Update, 11/30/23: U.S. and Japan join South Korea in sanctioning Kimsuky
On November 30, 2023, the United States’ Office of Foreign Assets Control (OFAC) and Japan’s Ministry of Foreign Affairs joined South Korea’s Ministry of Foreign Affairs in sanctioning Kimsuky. The U.S. Treasury Department emphasized Kimsuky’s cyber espionage activity and role in supporting North Korea’s nuclear weapons program in its press release regarding the designation. All three countries sanctioned several other individuals and entities associated with North Korea’s weapons program, some of which were also sanctioned by Australia’s Department of Foreign Affairs.
While OFAC’s SDN list entry for Kimsuky included several websites and email addresses as identifiers, there were no cryptocurrency addresses, unlike South Korea’s sanctions designation back in June.
As we explain in more detail in our original blog below, Kimsuky’s usage of cryptocurrency differs from the hacking we see from other North Korean groups like Lazarus Group. Rather than steal crypto to funnel to the government, Kimsuky obtains cryptocurrency — sometimes through mining and semi-legitimate services, and other times through malicious activity like extortion campaigns — to fund other operations, which are primarily focused on intelligence gathering on behalf of the North Korean regime. Proofpoint Senior Threat Researcher Greg Lesnewich told us more about Kimsuky’s crypto activity and why today’s international effort is so important.
“Unlike other North Korean operations, the clusters under the Kimsuky umbrella use cryptocurrencies to help fund their own operations in support of strategic intelligence gathering, instead of funneling funds directly for the regime to use elsewhere. The variety of ways North Korean actors attempt to acquire and use cryptocurrencies continues to diversify and increase in tempo, so it is encouraging to see sanctions be regularly applied to disrupt and counter their activity.”
Original blog: Kimsuky sanctioned by South Korean’s MOFA on June 1, 2023
On June 1, 2023, South Korea’s Ministry of Foreign Affairs (MOFA) sanctioned Kimsuky, a North Korean hacking group, and included two cryptocurrency addresses as identifiers for the organization. Additionally, MOFA collaborated with South Korea’s National Intelligence Service (NIS) and National Police Agency (NPA), as well as the United States’ Federal Bureau of Investigations (FBI), Department of State, and National Security Agency (NSA) to issue a joint advisory on related North Korean cyber espionage activities.
What is Kimsuky?
Active since at least 2012, Kimsuky is a North Korea-based cyber espionage organization that is known to have stolen technologies related to weapon and satellite development, and foreign policy information on behalf of the North Korean government. Kimsuky’s intelligence collection operations have targeted governments – most notably the South Korean government – political organizations, and academic organizations. Additionally, Kimsuky has used scams, theft, cryptojacking and sextortion tactics on civilians, likely for the purpose of self-funding.
Analyzing Kimsuky’s crypto activity
In many cases, Kimsuky has utilized cryptocurrency in an attempt to obfuscate its transactions. According to Greg Lesnewich, Senior Threat Researcher at Proofpoint, “Kimsuky operations involving cryptocurrency are reflective of the North Korean cultural tenet of ‘juche,’ or self-reliance. The operators have mined cryptocurrencies to generate and launder funds, operated semi-legitimate services to get paid in Bitcoin or Ethereum, and conducted infrequent malicious activity targeting cryptocurrency entities as well as individuals with sextortion campaigns.” Similarly, Joseph Dobson, Mandiant Principal Analyst at Google Cloud, notes that Kimsuky “predominantly utilizes stolen cryptocurrency to fund their offensive cyber operations… through token phishing, cryptojacking, and opportunistic wallet theft.”
The two addresses the Korean Ministry of Foreign Affairs included on its list are bc1qmkh9s8qju9tkk2qckcz79we2084h2ckeqxylnq and bc1qu9303km9mnq03hxehvtf2tzchvmkqnzyzm928d. In the Chainalysis Reactor graph below, we see some of the activity of these two addresses, which involved transactions with mainstream exchanges and mining pools.
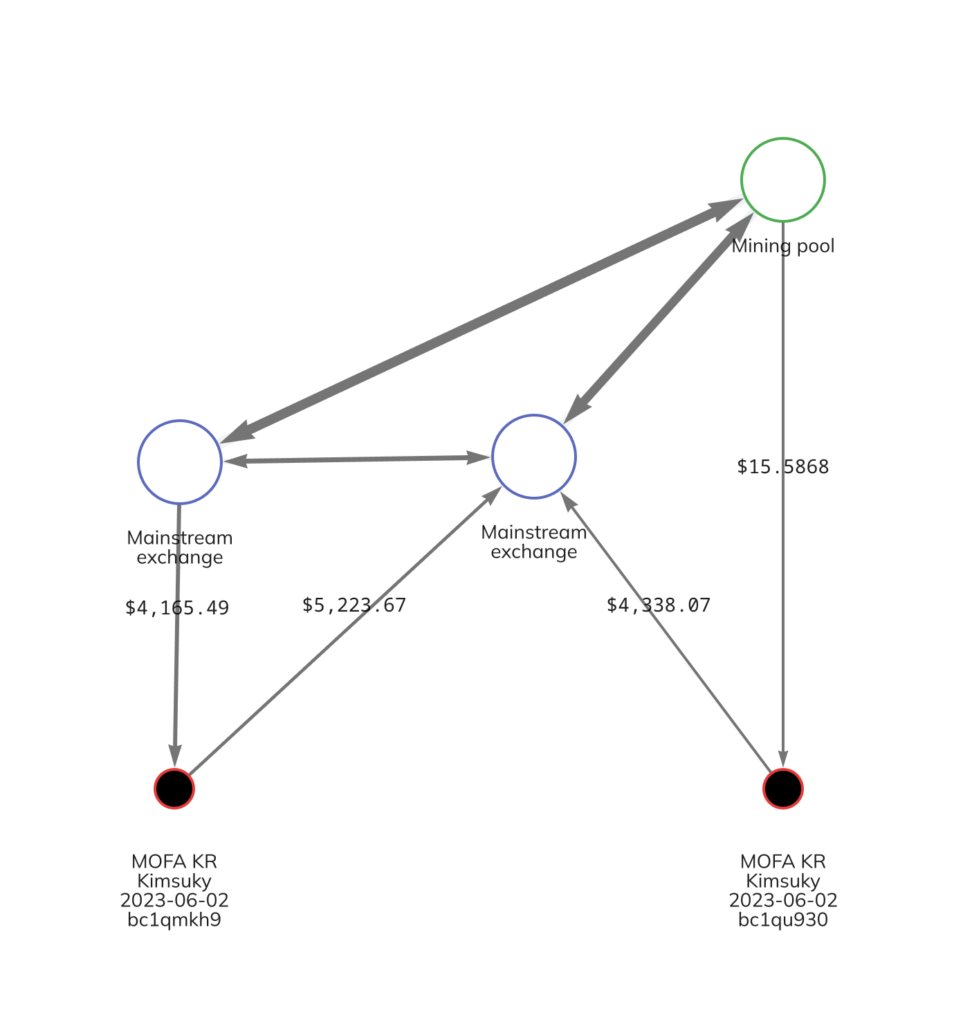
While MOFA did not specify the exact nature of the illicit activity these Kimsuky wallets were used for, their on-chain activity provides some possible clues. The screenshot below shows a series of transactions for one of the Kimsuky addresses identified by MOFA.
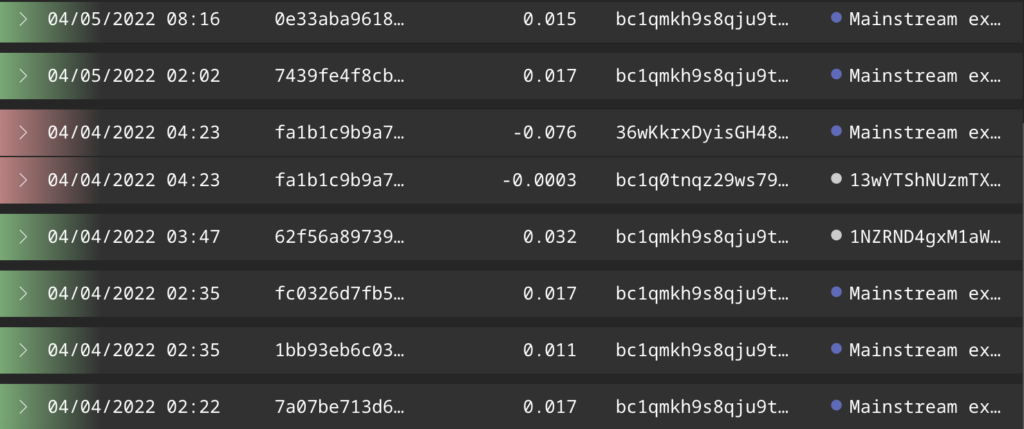
The constant reception of small, similarly-sized amounts of cryptocurrency may reflect Kimsuky’s victim payments related to a sextortion or blackmail campaign. These campaigns typically are spread through “spray and pray” methods in which the blackmailer emails thousands of individuals, threatening to release sexually compromising material on the recipients (which, to be clear, they usually do not actually possess) unless they pay a small amount of Bitcoin to the blackmailer’s Bitcoin address. We can see an example of one such blackmail email below.
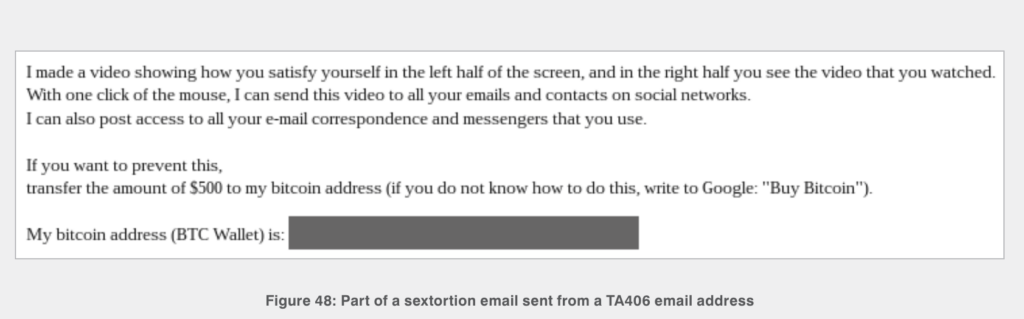
Source: Proofpoint
However, it is also possible that these payments are the result of fraud. Security researchers have noted that Kimsuky has at times launched fake charity drives, tricking victims into thinking they were donating cryptocurrency to South Korean non-governmental organizations (NGOs).
Our Reactor graph also shows Kimsuky interacting with mining pools. These may reflect money laundering efforts, as security researchers have also noted that North Korean hacking groups like Kimsuky sometimes send illicitly obtained cryptocurrency to mining pools or hashing services in order to receive freshly mined, clean cryptocurrency in return.
Monitoring North Korean cyber crimes
These two sanctioned addresses represent a small portion of cryptocurrency used in malicious cybercrimes, but nevertheless illustrate the need for law enforcement to monitor on-chain activity and North Korean organizations’ exploitative tactics. At Chainalysis, we commend MOFA and the United States government for their actions toward reducing cryptocurrency-based crimes. We will continue to provide updates when available and have labeled the identified addresses as associated with sanctioned entities in our product suite.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

