Earlier this week, the U.S. Treasury’s Office of Foreign Assets Control (OFAC) sanctioned two Chinese nationals, Tian Yinyin and Li Jiadong, for their role in helping the North Korea-aligned Lazarus Group launder funds stolen in four separate cryptocurrency exchange hacks between 2017 and 2019. OFAC also added 20 cryptocurrency addresses controlled by the pair to its sanctions list as identifiers for Tian and Li, thereby placing prohibitions on transacting with those addresses. At the same time, the Department of Justice (DOJ) filed a civil forfeiture complaint charging Tian and Li with money laundering on Lazarus Group’s behalf, and seeking to seize funds from 93 additional cryptocurrency addresses and accounts.
UPDATE: On March 6, 2020, the DOJ updated its civil forfeiture filing to include another 33 Bitcoin and Ethereum addresses implicated in this money laundering scheme, bringing the total to 146. We have added the new addresses to the full list later in this article, and will update further if U.S. agencies continue to name new addresses or accounts.
We’ve written previously about Lazarus’ cryptocurrency exchange hacks, which experts believe are carried out to fund North Korea’s weapons of mass destruction programs. This week’s news represents an impressive breakthrough in the United States’ efforts against Lazarus Group. Using Chainalysis tools, the US Government was able to follow the path of funds Lazarus stole from various exchanges, and despite the complex obfuscation measures taken, uncover enough information to identify two of Lazarus’ China-based money laundering partners. Below, we’ll tell you more about how they cracked the case and the information they uncovered.
How the investigation unfolded
Multiple agencies participated in the investigation, using Chainalysis to trace funds stolen in four separate exchange hacks carried out by Lazarus Group between 2017 and 2019. Lazarus collaborated with Tian and Li to launder the stolen cryptocurrency, conducting hundreds of transactions and forming peel chains that further obfuscated the path of funds. We see an example in the Reactor graph below, which shows how Lazarus Group moved funds during one of the 2018 exchange hacks cited in DOJ’s filing.
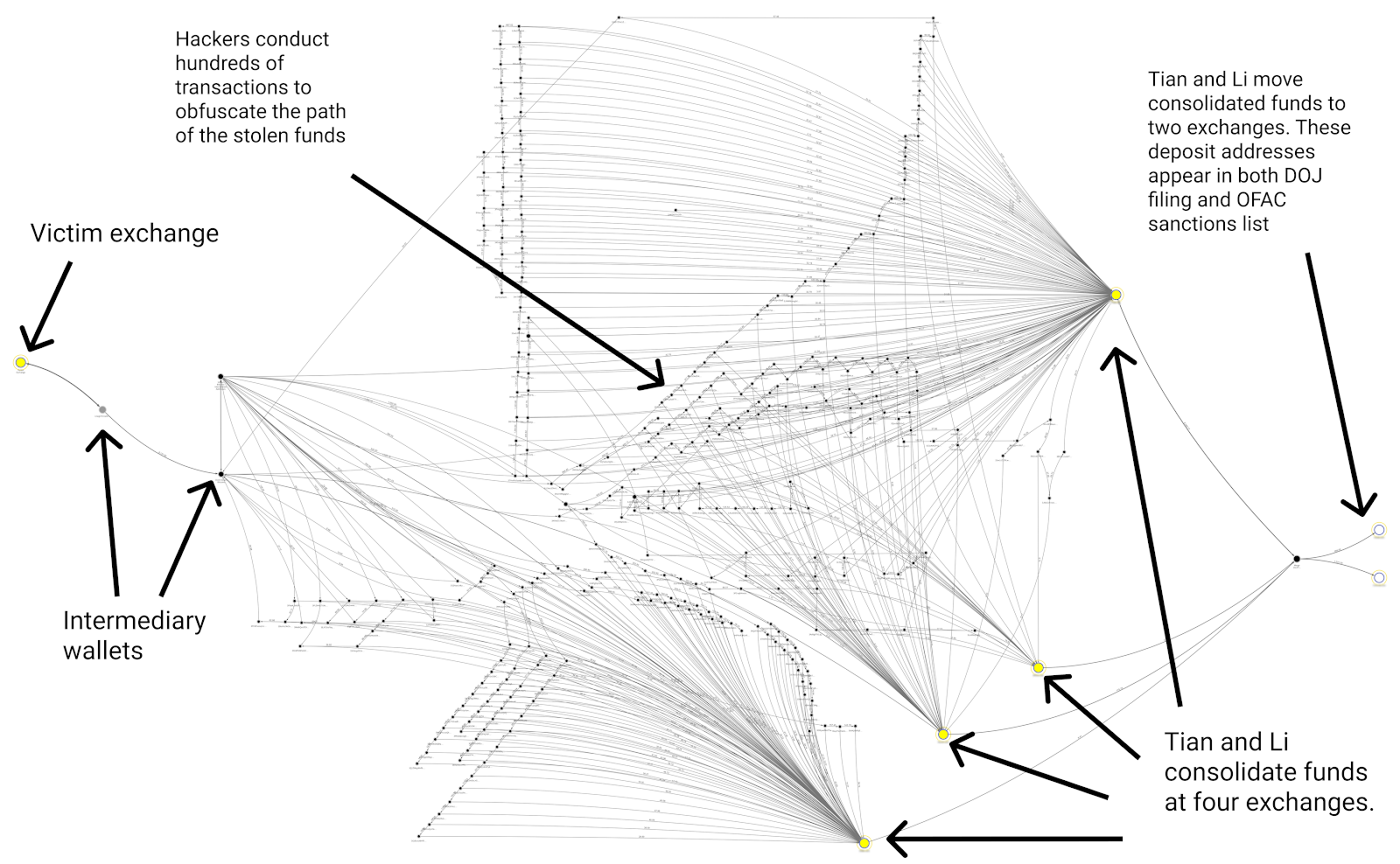
Funds move from left to right, starting at the victim exchange and then undergoing hundreds of transactions, presumably in an effort to throw law enforcement off the scent. Eventually, Li and Tian consolidated the funds at two exchanges and from there, converted them into Chinese yuan and deposited them into their bank accounts. Li and Tian seem to have circumvented the exchanges’ KYC measures using doctored photos, which you can see below.

Thanks to a combination of blockchain analysis and traditional information gathering, plus information provided by compliant exchanges, investigators were able to identify Li and Yian’s role in the operation despite their efforts to hide their activity.
The cryptocurrency addresses implicated
In total, 146 cryptocurrency addresses and accounts were implicated between the OFAC sanctions and DOJ civil forfeiture action. 40 of those addresses, including all 20 of those added to OFAC’s sanctions list, are deposit addresses at cryptocurrency exchanges. 126 of the 146 are standard cryptocurrency addresses. The remaining 20 are more difficult to categorize, but appear to be identification numbers and login information (e.g. usernames, email addresses) linked to exchange accounts. It’s important to keep in mind that the OFAC sanctions and DOJ filing are two separate actions brought by separate agencies with different goals and evidentiary standards, which may be why DOJ’s filing named more addresses.
In total, Tian Yinyin and Li Jiadong laundered over $100 million worth of stolen cryptocurrency using the 146 addresses and accounts named by both OFAC and the DOJ. Below is the full list:
20 cryptocurrency addresses added to OFAC sanctions list:
1EfMVkxQQuZfBdocpJu6RUsCJvenQWbQyE
17UVSMegvrzfobKC82dHXpZLtLcqzW9stF
39eboeqYNFe2VoLC3mUGx4dh6GNhLB3D2q
39fhoB2DohisGBbHvvfmkdPdShT75CNHdX
3E6rY4dSCDW6y2bzJNwrjvTtdmMQjB6yeh
3EeR8FbcPbkcGj77D6ttneJxmsr3Nu7KGV
3HQRveQzPifZorZLDXHernc5zjoZax8U9f
3JXKQ81JzBqVbB8VHdV9Jtd7auWokkdPgY
3KHfXU24Bt3YD5Ef4J7uNp2buCuhrxfGen
3LbDu1rUXHNyiz4i8eb3KwkSSBMf7C583D
3MN8nYo1tt5hLxMwMbxDkXWd7Xu522hb9P
3N6WeZ6i34taX8Ditser6LKWBcXmt2XXL4
134r8iHv69xdT6p5qVKTsHrcUEuBVZAYak
14kqryJUxM3a7aEi117KX9hoLUw592WsMR
15YK647qtoZQDzNrvY6HJL6QwXduLHfT28
1F2Gdug9ib9NQMhKMGGJczzMk5SuENoqrp
1PfwHNxUnkpfkK9MKjMqzR3Xq3KCtq9u17
1AXUTu9y3H8w4wYx4BjyFWgRhZKDhmcMrn
1Hn9ErTCPRP6j5UDBeuXPGuq5RtRjFJxJQ
3F2sZ4jbhvDKQdGbHYPC6ZxFXEau2m5Lqj
73 cryptocurrency addresses named in original DOJ civil forfeiture filing:
8bdd991a7b8e2fe1bfcb6b19ac3cf3e146cba415
1FKMe2Nyue2SDufB4RciiXsEEpAxtuBxD3
c4f9ee31626c8dee0ec02744732051e8b416e63e
a4b994f1ba984371ecca18556fe1531412d5c337
19YVKCETP8yHX2m2VbEByVgWgJUAZd5tnS
1K1fa3ydmpWMuX8gWHk5W6gnVFX7nGQJsu
17KS1C6DxViF68YaSAhWUrnaCtxzbMq7CB
1MP62xKDtbL79wQ8f8LbAg9dPpUHFTEVbJ
1GsAS3z7eG4Vw2QbyVqnR7cRQmpeRsCpt1
1K7cMd9RgwhThXi6VDu3Roti2W4241MLfG
1FhsTJ7hQKvpFXPRFFjsFPHQT4pQMQpgw1
1FzKR8XDmdrTRYfMcZRf3NPvSgyrUoG8kq
1AsHQhhCYwgd71cxnHA9a8dWeEh22ivdqn
1DZdJNQsEutzud3YX28DFXfzKVyEfoN8t2
1K83LzD1QR2iUVtHckFMUzzdF3xUhtNdYb
1DX3zJV4djK9CgCP48Ym3LEryq5RVdhWH8
1EFNjtGnJ7WohXd8L17NGA4N5osKRj98QN
1EU4tNd1RbhDCfkiQrtj6nfzxeRxRA9rBm
17Wx3A1tmiTnxJ9FAq7em1n6SxtXSG4r5F
1QBbEUUhG7CRJzJrSEnUvwrycYZzKB8YEq
113vSKMWvuM8Weee2neMScXqdtXFLvy8z7
12DCmGuX87aCzxCDneyAxZdVWapuza9UyR
12JSAKyUMFMFp2ao5Rqt3s3X4xrQMXMzkr
12urwZAF7JvdhiQcYVbNG7VtKP3165pPnf
13Bcq6AcWusG3YKsYadBRNwnfezUrhRDER
13u7zCciSC7yGKfe8qqvQxK7BnGiwpdAbQ
14jP1TjTjrFBVFKUMcGaPjGRHaWAK6QVr7
14umE3q9knsWKZhjPgLQyv4rrCNjfXpAuF
16RWbMVHvERVUjrh28rRugmrgeDW1nweoo
17PSv7hd2cvSmgMTFw8CA3hjdYtGWuPh98
18LX9wjgjDbmRZXYhDLzZWCQ3pkUGB6gFf
19RfkmQPS3wBF5XhjcZwnbpMkd96GoituJ
19V5YCatY8sfdNuskawrGmbrZEohLkqV3d
1Ax8m2gy1Ta6vQTMStnWdCh71oMX7Z4nen
1Bht2x8Y8tJLpXxqK9LX4ehtLNk6kh3FLk
1C3K6yYxr1xomotxkEbMLAcm3jVKDSyFBd
1C4hPundX3pBSiNbhkLpuLp246Ggc8gmwx
1C5S12fBSmeVedaEAqQzFf29H9hUucojPA
1JCWsAC86pokjDrvQsRWoU2jm9qA9Wc4qh
1K2FgtrdGk767RoLf8dN8tr5XsVc5st6RZ
1L5mPKvfKzGY2J99HtpoefxqbpLDxyMAZq
1LcsVyCd6yEyibDQS2WcxzTBT1iJGAqLhS
1MVkopW6PPWZtSAtP4295B6KfH93YKToZU
1Nmd7KBc3P6RgYcZ5n8ftdbw7z4jEzUSVj
1NMpPj2zUSPodncvZGp7owP2nttAgyFuY3
17UwTn7cVxu5ivkBnkPo83Gjtowi8dx75Q
1A3uGGvHFBauSmjZvdZFF6gjc8VSjgF7UY
1Bm659Wu5xVppUNRh7jKNFMboTbDepgmbm
18atn6kuyKzhnsWK554Uj6j1PAv3sPmx2p
18YNDeHouezsyxcvntohev9kANrMXiGBxr
1CD483mLYrMJwZF5drZnoPKSBbFTMSVvGf
1P8y7bj28tsq76anvKLgmhbbnTc1ZGcUVa
1Pa32FPFQJ5VdozwmMGE1ANNWVGB3XQJie
15pPmUErhTb8CaWF5x8iQggX3zK1y99ZN1
1EFWRRLUM3jy2poCpY7ALq2m7PPakyvns1
37JN1EDYCGYVabtofvyKKLtpA6uU3UBMLo
39PAYsdx2zi7GUhV71cx1zpp1N8495t58f
3ACmZQBNZsDDDs3UGoC6DeKMKHTe9RW1yu
3AUHHS4NQjJRAMbjdkeTdLDv9ZFeA9n1o3
3GAwA7PvLiHKjcmN2nsrHEpN7Qt9jwMQ4h
3HoJydELfq2kyZk9M6yug6CLQmYCS7FrJj
3M23QTysjRsfmJz4aDdc9RpaXjVZmbWKEt
3Nis34RW9uGV5mbovNidNNsxRTWwwqb1PS
LLzTJFu3UcwXRrwaq2gLKnJaWWt3oGHVMK
01facd1477e6df9e27fe9f0a459aaa0769c9af82
7175d1fa4461676ab8831483770ff84483f26501
93d8edbc42e547c571ce5af95f70c291d706925c
b35dff36ff3d686a63353fa01327f3ff4874cf21
bc1q39hkr7ta25e65d7u0pm09l99jvfny4lp3vam4q
81b34f7a426b31e77e875b8d00d830f8a5b044cb
fc3D6aee062c45b31e946ba49a7aa5addf1b53c6
bd72f2cfb28ed38b7cea94e26603983ce028c927
c137c3135eb8e94aa303d52c607296ba470e1a57
33 Bitcoin and Ethereum addresses added to DOJ civil forfeiture filing on 3/6/2020:
0xBeE7853cB00B240929d75F923c7B8D62Bb8D6673
0x0a28b41C4b8CD2390494e0349B068f0562E87986
0x1245C2Dc54Dfed6F79a078A2424F45cdaB47Cc25
0x16a02ceC301d61A37C2935e355Fe93F4660f50F8
0x1C2D9f510A79C9A7fc8A7E9fD8487Fd66CA47DAc
0x2F3FFef70A59BC688b1037881d42a4276E8714F1
0x571bC459f3430A00861b77aa9873f4268e350Cf7
0x5db0ca9D5057F6C62178771Fe967789DE8214bf5
0x649982b2e8b2e23dbdb024bBc76aB8625B326965
0x6eDfa4055fcfd53a90145037B41fBFc7D963a96D
0xA10F87EdB2FE6F910F6595e79177236CaAd3a8bA
0xA39528bC1ec1992baA8bf7a6B7CA262053De7b6E
0xa8D24c26E6b272040ef3505D3038575CF5F16B35
0xC79Ee5c784e89b69BBB5b1a7288111f4395942Cc
0xd434486Fd19d1098663194889a4717e8047d6DA5
0xE7192668b244Fd20aC8447C758Fbc1AC1109885A
0xf24D59CF8A22293E9c7626e17dE7331272aF4385
0xF288eAD5257B6b9D0BABAfD1E6BcF5524d600897
0xdadb6B7c7A075F11Fd0b3727c8A2C0937ba288DA
0x09a66a888e9C454683De5790066A26249195d06B
0x9654380B76636a04a463BC65b2eCE4854BE8F221
0xa0174BCdAeFC58CA89edb800963C7DfF9273f0C3
0x8A710F209744985999AbD9e400c5d5282287D515
0xfc38b48cC00d71F5Fad28e9bbf812A0dc89131d3
0xB0dEd65f252feF4825Bf66A8E11017deea621770
0xd4Bd4AdD6c39693056eF8505298b318b585aCFAa
0x40aF83D50fb8Ca47d759eC775479Eb3976C76DF4
0x6Df26eCa0A339242414487754FE8e26a92D11e00
0x4be124c42Ed71eD0177e5b5e45F06A387b4296EA
0xc25Ca97987D1D9cfe505c3A3e28d533B4Cf19EA1
13582daSueZgFoxyUdXLkUZLazoPkoonYj
34pQ6Bp1wNFXbFvHHDcKonBHuMK2hVWrVW
3MWvuBffavZeaSjPKYDdkUZQQuwJH1JQcN
20 non-standard cryptocurrency addresses or exchange account ID numbers named in DOJ civil forfeiture filing:
User ID 35802038 at VCE10
User ID 35977393 at VCE10
User ID 35978286 at VCE10
User ID 36020326 at VCE10
User ID 38785599 at VCE10
User ID 9fdbd2ca-3994-411b-9ddb-f5318b63049d at VCE3
VCE12 internal transaction ID Fnc4bjm7ehwhdk6h4d
VCE12 internal transaction ID pd7e8fxxkuy2gfge7f
Account 1000021204 at VCE6
Account 1000079600 at VCE6
User IDs 1473600 & 14736005 at VCE5
User IDs 458281 & 4582819 at VCE5
User k*****@****** at VCE1
User 881051 at VCE7
Account 14166934 at VCE 11
Account 14166961 at VCE 11
Account 14167009 at VCE 11
User DavidniColinDC3 at VCE4
User Ep4444 at VCE4
User Sma414 at VCE4
Next steps for Chainalysis
As soon as we received the news Monday, we tagged the specific addresses mentioned in the OFAC sanctions as sanctioned entities and those in the DOJ filing as stolen funds in all of our products. Within 24 hours, we also sent alerts to any of our Chainalysis KYT clients with historic exposure to these addresses. Any future transactions involving these addresses will, of course, also generate alerts to clients with exposure.
We’re currently working with clients who have either hosted or previously transacted with the relevant addresses. Our goal is to help them identify information relevant to this case and understand how they can improve their KYC procedures to prevent this kind of activity in the future. Chainalysis is working to identify any further addresses associated with this laundering activity, and we will continually update labels in our products to reflect the latest information and inform customers of any exposure they may have.
