdict is reached. If the defendant is acquitted, the assets are returned; if convicted, the asset forfeiture is part of the defendant’s sentencing. In the event of a successful conviction, a separate, ancillary proceeding is initiated to determine all third-party ownership interests in the assets the government seeks to forfeit.
When all ownership interests are addressed, the remaining funds are auctioned for fiat currency and allocated to the agencies that participated in the case. These assets are typically earmarked for restoration to identified victims or forfeiture to government treasuries. Depending on the jurisdiction, some of the funds may also go towards community-based revitalization programs, such as drug abuse treatment, public housing, and job skills training.
The importance of training, expertise and third-party services
As crypto has become more prevalent, increasing numbers of public/private sector investigators need access to the resources necessary to confidently identify and seize cryptocurrencies. This includes searching for evidence of crypto usage on individuals’ electronic devices, computers, hardware wallets, software applications, file systems, text messages, or even just paper notes. These devices may store valuable cryptocurrency information like private keys, seed phrases, bitcoin addresses, and transaction hashes that can be traced in Reactor and physically seized.

Devices, applications, and documents indicative of cryptocurrency activity.
Training on evidence handling is also crucial. For example, investigators need to know how to safely store seed phrases and private keys. They also need to know how to set up either a non-custodial wallet or a custodial account on a trusted cryptocurrency platform.
How Chainalysis can help
Law enforcement agencies and private investigators need a safe way to track, store, and sell the cryptocurrency they’ve seized. That’s why we and our trusted partners have built a secure end-to-end solution to track, handle, and realize forfeited cryptocurrencies.
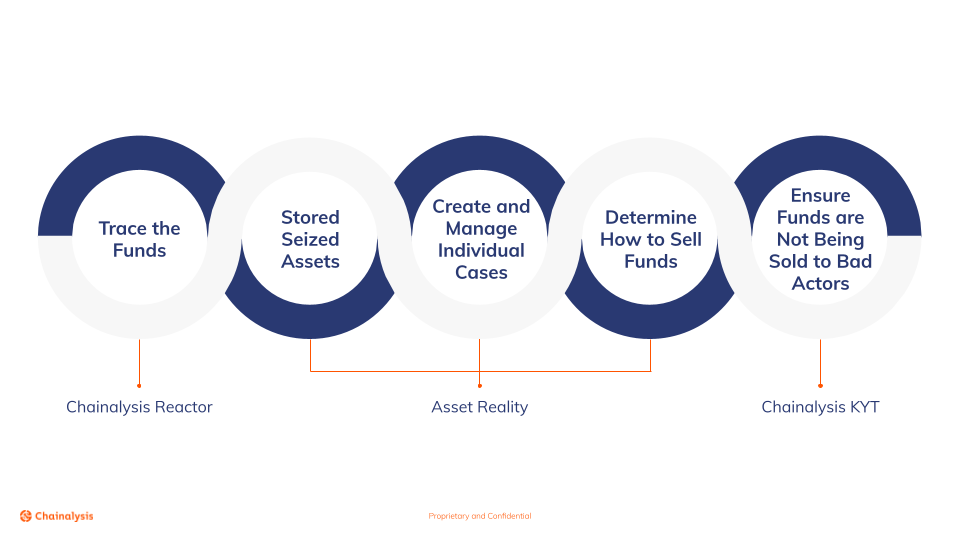
This begins with Chainalysis Reactor – for investigators to build cases – and ends with Chainalysis KYT – for sellers to ensure that the forfeited funds are sold in compliance with crypto AML and KYC policies. Meanwhile, our trusted partners in between can help you store, manage, and find customers for your cryptocurrency.
Learn more about Chainalysis’s products for insolvency practitioners, investigators, and compliance teams.
About the author: Dani Haston is Chainalysis’s Global Head of Asset Management. A practicing lawyer for 16 years, Dani has acted on behalf of government bodies, local authorities, and private sector clients on insolvency, asset recovery, and international civil fraud. She joined Chainalysis to help organizations of all stripes bring crypto within the scope of assets that they can identify and obtain value from.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
All trademarks, logos and brand names are the property of their respective owners. All company, product and service names used in this website are for identification purposes only. Use of these names,trademarks and brands does not imply endorsement.