Last Friday, September 25, 2020, hackers stole more than $275 million worth of cryptocurrency from KuCoin in one of the largest ever exchange hacks. Specifically, the stolen funds included:
- 1,008 BTC ($10,758,404.86)
- 11,543 ETH ($4,030,957.90)
- 19,834,042 USDT-ETH ($19,834,042.14)
- 18,495,798 XRP ($4,254,547.54)
- 26,733 LTC ($1,238,539.89)
- 999,160 USDT ($999,160)
- $147M worth of ERC-20 tokens
- $87M of Stellar tokens
At this time, we cannot disclose the whereabouts of all of the cryptocurrency we’ve tracked thus far stolen in the Kucoin hack. However, we can share that, as of 10:00 AM ET on Friday, October 2:
- The 1,008 BTC stolen in the attack is split between two addresses, with one holding 201 BTC and the other holding 807 BTC.
- The hackers have purchased and withdrawn roughly 875 BTC from centralized exchanges using altcoins stolen in the hack, including but not limited to Litecoin. Of that newly-purchased 875 BTC, roughly 683 BTC has been sent to mixing services.
- 50,001 USDT_ETH of the 19,834,042 USDT-ETH stolen has been moved, with 20,000 USDT_ETH going to the decentralized exchange Uniswap, 11,000 USDT_ETH going to the exchange MXC, 1,000 USDT_ETH going to the exchange Poloniex, and 500 USDT_ETH going to the exchange FatBTC. Another 3,000 USDT_ETH has been sent to three separate addresses where it continues to sit, and the remaining 15,400 USDT_ETH remains unspent in an intermediary wallet.
- All 26,733 LTC stolen in the attack has been deposited to exchanges.
However, what’s especially notable about this hack is how the perpetrators have used DeFi protocols to launder the stolen ETH and ERC-20 tokens. DeFi stands for decentralized finance, and generally refers to decentralized apps (dApps) built on top of smart contract-enriched blockchains — primarily the Ethereum network. These dApps can fulfill specific financial functions governed by underlying smart contracts, meaning they can execute transactions — trades, loans, etc. — automatically when specific conditions are met. Without the need for centralized infrastructure or human governance, dApps can theoretically enable users to execute financial transactions at lower fees than other fintech applications or financial institutions.
In this case, the KuCoin hackers used platforms like Uniswap and Kyber, which are both examples of a specific type of dApp known as a decentralized exchange (DEX). DEXs allow users to buy, sell, and swap different tokens built on a specific blockchain (again, primarily Ethereum) directly between one another’s wallets for greater privacy and security. Since these platforms never actually take custody of the funds, instead facilitating direct transfers, users can complete these currency swaps without having to provide KYC (know-your-customer) information or the trades being recorded in an order book as they would be on a standard cryptocurrency exchange.
However, because Chainalysis supports many of the ERC-20 tokens in question, investigators using Reactor can trace most of these funds despite the complicating effects of DeFi. Below, we’ll break down the movements of a portion of the ETH and ERC-20 funds that the KuCoin hackers have attempted to launder in this manner.
Analyzing KuCoin hackers’ movement of LINK tokens
On the Chainalyis Reactor graph below, we visualize how hackers have moved a portion of the ERC-20 tokens taken. While the hackers stole other ERC-20 tokens as well, the graph below shows transactions involving:
- LINK Token
- TIA Token
- Old Ocean Token
- COMP Token
- KardiaChain Token
Though the graph appears complicated due to the number of cryptocurrencies involved and nature of the DeFi protocols being used, we’ll focus on the movements of LINK specifically to illustrate what’s happening, as the other currencies’ movements follow a similar pattern.
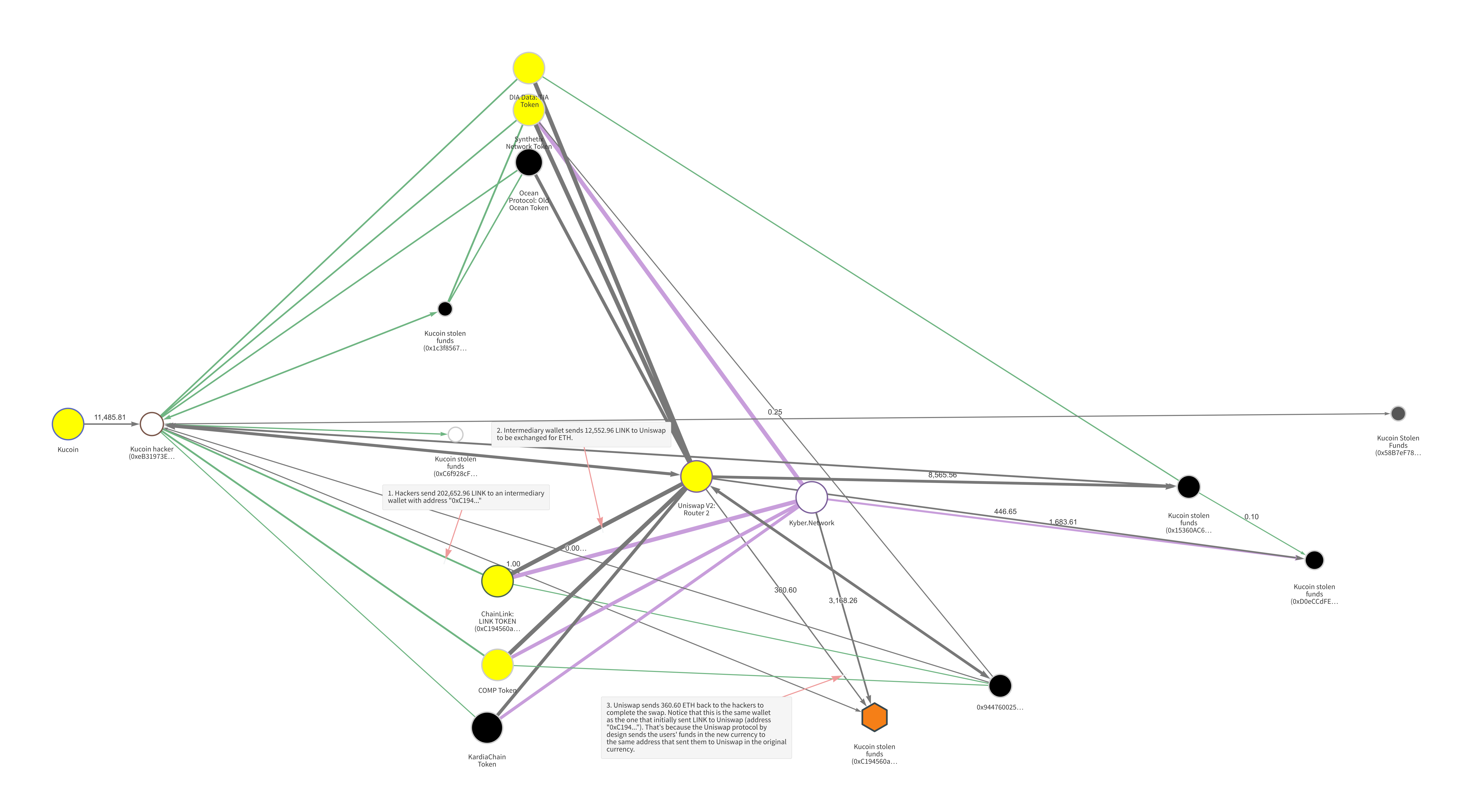
The hackers first moved the LINK from their initial wallet to an intermediary, and from there sent it to Uniswap to be traded for ETH. As a DEX, Uniswap allows users to swap between ETH and several types of ERC-20 tokens without Uniswap ever taking custody of the funds, meaning that users don’t have to provide KYC information. Users simply send funds to Uniswap from one address, and receive the equivalent amount back (minus minimal fees) at the same address in the token of their choice. So, in this case, the Kucoin hackers sent 12,552.96 LINK to Uniswap from the address “0xC194…” and received 360.60 ETH back to the same address. As we can see on the graph, the hackers carried out many similar DEX transactions using other types of tokens stolen in the hack.
By using DEXs, the hackers were able to swap their stolen funds into new types of cryptocurrency without having to go through regulated exchanges who had flagged their addresses and would have required them to submit KYC information. It’s estimated that the hackers sold at least $13 million worth of ERC-20 tokens before the majority was frozen by the underlying smart contracts. In addition, some transactions were reversed via forking.
DeFi presents new but solvable hurdles for investigators
In addition to showing you how the KuCoin hackers have thus far attempted to move and launder stolen ETH and ERC-20 tokens, we hope that this case study shows the difficulties that arise for investigators when cybercriminals use DeFi platforms. However, by continuing to support more and more ERC-20 tokens, we can equip law enforcement and compliance professionals with the tools they need to continue tracing funds even when they move to DeFi protocols. Our training and professional services teams stand by ready to help investigators master new techniques to follow these types of transactions.
We have labelled all addresses identified so far as belonging to the hackers — not just ETH and ERC-20 token addresses, but for all funds stolen — in our products and will continue to tag more as we discover them. We’ll provide further updates on funds stolen in the KuCoin hack as more information becomes available.
Want to learn more about how cybercriminals are exploiting DeFi and other emerging cryptocurrency technologies. Sign up now for our upcoming 2021 Crypto Crime Report and get it delivered to your inbox when it comes out next January!
