New updates, 4/6/23: Hacker returns stolen funds, marking one of the largest DeFi recoveries
Several weeks after the $197 million Euler Finance Flash Loan Attack, the hacker returned the stolen funds and apologized through a series of encrypted messages. The hacker, who identifies as Jacob, began by sending 54,000 in ETH (3,000 on March 18 and 51,000 on March 25) to Euler and followed with 7,000 ETH and $10 million in DAI several days later. Jacob also sent ETH and DAI from these addresses, all of which Jacob funded directly:
- 0x46e0Be2DF97dAc791fC8e30Cf2b2E4f58c50Cf55
- 0xa1b44d4b5b4C361f51E029b81bf2Db9cF4D8e676
- 0xC4e04Ac48639FF077eBb36E7cFe0C4993b7b208E
- 0x8765A35394C98e81B9d56d44248E1199D8E38A4c
- 0xB2698C2D99aD2c302a95A8DB26B08D17a77cedd4
- 0xc66dFA84BC1B93df194bD964a41282da65D73c9a
As the below image demonstrates, Jacob expressed intentions to eventually return all of the funds, which Jacob fulfilled:
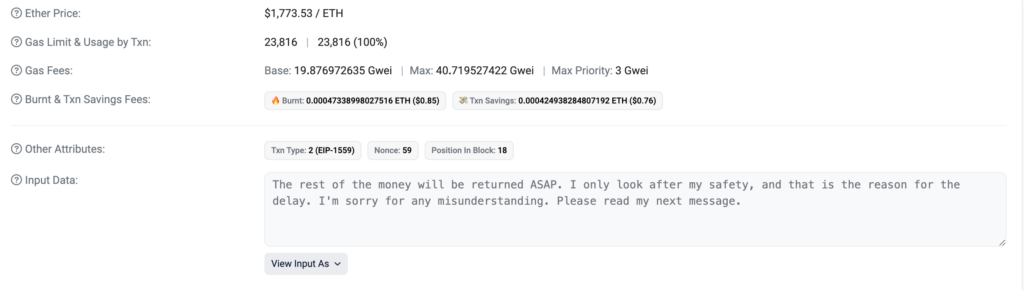
Source: Etherscan
The following Chainalysis Reactor graph shows the movement of funds back to Euler Finance:
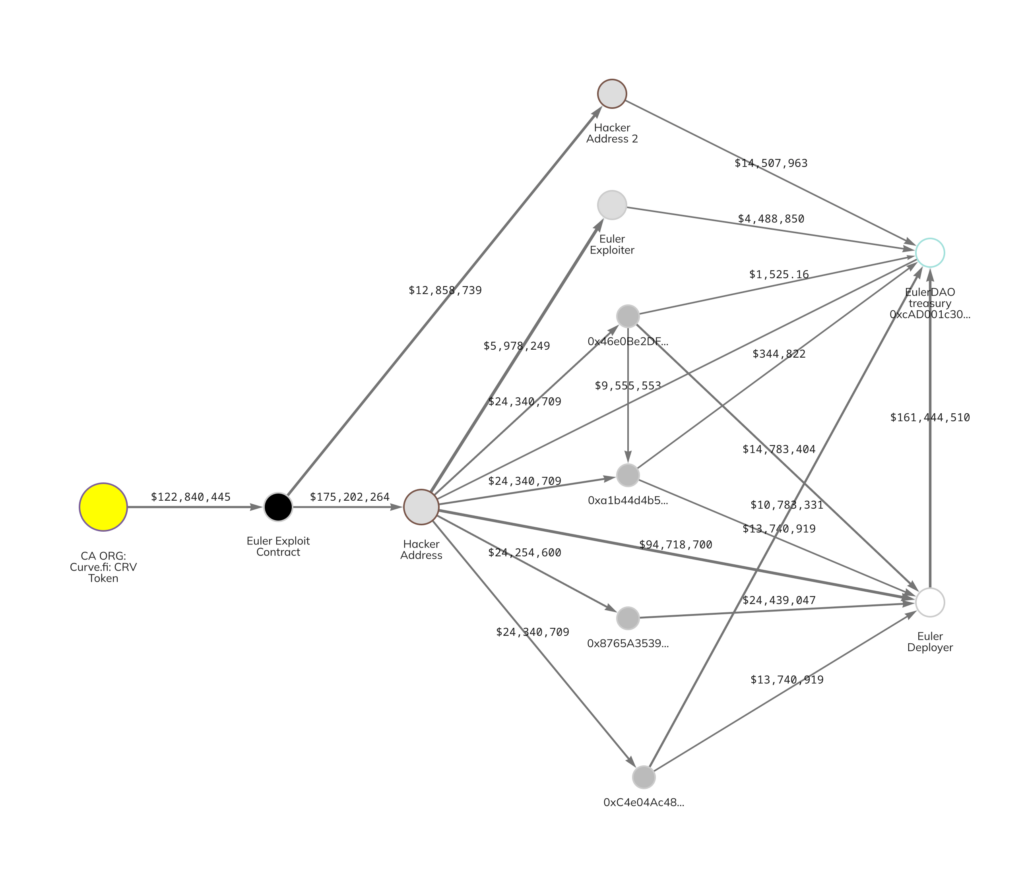
On April 4, Euler released a statement, announcing that the community investigation is finished and the company is developing a plan to restore user assets.
New updates, 3/17/23: Possible North Korean involvement
Early in the morning of March 17, 2023, 100 ETH stolen in the Euler Finance hack moved to an address that previously received funds stolen in the Axie Infinity Ronin Bridge hack, which was carried out by the North Korean hacking syndicate Lazarus Group.
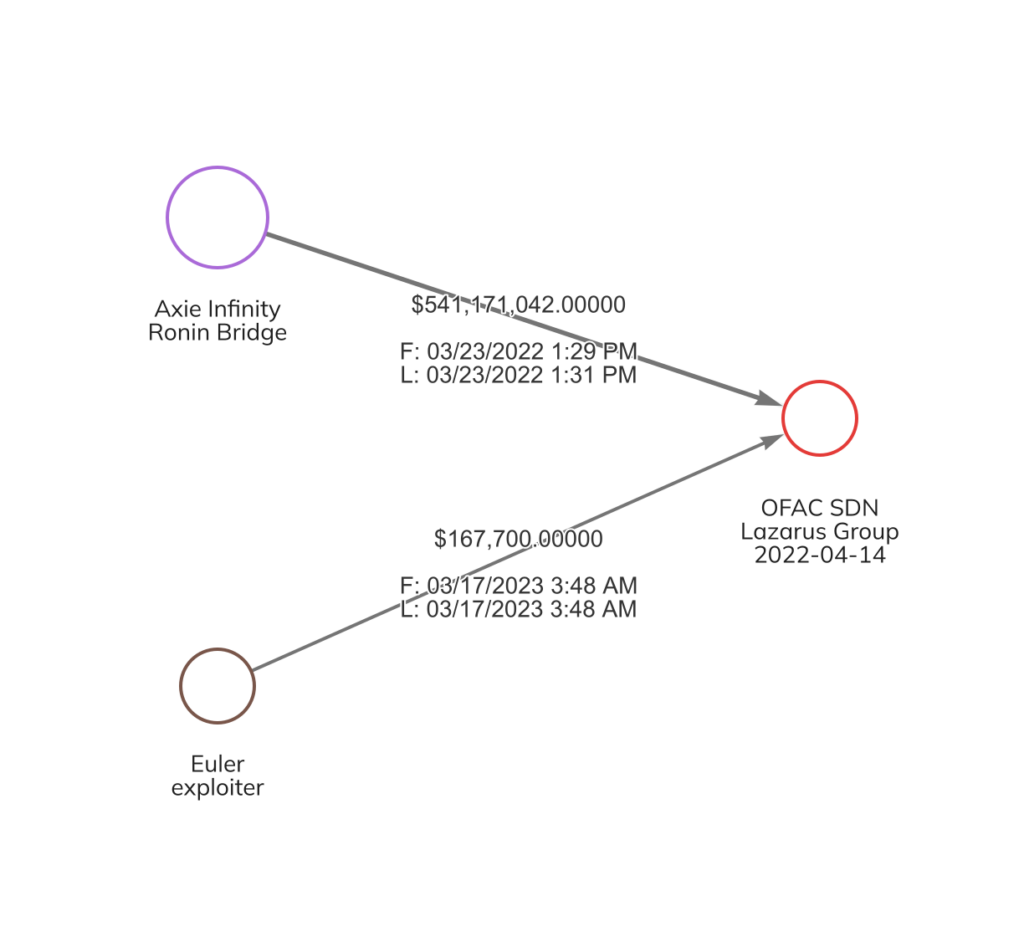
This could also mean that the Euler Finance hack was also carried out by Lazarus Group. However, we can’t yet know for sure — it’s possible that this movement of funds was an attempt at misdirection by another hacking group. We will continue to monitor the situation and provide updates as possible.
Original post: Analysis of Euler Finance flash loan attack
On March 13, 2023, Euler Finance, a permissionless borrowing and lending protocol on Ethereum, was the victim of a flash loan attack. Euler Finance isn’t the first DeFi hack victim this year — dForce and Platypus were similarly targeted in February — but it is unfortunately the largest. At a whopping near-$200 million loss, hackers stole funds in USDC, wrapped Bitcoin (wBTC), staked Ether (stETH), and DAI, an algorithmic stablecoin maintained by MakerDAO. A hack of this magnitude illustrates both the ongoing threats to widely used DeFi protocols and the potential hacking abuses opened up by flash loans.
In this blog, we’ll explore how flash loans work, how hackers stole funds from Euler Finance, and how the effects of flash loan attacks may be mitigated in the future.
What is a flash loan?
Before analyzing the details of the Euler hack, it is important to understand how flash loans typically work. Flash loans are executed by smart contracts and enable participants to quickly borrow funds without the need for collateral. However, these loans must be repaid in full within the same transaction, or else the entire transaction, including the loan itself, will be reversed. Flash loans are attractive for DeFi traders looking to maximize arbitrage opportunities. They are also commonly used for swapping collateral and self-liquidation.
Although there are several legitimate uses of flash loans, hackers can also use them to manipulate DeFi protocols’ pricing oracles. They do this by taking advantage of the lack of collateralization to borrow huge amounts of funds, which they can then use to manipulate token prices, typically by buying or short selling high volumes of tokens with thin supply levels.
How the Euler Finance flash loan attack occurred
When users borrow and lend using the Euler Finance platform, they primarily transact with two types of tokens: eTokens (which represent collateral) and dTokens (which represent debt). Euler issues eTokens based on the types of funds deposited by users; dTokens automatically trigger on-chain liquidation when the platform holds more dTokens than eTokens.
The hack was made possible by a liquidity issue in the DonateToReserve function of the eToken. This function was properly burning eTokens, but not dTokens, leading to an incorrect conversion of borrowed assets to collateralized assets. Euler’s hacker took advantage of these inconsistencies to create a false impression that the platform had a low amount of deposited eTokens and fake debt due to the fact that the dTokens were not burned.
We currently have reason to believe that there were two primary on-chain entities involved in the hack: a front-running MEV bot (using the wallet 0x5F259D0b76665c337c6104145894F4D1D2758B8c) and the hacker’s primary personal wallet (using the wallet 0xb66cd966670d962C227B3EABA30a872DbFb995db). The hacker hardcoded their lending contract so that the personal wallet received most of the funds, regardless of which entity executed which transactions.
The hacker received initial funding from the sanctioned mixer Tornado Cash for gas fees and to create the contracts used in the exploit, then initiated a flash loan to borrow around $30 million in DAI from the DeFi protocol Aave. After this, the hacker deposited $20 million of that DAI into Euler’s platform, receiving a similar amount in eDAI tokens. By leveraging Euler’s borrowing capabilities, the hacker was able to borrow 10 times the original deposited amount. The hacker then used the remaining $10 million in DAI from the original loan to repay part of the acquired debt (dDAI) and reused the mint function to borrow again until the flash loan was closed. After the hack was complete, the hacker moved some of the funds back to Tornado Cash. Investigators would need to employ advanced investigative techniques like those Chainalysis offers to pursue the funds further.
We can see some of these steps in the Chainalysis Storyline graph below:
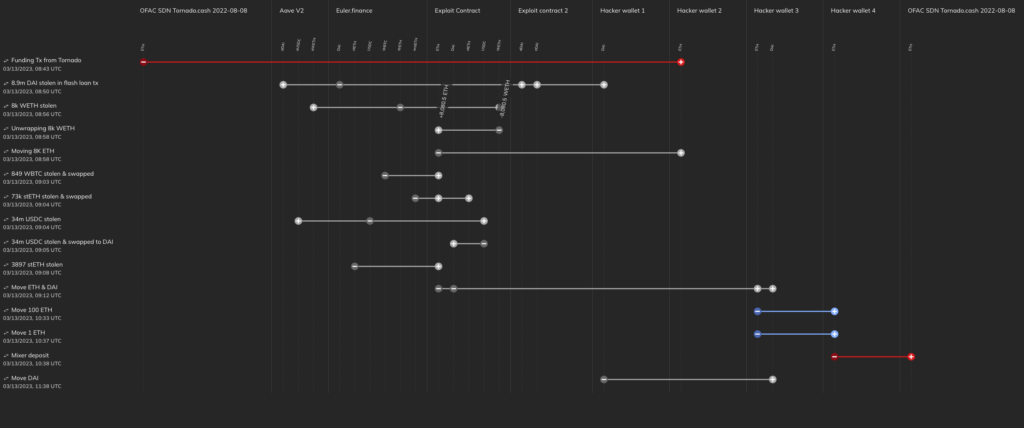
Overall, Euler lost roughly $197 million worth of cryptocurrency, spread across DAI, wBTC, stETH, and USDC. Additionally, Euler’s native token, EUL, declined more than 45%.
Reducing hacking risks
Although it can be difficult to identify DeFi platform vulnerabilities, there may be several methods to mitigate risk of flash loan attacks to protect cryptocurrency participants from similar catastrophic events. For instance, circuit breakers could be used to temporarily halt protocols when there are unusually large price movements or outflows so that hacks can be stopped early. We will continue to monitor the Euler hack situation and provide updates as possible.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

