In blockchain analysis, the best way to assess the risk of a cryptocurrency address or group of linked addresses (e.g., a wallet) is to analyze the other addresses with which it has transacted. If many of those addresses are themselves linked to illicit activity, then one can conclude that the initial address carries more risk. We call this concept exposure, meaning the types of addresses and services to which the target address has been exposed. Chainalysis Reactor aggregates this information for individual cryptocurrency addresses, wallets, and services, and displays it in exposure wheels, which express the address’ total exposure as an explanatory pie chart.
The GIF below shows a large international exchange’s exposure wheels as an example — on the left we see exposure from the receiving side, meaning a breakdown of the sources of funds received by the exchange, and on the right we see sending exposure, which is a breakdown of where funds sent from the exchange have gone. Exposure categories in Reactor include services like exchanges (some of which are broken out further into sub-categories such as P2P exchanges) and merchant services providers, as well as illicit categories like darknet markets, or even wallets we know to be associated with exchange hacks and other forms of criminal activity.
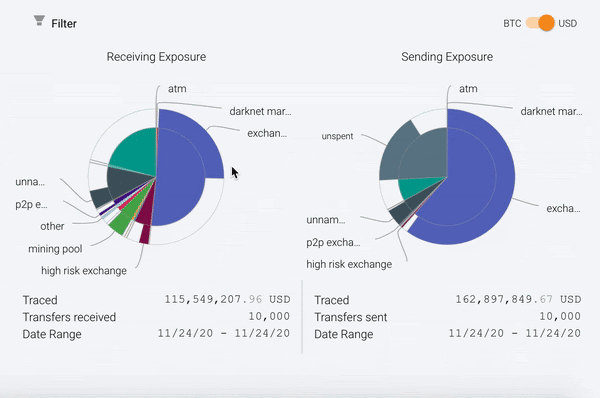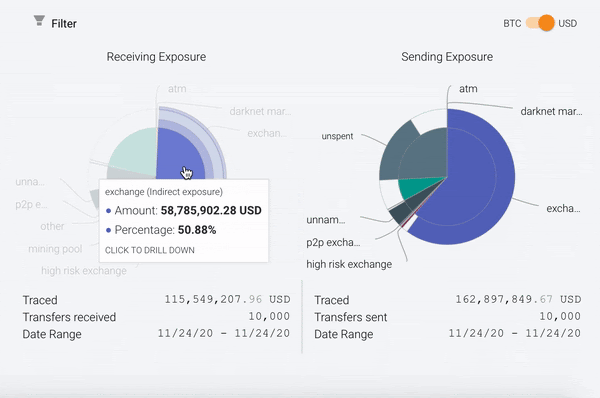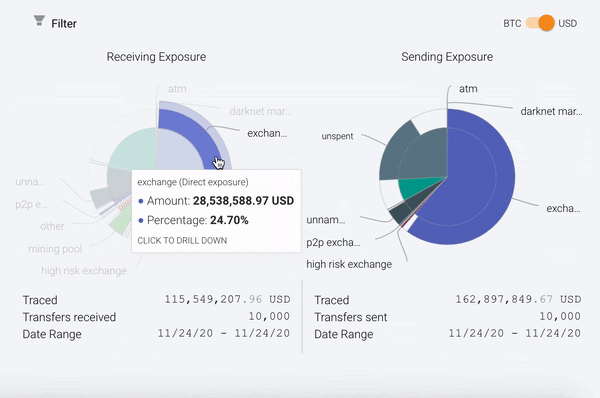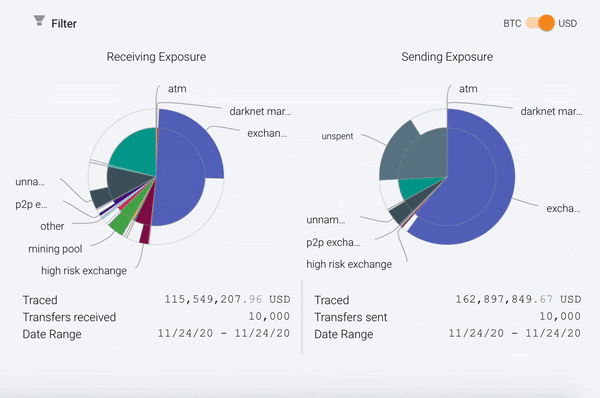
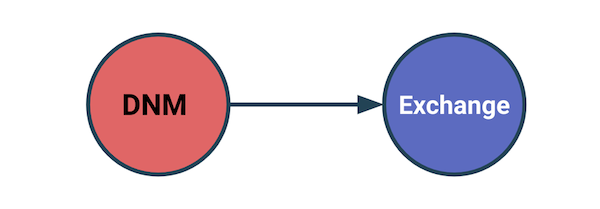
However, you’ll also notice that Reactor measures two types of exposure: direct exposure, represented by the outer ring of the exposure wheel, and indirect exposure, represented by the inner portion. Direct exposure is easy to explain: it represents services or other entities that are direct counterparties of the target address across any of its transactions. Indirect exposure, on the other hand, is a bit more tricky. Below, we’ll explain what it is and why it’s critical to robust blockchain analysis.
Indirect exposure explained
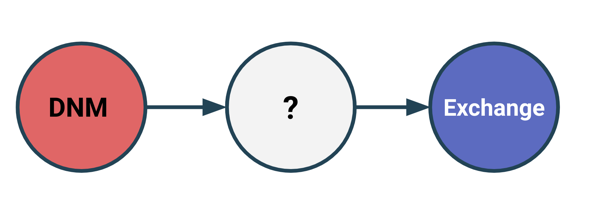
Indirect exposure measures the services and entities that make up the origins or destinations of funds in the target address’ transactions in cases where there are non-service addresses between the target address and those services or entities. In other words, imagine a target address sends funds to another address that isn’t attributed to a service or other identified entity in Chainalysis’ dataset. In that case, Reactor automatically follows the funds until they reach an attributed service or entity, and counts that service or entity in the target address’ indirect exposure. We use services as the “stopping point” for when to include an address in indirect exposure because tracing funds through a service usually isn’t possible using blockchain analysis. Once a user deposits funds at a service like an exchange, the service itself moves the funds between its internal wallets, so we can no longer use blockchain analysis to track them as if the user is controlling them.
Indirect exposure is a unique benefit to cryptocurrency due to the nature of distributed ledger technology. Thanks to blockchain transparency, crypto compliance teams can better understand the origin of funds. This can be difficult in traditional finance, where incoming funds may have moved through multiple financial institutions, with the recipient institution having only a view of transactions processed through their institution.
With cryptocurrency, users can transfer funds directly to exchanges or other services from self-hosted wallets, where they’re often not subject to typical compliance standards and are directly under the user’s control. Furthermore, it’s easy for users to set up as many self-hosted wallets as they want, which can act as a buffer between their wallet or exchange account, and any illicit services they interact with. This is a common tactic that cybercriminals often use in an effort to obfuscate their activity and make tracing harder. That’s why Reactor’s indirect exposure calculations account for all services and entities that ultimately receive or send funds to or from the target address, no matter how many intermediary non-service addresses— or “hops,” as they’re colloquially known — are in between.
Peel chains illustrate why it’s important to account for every hop. A peel chain is a transaction pattern commonly seen in blockchain analysis, in which there appear to be many intermediary addresses between a target cluster and another cluster of interest, such as a service or illicit entity. In reality though, those intermediary addresses are part of the user’s original wallet, and are created automatically to receive the leftover change that results from certain transactions. Indirect exposure is crucial here, as it can alert investigators to examine a wallet or address’ transactions more closely, allowing them to spot peel chains that would otherwise conceal illicit activity.
We see an example of this in the Reactor graph below.
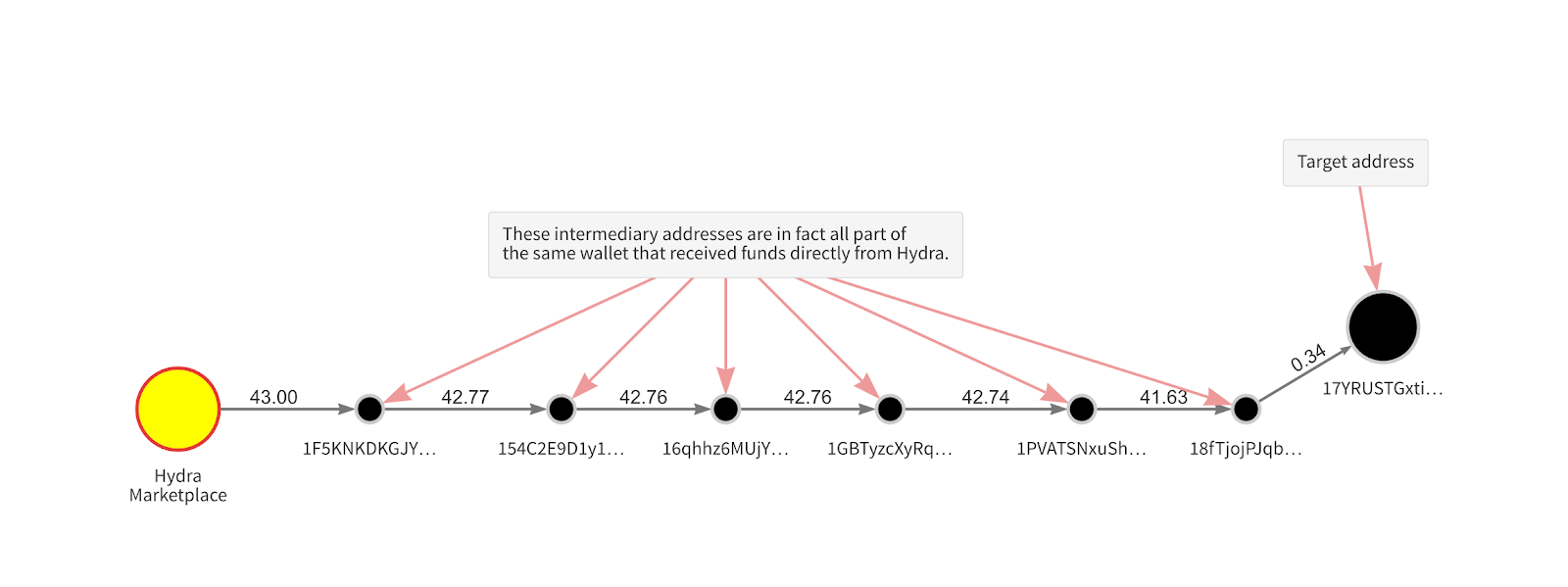
Imagine you’re investigating the address “17YRUST…” seen in the upper right-hand corner. There are seven intermediary addresses between the target address and the popular darknet market Hydra. You might initially assume that because enough intermediaries have handled the funds since they came from Hydra, the target address must be safe. But further analysis would reveal that this is a peel chain, and that in reality there’s only one wallet between Hydra and the target address. Once you merge those addresses to accurately represent the fact that all of them are in the same wallet, your graph makes the real story more apparent.
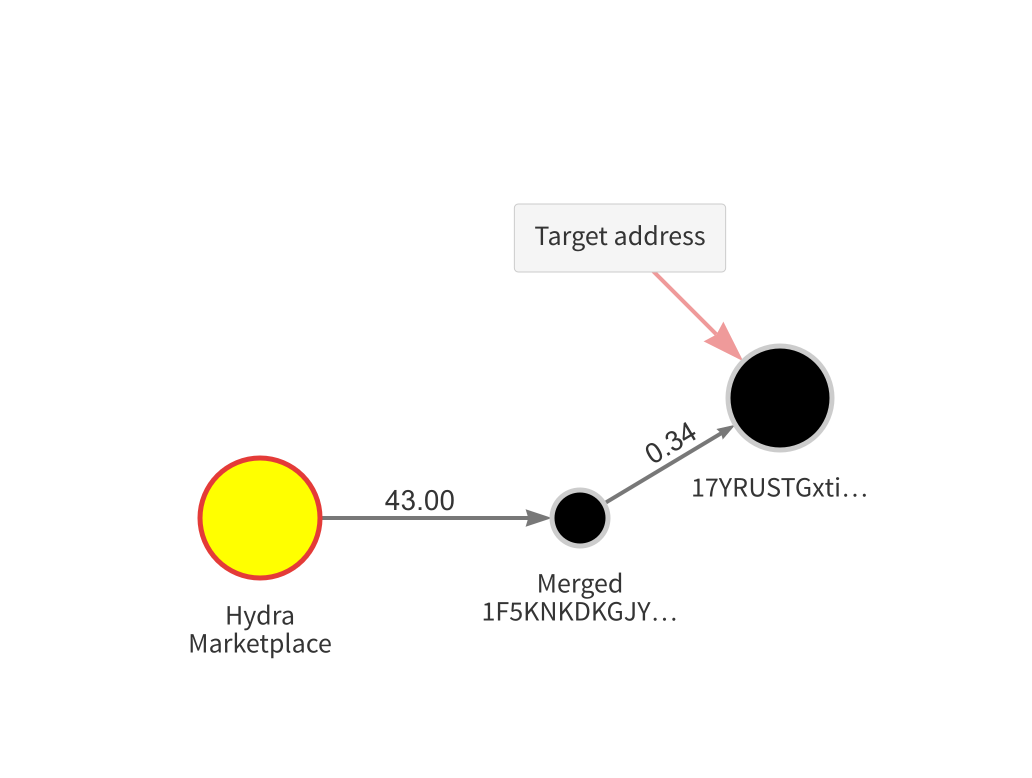
Without Reactor showing the target address’ indirect exposure to Hydra, you may not have known to conduct this analysis. Update: Chainalysis Reactor now offers automated peel chain detection. See how it works here!
You can’t tell the whole story without indirect exposure
Analyzing direct counterparties is the best way to assess the risk of a cryptocurrency address, but it won’t tell you the whole story. The unique infrastructure of cryptocurrency means we have to analyze those counterparties’ exposure as well. Indirect exposure measurements allow us to warn investigative and compliance teams of a target address’ possible link to criminal activity as specifically as possible, but with enough context for them to know how to investigate further.
Want to learn more about how to use indirect exposure in investigations, untangle peel chains, and assess cryptocurrency risk across multiple hops? Check out our Chainalysis Reactor Certification (CRC) training program!
