Cryptocurrencies represent an opportunity to expand the way people transact globally. Since Bitcoin’s launch in 2009, cryptocurrency has created new markets, spurred innovation in financial infrastructure, and brought about new ideas on how we can meet the world’s economic needs. Given all of these positives, it shouldn’t be a surprise that cryptocurrency adoption has continued to grow.
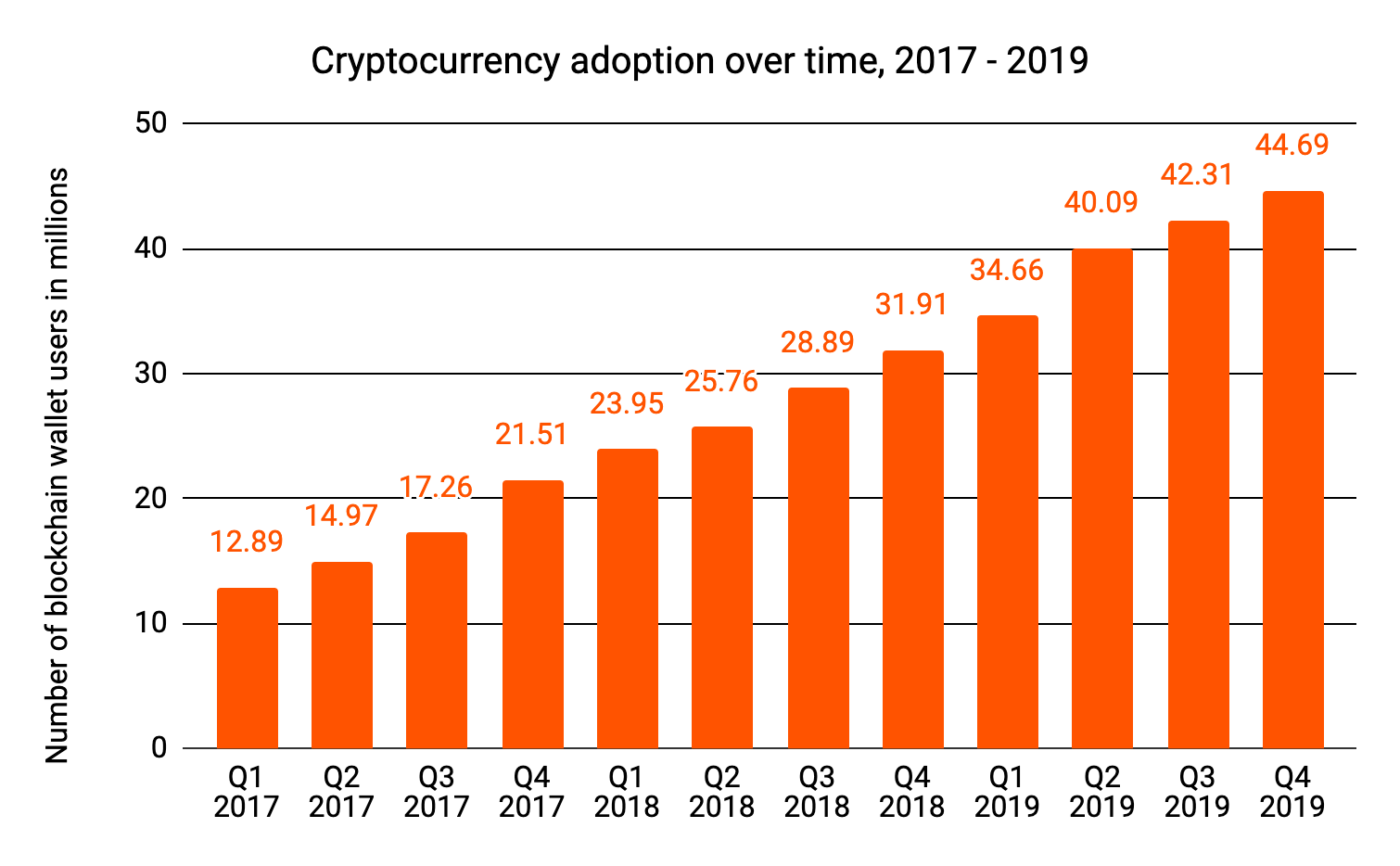
But in order for that growth to continue, all relevant stakeholders — industry operators, traditional financial institutions, and governments — need a shared understanding of all the players in the cryptocurrency ecosystem. Only then can they identify the next big opportunities and ensure that blockchains are a safe place to do business. Key to this is an understanding not just of who the entities conducting cryptocurrency transactions are and how they act, but also the level of risk and illicit activity associated with them.
That’s why we wrote our Cryptocurrency Typologies Guide. As a blockchain analysis firm, we’re always thinking about risk and illcit activity in cryptocurrency, as we work hand in hand with industry operators, governments, financial institutions to bring more transparency to the industry. Below, we’ve placed the most important cryptocurrency typologies, representing the key services and groups transacting with cryptocurrencies today, on a spectrum according to risk.
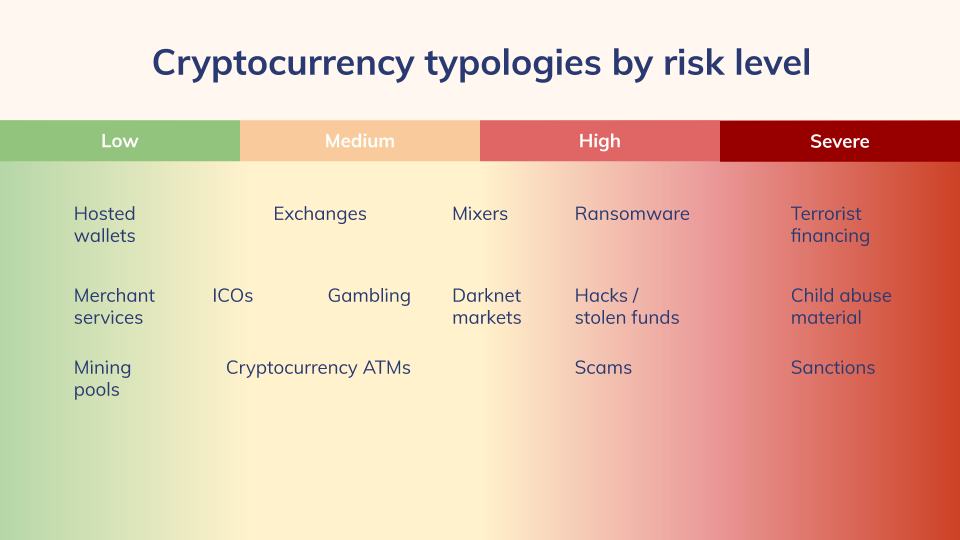
On the left are services like hosted wallets and merchant services, which are used less often for illicit activity and are therefore lower risk. On the right are typologies like terrorist financing schemes, which are illegal under any circumstances, and therefore rated as severely risky. Those in the middle aren’t universally considered illegal but are often linked to or used to aid in criminal activity.
While these risk levels represent the typologies themselves at a high level, they aren’t enough on their own to assess the risks associated with a specific entity. The only way to do that is to analyze that entity’s cryptocurrency transactions and counterparties in greater detail. But if you’re new to cryptocurrency, our Typologies Guide will give you a deeper understanding of each typology’s most common use cases and show you what to be on the lookout for to limit your risk of exposure to illicit activity.
Click here to download the full Typologies Report and get a deep dive into each individual typology, complete with original research and data.
