Ransomware is a widespread problem. Chainalysis has identified more than 52,000 victims of the attacks, and this likely underestimates the issue because so many breaches go unreported.
In recent years, ransomware perpetrators have become more sophisticated, resulting in a more targeted approach and higher costs for individual victims. The average amount sent to ransomware addresses increased more than tenfold between 2015 and 2019.
Perpetrators of ransomware attacks employ cryptocurrency for secrecy; however, Chainalysis has the resources and expertise to crack the code. Recently, we used proprietary heuristics to gain insight into ransomware attackers, their motives, their methodologies and, crucially, the way they cash out illicit revenues. Here is what we found.
Who are the perpetrators of ransomware attacks?
There are two main categories of ransomware perpetrators: organized criminal groups and state actors.
Organized criminal groups
Organized criminals operating primarily out of Eastern Europe initially used a “wide and shallow” ransomware approach to find victims. Their attacks used spam kits to spread virus-infected software rapidly and indiscriminately, sometimes to hundreds of thousands of victims in a single attack.
These attackers often developed highly automated infrastructure to handle infections, payments, decryption, and laundering. They typically demanded small ransom payments; it was a high volume, low dollar value attack.
The infrastructure employed in these attacks strongly benefitted from the “network effects” present in organized crime circles—where criminals could simply plug into well-run laundering mechanisms built and used by their “network.”
State actors
State-led ransomware typically comes from heavily sanctioned countries like North Korea, Iran, and Russia. They operate for a variety of reasons, not just to steal funds but also to sow chaos for their adversaries.
For instance, NotPetya was a widespread ransomware attack led by the GRU, the intelligence arm of the Russian military. NotPetya never developed a workable payment mechanism; the attackers may not have ever intended to decrypt any files. Given the large number of Ukrainian victims, it seems that NotPetya’s primary objective was sabotage and geopolitical disruption.
The WannaCry ransomware attack, linked to North Korean cybercriminal group “Lazarus,” similarly had no known cases of decryption. This was another attack with no real infrastructure for handling ransom payments. It only had three payment addresses and there was no clear way to communicate with victims. It is unlikely that financial gain was the main objective, but it’s difficult to discern a core motive. Perhaps the attackers were experimenting with new technologies, or the attack was an attempt at sabotage that was made to look like ransomware. Or WannaCry may have just “escaped” and accidentally affected more people than originally intended.
How ransomware has evolved
Businesses and individuals have taken steps to protect themselves against ransomware in the last few years, including installing software patches, training around simple security procedures, and moving important files into cloud storage services.
Organized criminal groups as well as state actors evolved their approach as a result, with more strategic, targeted ransomware attacks that have extracted over $2,300 per victim on average in 2019, up from $210 four years prior.
Who are the victims of ransomware?
- High value targets such as the people handling finances for medium-sized financial institutions that likely have more lax security. Accountants in Russia were recently targeted through “malvertising” campaigns on websites pertinent to the accounting profession.
- Targets with sensitive data such as hospitals where every second that data is locked up matters, including the U.K. National Health Service and Atlanta hospitals in the US. Perpetrators also target government organizations to gain access to sensitive data, such as information about police protection programs.
- Organizations typically with low security or easy-to-breach systems. These include educational institutions with limited budgets for computer security systems whose HR departments can typically be accessed through imposter job applications.
- Organizations with data that can be turned into attractive targets for state actors including government agencies, defense contractors, government consultants, and political campaigns. While some attackers wish to gain access to sensitive files, others may simply wish to delete data to create chaos. For instance, NotPetya spread rapidly among Ukrainian businesses, causing havoc by erasing tax reporting data. Ukrainian subsidiaries of multinationals like FedEx and Maersk then spread the attack globally, amplifying the damage.
Investigating and disrupting ransomware attacks
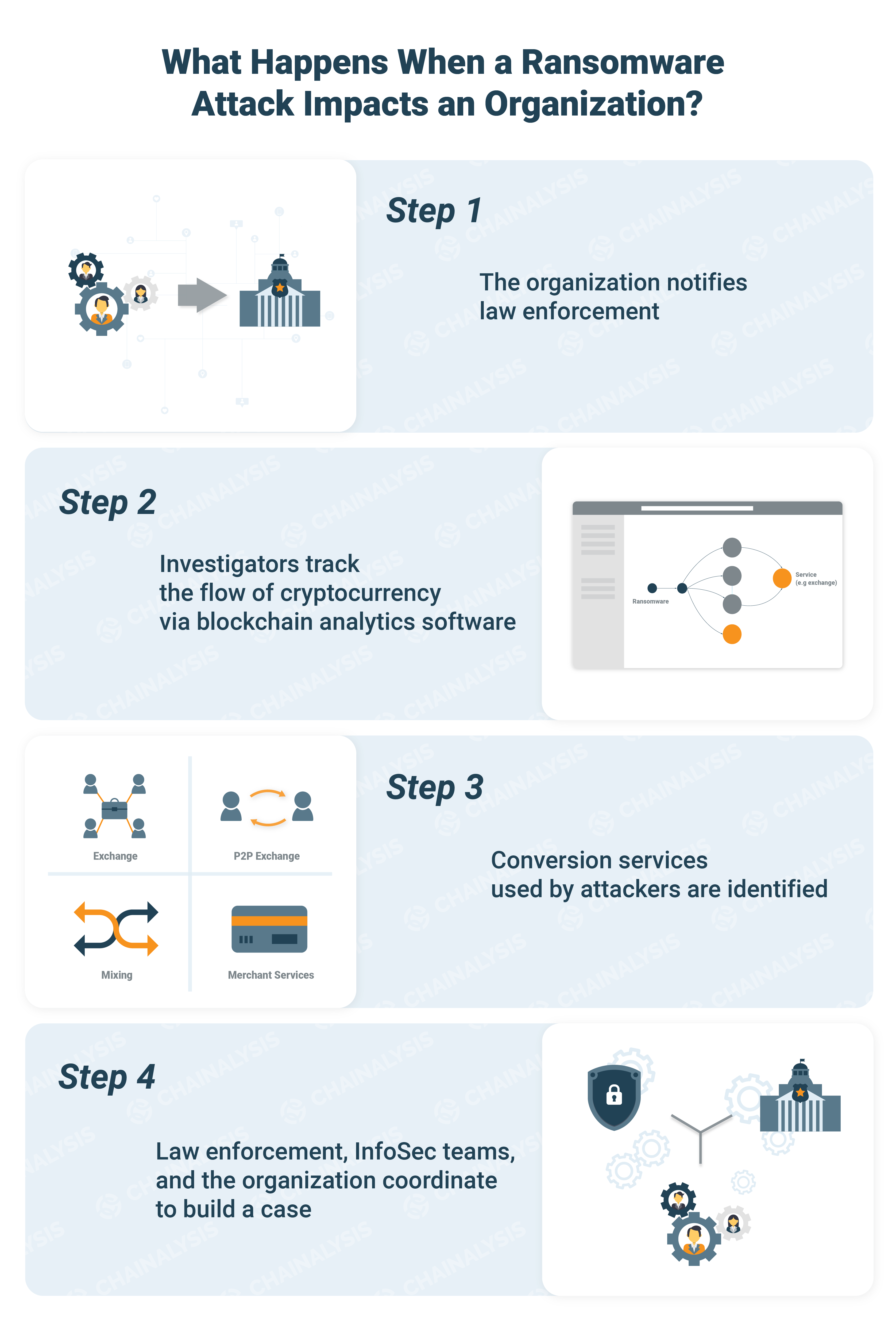
By “following the money” after an attack, we can better understand ransomware perpetrators and develop strategies for disrupting their activities. Chainalysis has tracked hundreds of ransomware attacks since 2014 and identified hundreds of services that received the stolen cryptocurrency funds. Exchanges are the most popular such services, receiving nearly 50% of the stolen cryptocurrency funds, followed by mixing services (34%) and P2P exchanges (8%).
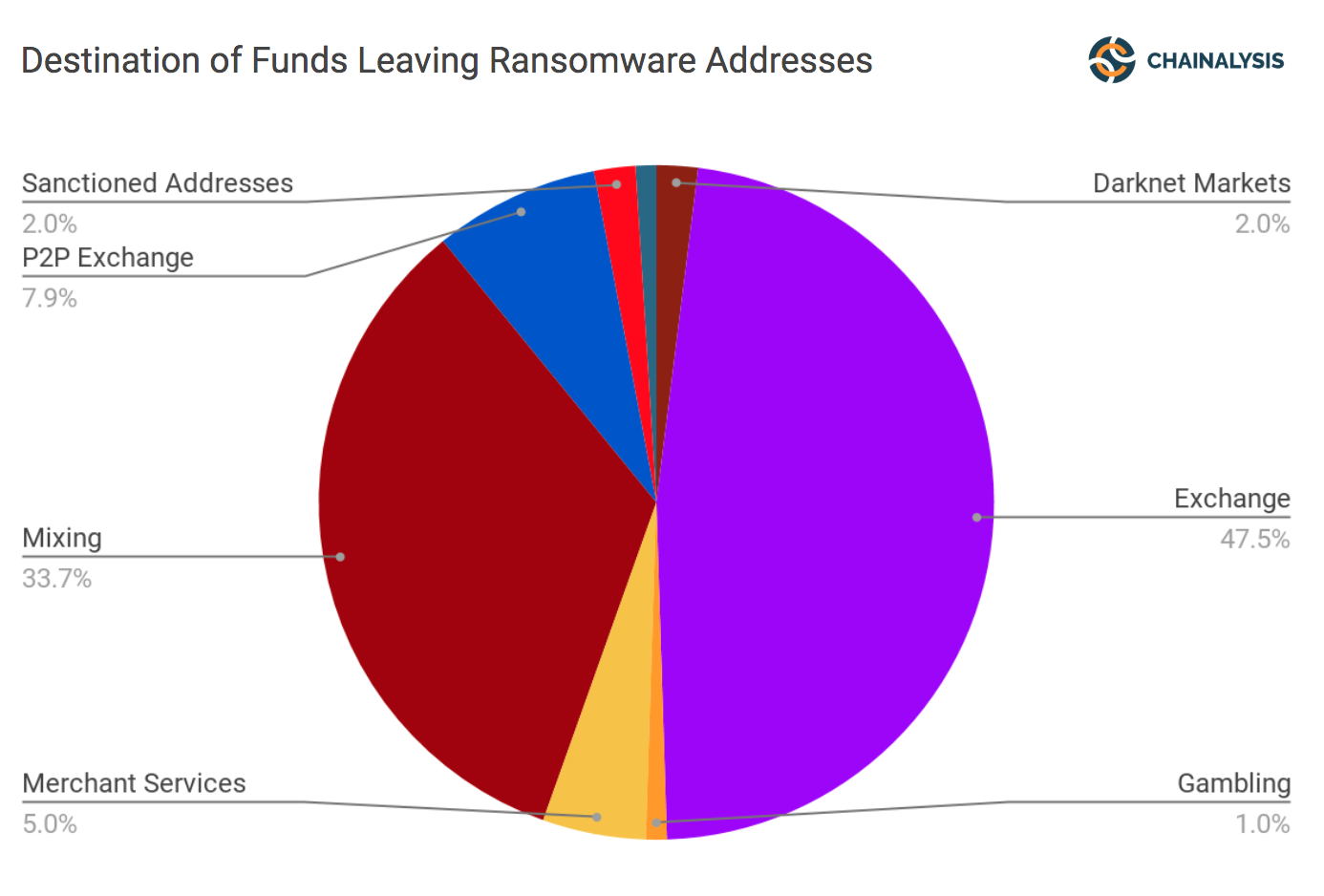
Once we identify the destination of funds, we then work with law enforcement who can then subpoena the service to identify criminals behind the attack.
Our investigators have found that ransomware attackers typically cash out or convert funds via services quickly and simply; there are no elaborate fund movements between receipt of funds and their withdrawal through services.
Ransomware perpetrators focus on criminally friendly exchanges such as BTC-e, or conversion services with low KYC (Know Your Customer) requirements. However, even exchanges with strong KYC standards may see ransomware proceeds come through their organizations. As a result, identifying ransomware attackers is a problem for the entire cryptocurrency ecosystem.
Recommendations
Ransomware attacks have become more sophisticated and costly in recent years, and they can have a devastating impact on targeted organizations. To protect against them, organizations should follow these recommendations:
- Know the actors. State actors and criminal organizations approach ransomware attacks differently. Understanding their aims and methods is the first step towards protection.
- Act quickly. Ransomware attackers move stolen funds quickly, often in a single transaction. Time is of the essence if you want to get funds back.
- Engage law enforcement. Many victims don’t report ransomware attacks. As a result, perpetrators operate with impunity. If you are the victim of an attack, it’s important to get law enforcement involved. By sharing data about attacks among exchanges, law enforcement professionals, investigators, and other key parties, we can develop better tools for catching perpetrators and recovering stolen funds.
- Use available tools. Familiarize yourself with specialized software that identifies ransomware perpetrators, tracks stolen fund flows, and helps prevent or thwart ransomware attacks.
For more information about how Chainalysis’ blockchain analysis can help you protect your organization from ransomware, contact us today.
