This blog is an excerpt from the Chainalysis 2020 Crypto Crime Report. Click here to download the full document!
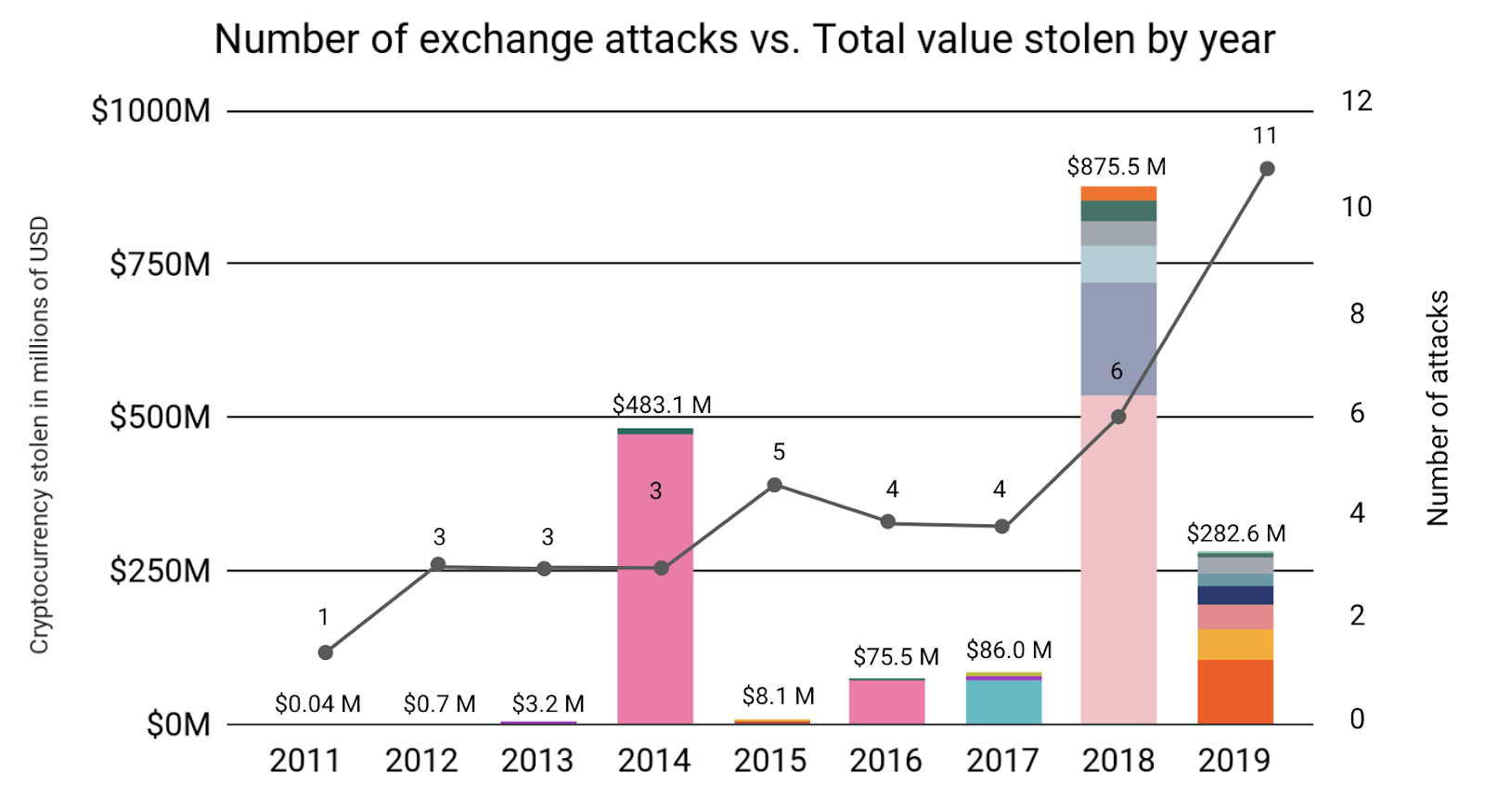
2019 saw more cryptocurrency hacks than any other year. But of the 11 attacks that occurred this year, none of them came close to matching the scale of major heists such as last year’s $534 million Coincheck hack, or the $473 million Mt. Gox hack in 2014. Therefore, the total amount stolen from exchanges dropped sharply to $283 million worth of cryptocurrency despite the increased number of attacks.
Allow us to explain how we arrived at our final count of 2019 exchange attacks, given that other sources in the media and elsewhere may report different numbers:
- We counted both hacks involving exploitation of technical vulnerabilities and attacks conducted through social engineering or other forms of deception. (A note on terminology: All hacks are attacks, but not all attacks are hacks. Hacks refer specifically to cases where a bad actor exploits a technical vulnerability in a piece of software, while attacks can include other, less technically sophisticated actions, such as phishing attacks that trick victims into downloading a malicious piece of software.)
- We only counted attacks that allowed bad actors to access funds belonging to exchanges, and not payment processors, wallet providers, investment platforms, or other types of services.
- We didn’t count exchange exit scams or cases of users exploiting an exchange error, such as the pricing discrepancy that nearly allowed a Synthetix user to net over $1 billion in faulty trades.
- We only included attacks in which the amount stolen was measured and publicly confirmed by multiple sources. That means we didn’t include incidents in which exchanges’ user data was compromised, but no cryptocurrency was stolen. We also excluded hacks that have been privately reported to us, but are confident that including them wouldn’t significantly skew the data we analyze here.
Under these constraints, nearly all of the hacks we didn’t include were on smaller exchanges for relatively low amounts of cryptocurrency. Our estimates of the total amount in exchange hacks are therefore likely a lower boundary, but one we believe isn’t far off from the actual total.
2019 Exchange Attacks Quantified
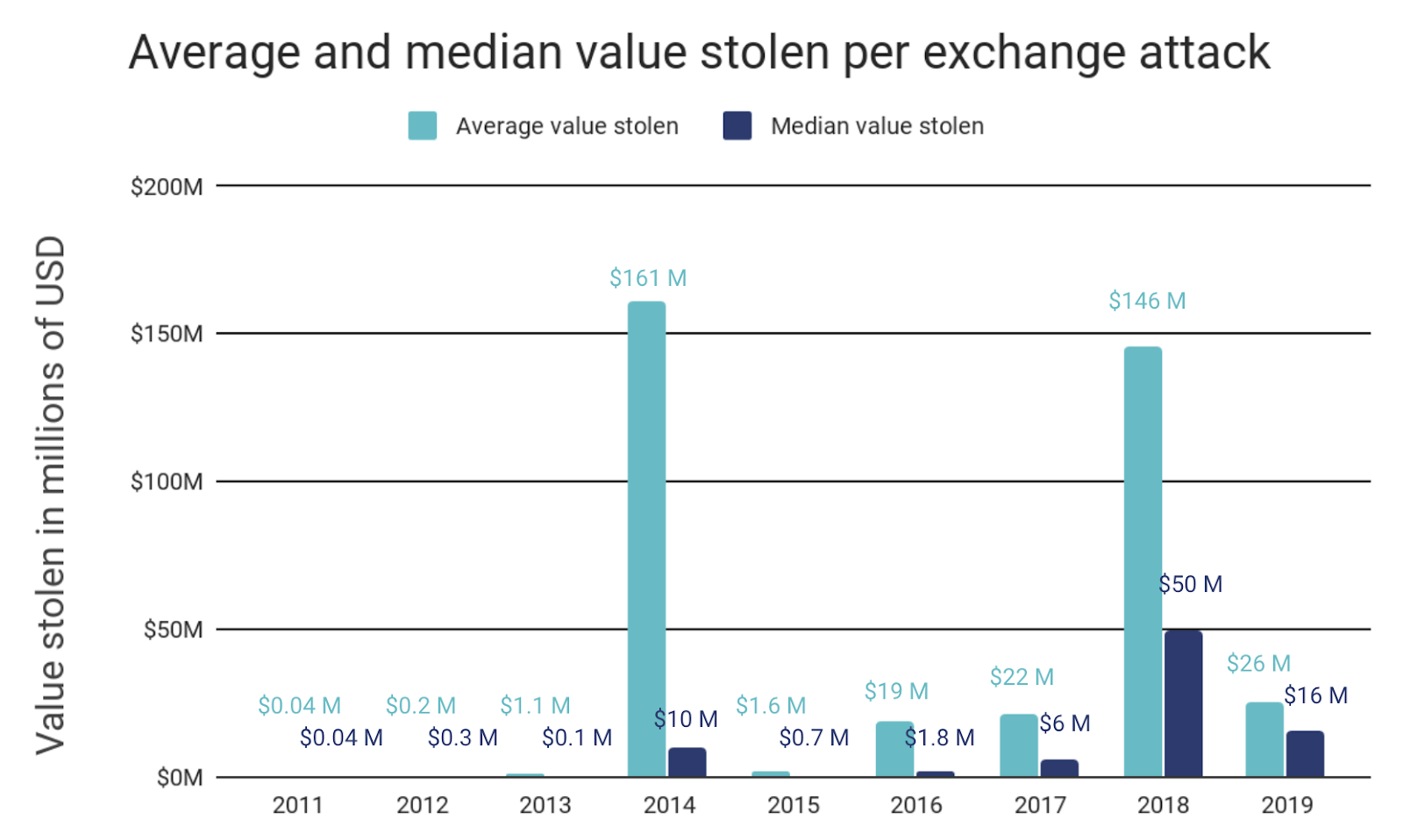
With no hacks taking in more than the $105 million stolen from Coinbene, both the average and median amount stolen per hack fell substantially in 2019, after having risen each of the three preceding years. Only 54% of the hacks we observed in 2019 took in more than $10 million, compared with all hacks in 2018. While the increase in the number of individual hacks should be concerning, the data indicates that exchanges have gotten better at limiting the damage any one hacker can do.
Where do funds go after the attacks?
Using blockchain analysis, we can analyze the movements of funds stolen in hacks to get a sense of how hackers liquidate funds. Below, we see the most common destinations for funds stolen in exchange attacks broken down by year.
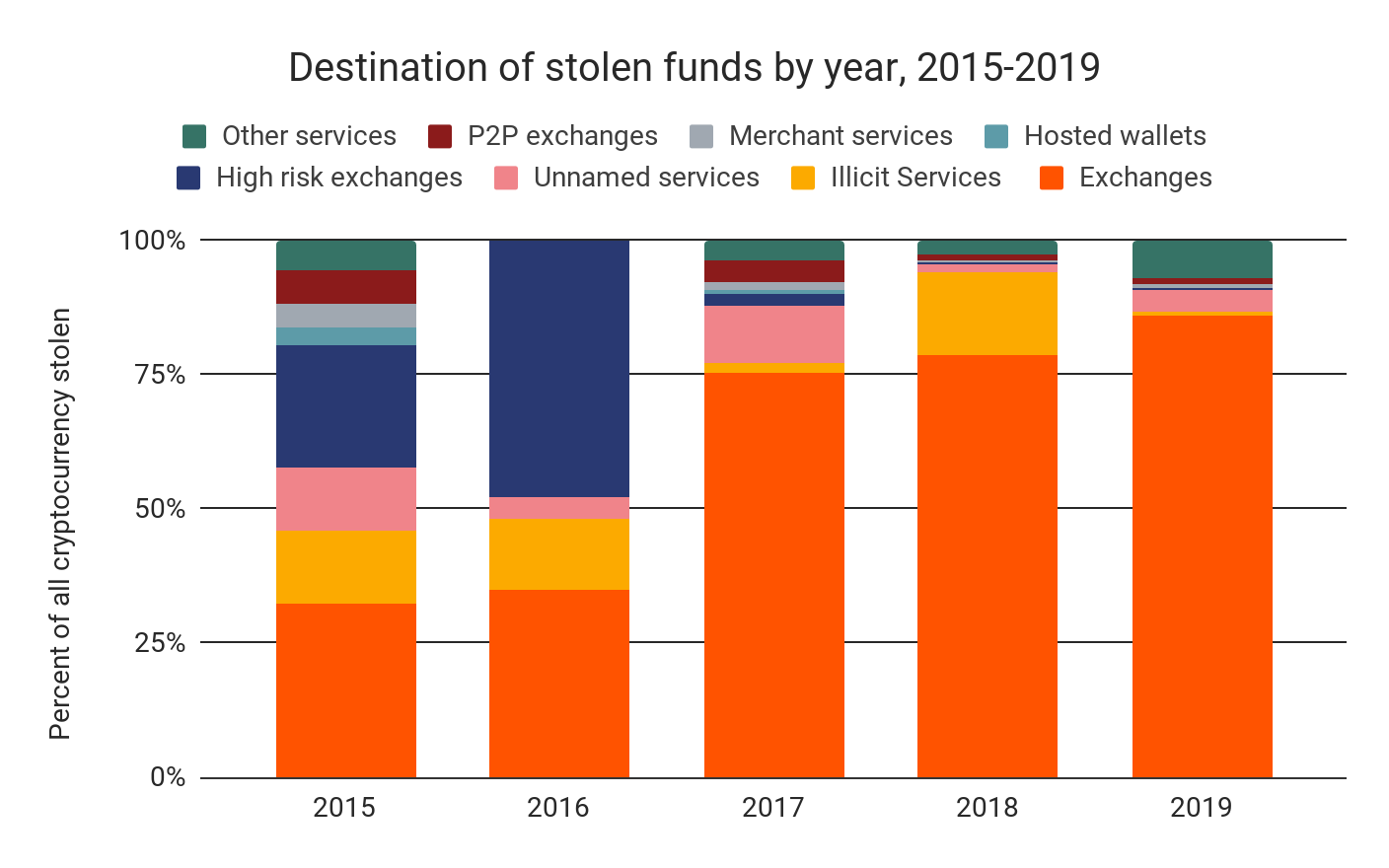
The majority of funds stolen in exchange attacks end up being sent to other exchanges, where they’re likely converted into cash. However, a substantial portion of funds sit unspent, sometimes for years. In those cases, there may still be an opportunity for law enforcement to seize the stolen funds. And as we’ll explore later, a small but significant — and, in 2019, increasing — portion of all funds stolen are passed through third-party mixers or CoinJoin wallets to obscure their illicit origins. Any mixed funds on the chart above, however, are categorized according to their final destination after mixing took place.
Hackers respond to exchanges’ security measures
Exchanges have taken strides to better protect customers’ funds from hacks and the sharp decreases in amount lost per hack indicate they’ve been successful. Many exchanges now keep a lower percentage of funds in less secure hot wallets, require more withdrawal authorizations, and monitor transactions more closely for suspicious activity so as to catch hacks earlier. We also know from the hacks we’ve helped investigate in 2019 that exchanges’ increased willingness to come forward when attacked and share details with the rest of the cryptocurrency community have made it easier to track down stolen funds.
But at the same time, the most prolific hackers have also grown more sophisticated, both in how they carry out hacks and in how they launder their stolen funds afterwards. While this isn’t a positive development, it suggests that the measures adopted by exchanges are effective enough to force hackers to adapt in the first place. And as we’ll show you, there are concrete steps exchanges and law enforcement can take to counter hackers’ new tactics.
Let’s explore some of the new tactics exchange hackers have adopted by analyzing the activity of one high-profile cybercriminal organization.
How Lazarus Group became more advanced in 2019
Lazarus Group is an infamous cybercriminal syndicate linked to the North Korean government. Considered an advanced persistent threat by cybersecurity experts, Lazarus is widely believed to be behind the 2014 hack of Sony Pictures and 2017 WannaCry ransomware attacks, as well as a number of cryptocurrency exchange attacks. We can also reveal that Lazarus Group is the organization we dubbed “Beta Group” when we analyzed their exchange hacking activity in last year’s Crypto Crime Report.
In 2019, Lazarus Group made three key changes to its hacking and money laundering strategies:
- More sophisticated phishing ploys. Lazarus Group has historically relied on social engineering to attack exchanges, typically fooling employees into downloading malicious software that gives Lazarus access to users’ funds. But in an exchange attack this past year, Lazarus took this strategy a step further and executed one of the most elaborate phishing schemes we’ve seen to gain access to users’ funds.
- Increased use of mixers and CoinJoin wallets. In 2019, hackers have more often sent funds stolen from exchanges through mixers or, to be more specific in the case of Lazarus Group, CoinJoin wallets. Mixers obfuscate the path of funds by pooling cryptocurrency from multiple users, and giving each one back an amount from the pool equal to what they initially put in, minus a 1-3% service fee. Everyone ends up with a “mix” of the funds everyone else put in, which makes it more difficult to connect the inputs to an output on the users’ transactions. Many criminals use mixers to hide the source of illicit cryptocurrency before moving it to other services. CoinJoin wallets (named for the underlying CoinJoin protocol), such as Wasabi Wallet, accomplish the same thing by providing a wallet service that allows multiple users to trustlessly join their payments into a single transaction with multiple recipients.
- Faster liquidations. We’ve also seen hackers like Lazarus move their funds to exchanges and other services for liquidation in shorter amounts of time than in 2018. This trend could suggest that hackers in 2019 improved their money laundering capabilities, or that they’re simply prioritizing faster access to stolen funds more so than in 2018.
Let’s look at examples of how Lazarus has employed these new tactics.
How Lazarus Group used a fake company as phishing bait
In March of 2019, hackers breached the Singapore-based DragonEx exchange, taking roughly $7 million worth of various cryptocurrencies, including Bitcoin, Ripple, and Litecoin. DragonEx responded quickly, announcing on various social media platforms that it had been hacked and releasing a list of 20 wallet addresses to which its funds had been transferred. That allowed other exchanges to flag those wallets and freeze accounts associated with them, making it harder for the attackers to move the funds. DragonEx was also quick to contact Chainalysis and enlist our help alongside legal authorities.
While the DragonEx hack was relatively small, it was notable for the lengths Lazarus Group went in order to infiltrate the exchange’s systems in a sophisticated phishing attack. Lazarus created a fake company claiming to offer an automated cryptocurrency trading bot called Worldbit-bot, complete with a slick website and social media presence for made up employees.
Lazarus even went so far as to build a software product resembling the trading bot they claimed to be selling. The key difference, of course, was that the program contained malware giving the hackers access to the computer of anyone who downloaded it. Lazarus Group hackers pitched a free trial of the software to DragonEx employees, eventually convincing someone to download it to a computer containing the private keys for the exchange’s wallets. From there, the hackers were able to make off with millions.
Whereas most phishing attempts rely on little more than an email or small-scale website, Lazarus Group’s fabricated Worldbit-bot company is on another level of sophistication. It reveals the time and resources Lazarus has at its disposal, as well as the deep knowledge of the cryptocurrency ecosystem necessary to successfully impersonate legitimate participants.
Increased mixer usage and faster cashouts highlight changes to Lazarus’ money laundering strategy
When we analyzed their 2018 post-hack money laundering transactions for last year’s Crypto Crime Report, we found that Lazarus Group didn’t use sophisticated money laundering techniques like mixers to “clean” and withdraw stolen cryptocurrency quickly like other prominent hacking groups. Instead, they tended to park funds in a wallet, wait 12 to 18 months, and suddenly move all the funds to a low-KYC exchange when the coast seemed clear.
We concluded that this was due to Lazarus’ motivations being primarily financial. Whereas other prominent hacking groups appear more interested in causing chaos for targets and avoiding detection, Lazarus’ behavior indicated a singular focus on turning stolen cryptocurrency into cash, even if it meant waiting for long periods of time and moving them to an exchange in a way that’s relatively easy to trace. The U.S. government has reported that North Korea uses funds from exchange hacks and other financial crimes to fund its weapons of mass destruction (WMD) and ballistic missile programs, supporting the theory that money is Lazarus’ primary goal.
While we don’t claim to know if Lazarus’ motivations changed in 2019, we do know that their modus operandi for moving and cashing out funds stolen in exchange hacks did change. First, we see a much higher percentage of funds they steal moving to mixers.
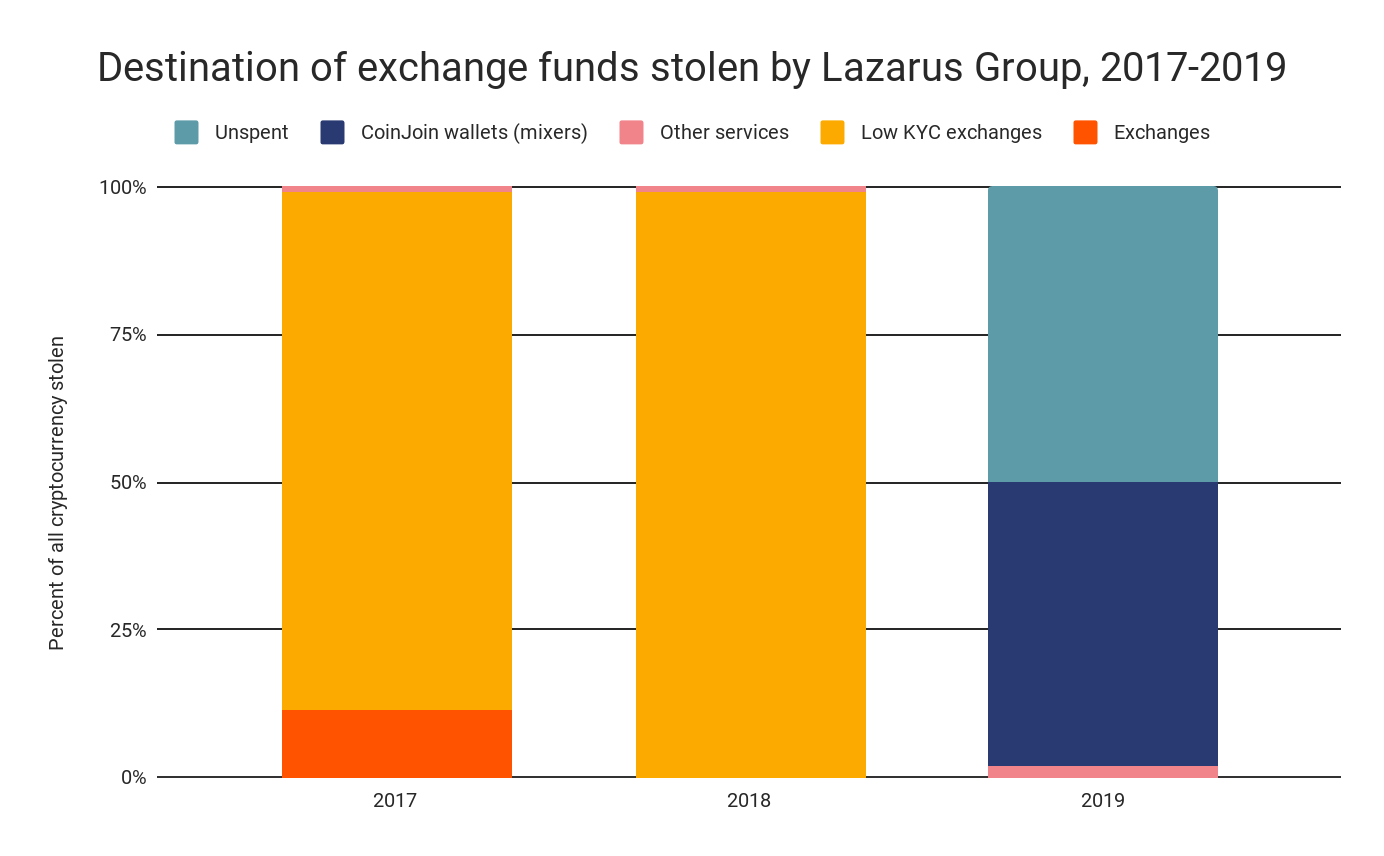
98% of all funds Lazarus stolen from exchanges in 2018 ended up being moved to exchanges, all of which have low KYC requirements, while none went to mixers or CoinJoin wallets. However, in 2019, 48% of funds stolen by Lazarus moved to CoinJoin wallets, while 50% sit unspent in the hackers’ original wallet.
We can see this below using Chainalysis Reactor to compare transaction activity associated with a Lazarus hack from 2018 with one from 2019.
Chainalysis Reactor: 2018 Lazarus Group exchange hack
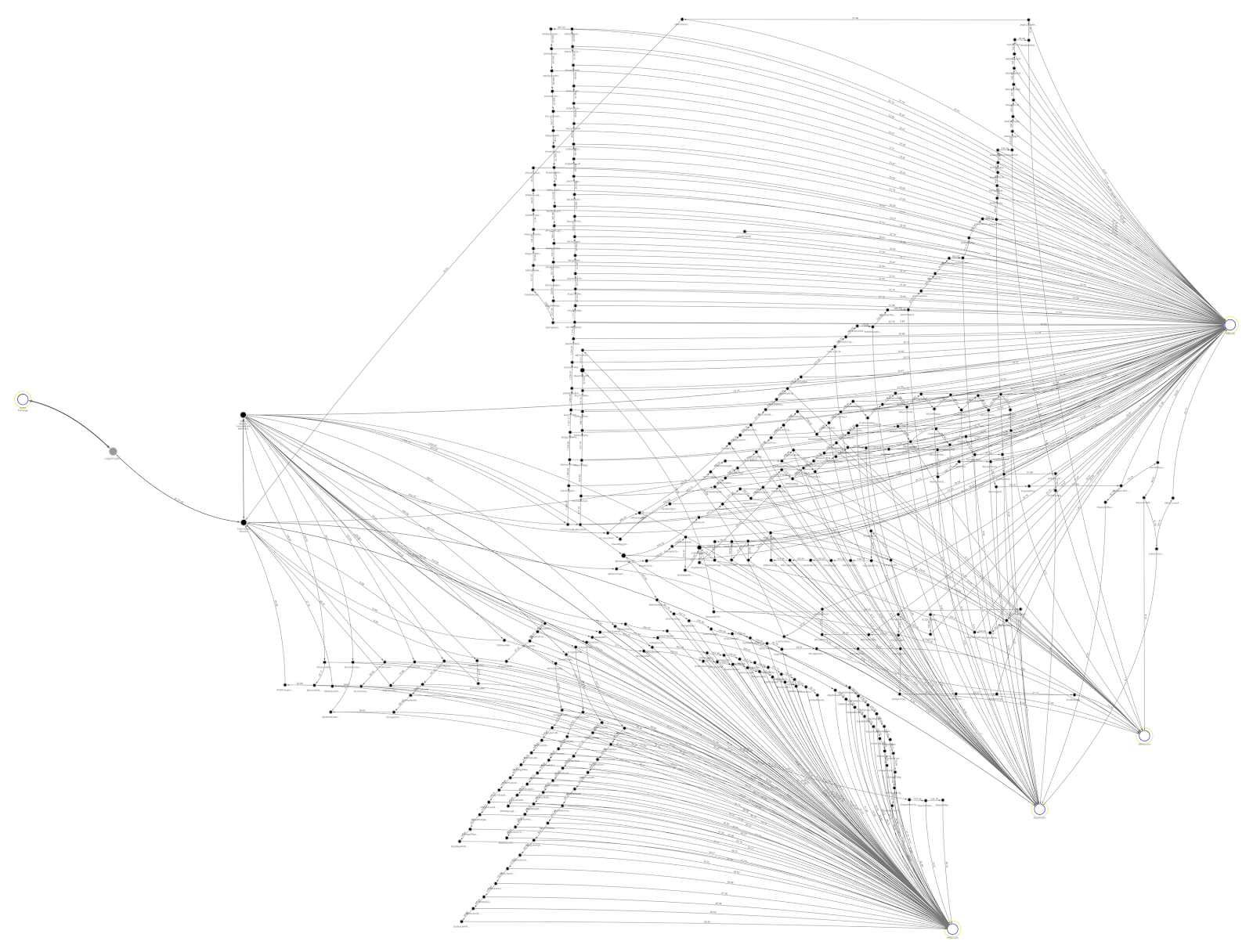
Above, we see how Lazarus moved stolen funds following one of its 2018 exchange hacks. While it may look complicated due to the large number of transactions, it’s actually very simple. Funds leave the Victim Exchange wallet on the left, move through two intermediary wallets, and then are dispersed to four different exchanges on the right. The many hops in between represent unspent change moving from a wallet to an exchange. While the funds’ path may be long, it’s relatively easy to follow.
Chainalysis Reactor: 2019 Lazarus Group exchange hack
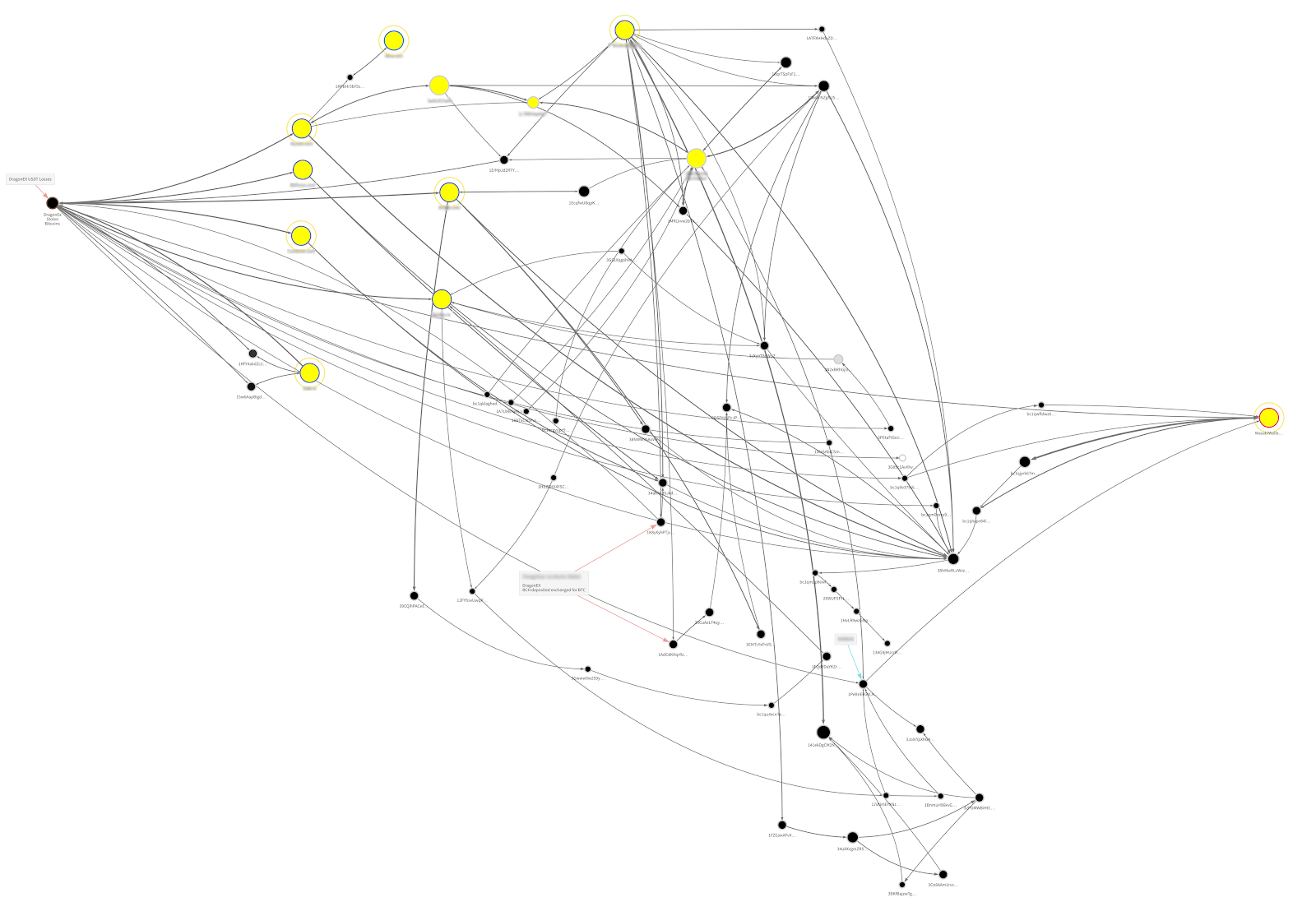
The Reactor graph showing how Lazarus moved funds following the 2019 DragonEx hack is much more complicated. In this case, stolen altcoins like Ethereum and Litecoin were moved to exchanges and swapped for Bitcoin. Next, they shuffle the Bitcoin withdrawn from exchanges between a variety of local wallets, before ultimately moving it to a Wasabi Wallet on the far right to mix the funds via the CoinJoin protocol.
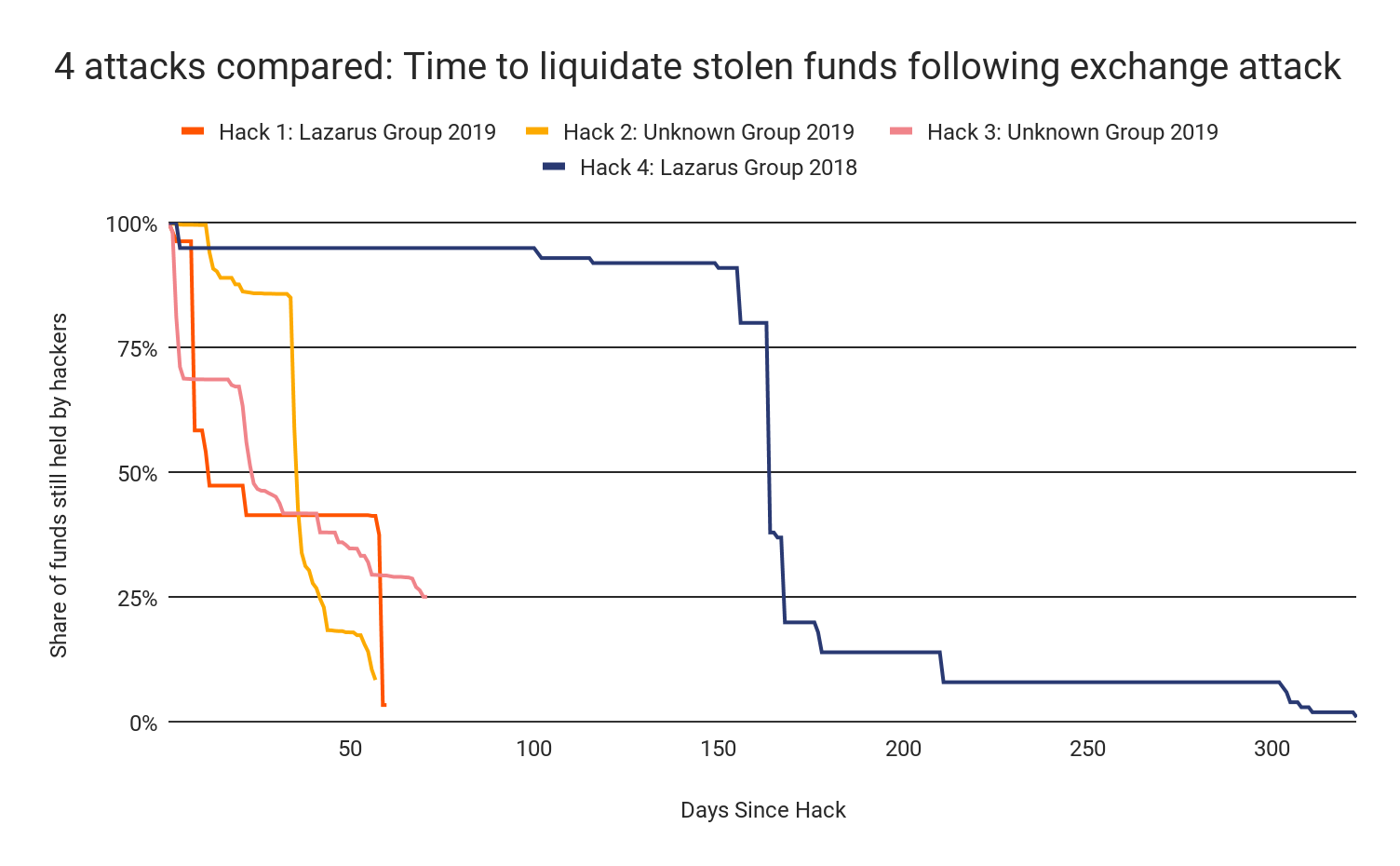
Lazarus Group also moved stolen funds to services where they can be liquidated — mostly exchanges — much faster this year. In 2018, Lazarus took as long as 500 days to move funds from their initial private wallet to a liquidation service, and never did so in under 250 days. But that changed drastically in 2019. Nearly all of the funds stolen in both hacks attributed to Lazarus were moved to liquidation services in under 60 days, though some still remain unspent. Hacks attributed to other groups followed this trend as well.
Lazarus’ growing sophistication and speed in laundering stolen cryptocurrency puts more pressure on intelligence agencies and exchanges alike to move quickly when cybercriminals attack exchanges.
Exchanges need to keep prioritizing security
Exchanges have raised the bar on anti-hacking security in the last few years, but the subsequent advancements of groups like Lazarus show that they can’t afford to rest on their laurels. They need to remain vigilant and continue building on the improvements they’ve already made to stay one step ahead. We recommend exchanges continue putting guard rails in place to ensure suspicious transactions are flagged before completion and take steps to prevent employees from downloading malicious software that could compromise their network and give hackers access to the exchange’s private keys. In the event exchanges are hacked, they need to report it to law enforcement immediately and provide key information such as addresses to which stolen funds have moved.
Aside from protecting themselves from being hacked, exchanges also have a responsibility to make sure criminals aren’t using them to cash out funds from other exchanges that have been hacked. We suggest that exchanges treat large deposits — or high volumes of small deposits in a short amount of time — from mixers or CoinJoin wallets with increased suspicion. While there are legitimate uses for mixers, the data makes it clear that they’re increasingly being utilized by hackers to obfuscate the path of stolen funds prior to cashing out. Exchanges can likely stop some of these cashouts and help law enforcement claw back stolen funds by halting suspicious transactions from mixers. Binance has already begun doing this, and we think their model could be a useful example for other exchanges to follow.
Finally, we believe that increased cross-border cooperation between law enforcement agencies can go a long way towards mitigating exchange hacks. If financial intelligence units (FIUs) around the world can swiftly share the information they get from exchanges upon being hacked, they may be able to freeze funds before hackers are able to move them to a mixer or low-KYC exchange.
This blog is an excerpt from the Chainalysis 2020 Crypto Crime Report. Click here to download the full document!
