Today, the U.S. Department of Justice (DOJ) unsealed a civil forfeiture complaint against the holders of 280 cryptocurrency addresses involved in the laundering of approximately $28.7 million worth of cryptocurrency stolen from an exchange by the North Korea-affiliated hackers known as Lazarus Group. The complaint also analyzes fund movements associated with a second exchange hack the group carried out.
This case highlights the increasingly sophisticated money laundering techniques Lazarus Group is employing in their efforts to launder funds stolen from cryptocurrency exchanges. However, despite these efforts, investigators with the FBI, HSI, IRS-CI, and other agencies were still able to trace the funds to their ultimate destinations. In addition, in some instances, exchanges were able to prevent the hackers from depositing or trading the stolen funds on their platforms.
We congratulate our government partners for cracking a case with serious national security implications in the face of new levels of sophistication from state actors. In addition, we’re proud to equip these partners with investigative tools that help them keep up with these advanced obfuscation techniques and track down the funds cybercriminals seek to launder. We’re also proud to provide exchanges with the transaction monitoring tools necessary to prevent these funds from being traded on their platforms.
You can read the full DOJ complaint here to learn more. Below, we’ll highlight a few specific elements of the case showing how Lazarus Group is becoming more advanced in its money laundering techniques, and how government agencies and exchanges are fighting back with blockchain analysis.
Increasing sophistication of Lazarus Group’s cryptocurrency money laundering efforts
The funds stolen in the two exchange hacks relevant to today’s complaint initially comprised three different types of cryptocurrency: Bitcoin, Ethereum, and Algorand. However, hackers attempted to obfuscate their efforts to move the funds to services where they could be liquidated using a technique called “chain hopping,” in which funds are traded for other types of cryptocurrency to make them harder to trace between blockchains. From there, the hackers attempted to convert funds into Bitcoin and cash out through other services.
We can see examples of this activity in the Chainalysis Reactor graph below, which shows how hackers moved a portion of the Bitcoin stolen in the hacks.
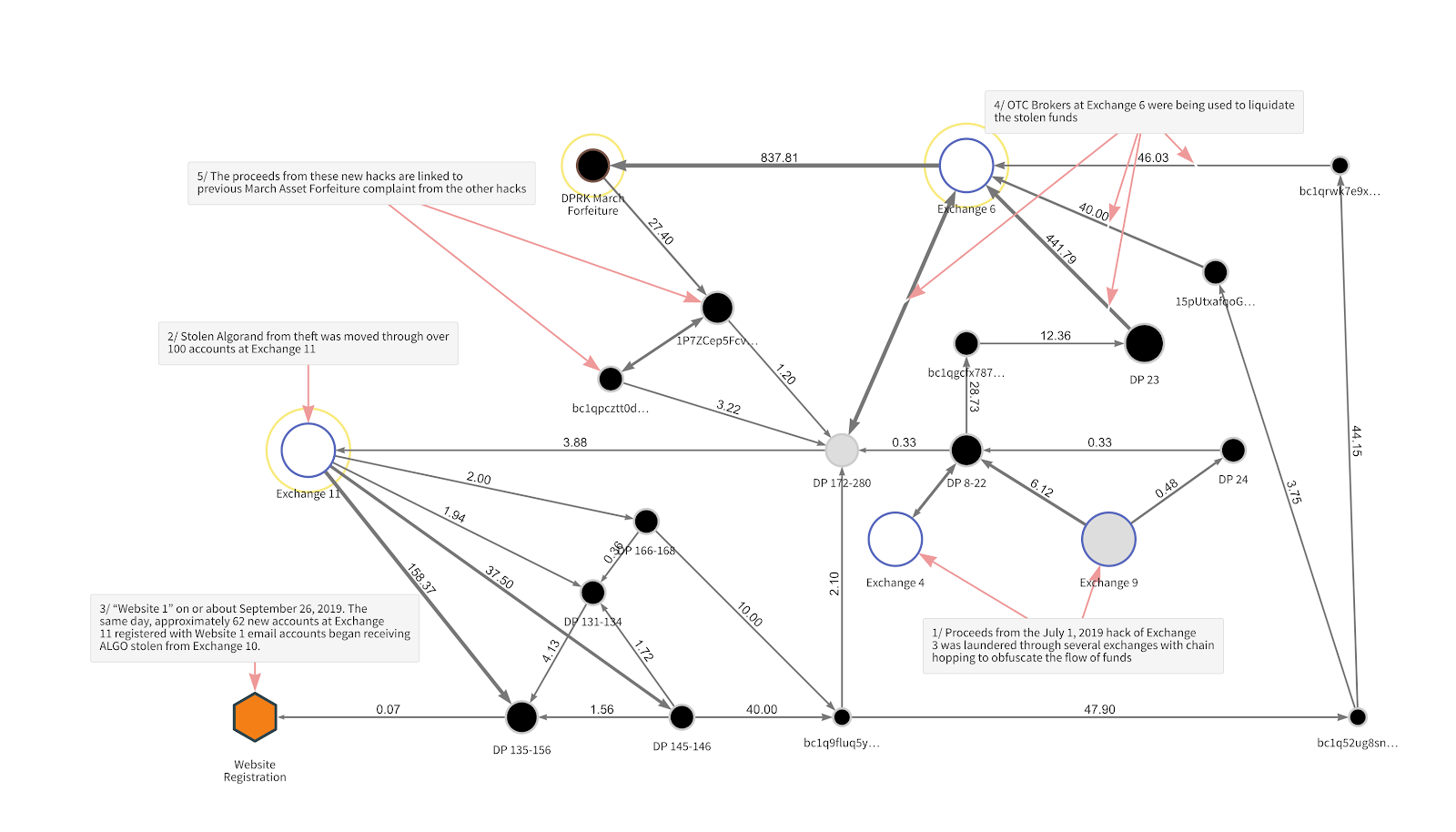
In the lower right-hand region of the graph, we see that hackers moved Bitcoin out of two exchanges, labeled “Exchange 4” and “Exchange 9,” which they obtained via chain hopping, trading other types of cryptocurrency stolen in the initial hack for the Bitcoin we see on the graph. However, agents were equipped with blockchain analysis tools that enabled them to trace the funds even in obscure cryptocurrencies until they were swapped into Bitcoin and moved to “Exchange 6” on the diagram.
However, while the Lazarus Group hackers did employ some new money laundering methods, they also relied on a key old one: Liquidating funds with OTC brokers. For background, OTC brokers facilitate trades between individual buyers and sellers who can’t or don’t want to transact on an open exchange. OTC brokers are typically associated with an exchange but operate independently. Traders often use OTC brokers if they want to liquidate a large amount of cryptocurrency for a set, negotiated price.
As we see in the upper right-hand region of the graph, hackers moved substantial portions of the stolen funds to OTC brokers nested at an exchange — labeled “Exchange 6” — to be converted into cash. We’ve written previously about cybercriminals’ usage of OTC brokers for money laundering purposes before. In fact, some of the specific OTC brokers nested at “Exchange 6” shown on the graph above have transacted heavily with OTCs on our Rogue 100, a list of 100 OTC brokers we’ve identified as frequently dealing in illicit funds over the course of several investigations. That could indicate that these OTCs have been involved in other illicit transactions prior to this case.
Exchanges stepping up
The DOJ complaint also makes it clear that in some instances, exchanges were able to prevent Lazarus Group from laundering funds on their platforms.
For example, the complaint states that in December 2019, the hackers attempted to chain hop by converting Ethereum stolen in one of the hacks into Bitcoin at Exchange 9, which we see in the lower right-hand region of the graph (please note however that Ethereum transactions are not included on the graph above). However, the exchange’s transaction monitoring tools were able to alert them that the incoming funds came from an exchange hack and prevent the transaction from going through. Those funds remain frozen at Exchange 9 today.
That example shows that, while law enforcement is capable of tracing funds through chain hopping transactions, exchanges can prevent those transactions from even happening with the right transaction monitoring tools. The more exchanges that incorporate those tools into their compliance programs, the fewer options hacking groups like Lazarus have to launder and liquidate stolen funds.
We’re moving in the right direction
This case shows yet again that the cryptocurrency industry and government can work together to prevent bad actors from exploiting cryptocurrencies for their own gain, despite their constantly advancing techniques. We’re proud to occupy a unique role as the bridge between government and the industry, supplying each side with the tools they need to make cryptocurrency safer and more transparent so that adoption can continue to grow.
Want to learn more about how Chainalysis helps investigators track funds stolen by Lazarus Group and other cybercriminals? Sign up for a demo here!
