This blog is an excerpt from the Chainalysis 2021 Crypto Crime Report. Click here to download the whole thing!
2020 will forever be known as the year of Covid, but when it comes to crypto crime, it’s also the year that ransomware took off.
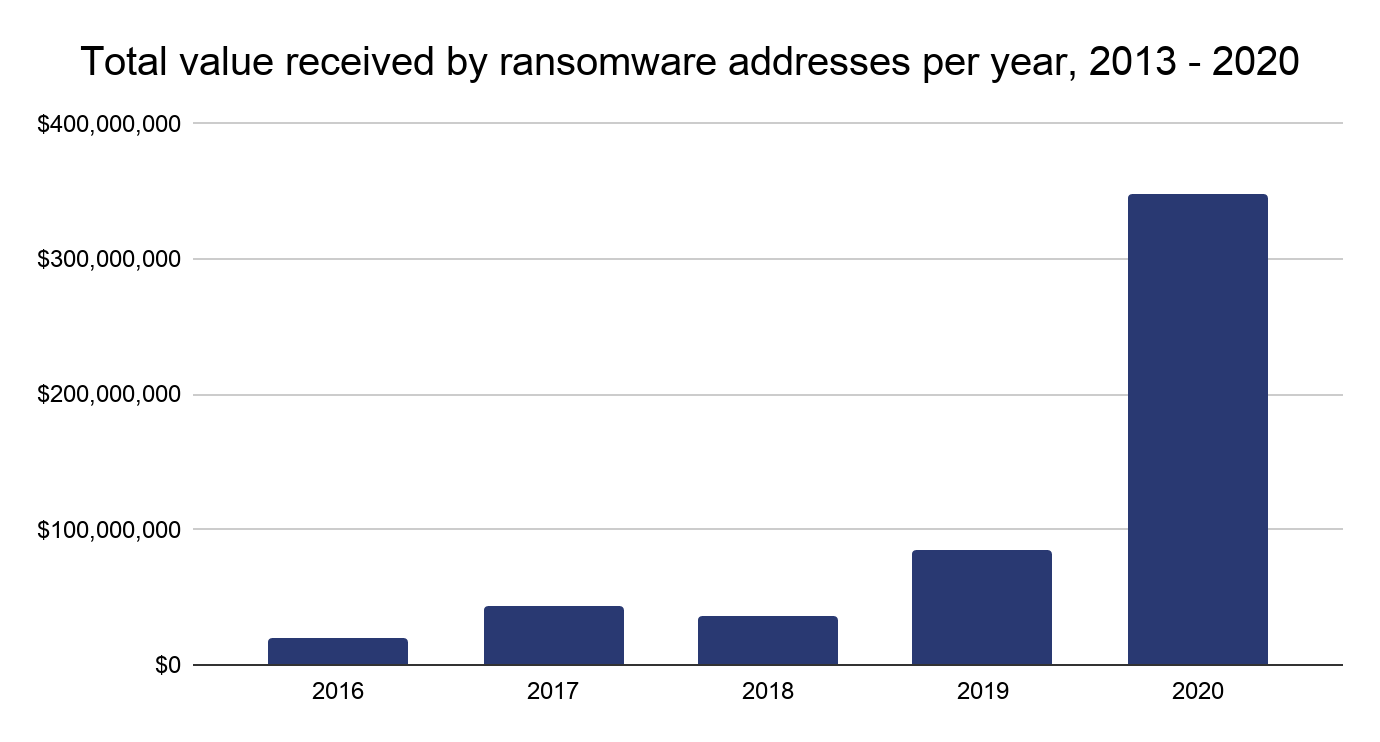
Blockchain analysis shows that the total amount paid by ransomware victims increased by 311% this year to reach nearly $350 million worth of cryptocurrency. No other category of cryptocurrency-based crime had a higher growth rate. Keep in mind too that this number is a lower bound of the true total, as underreporting means we likely haven’t categorized every victim payment address in our datasets.
2020’s ransomware increase was driven by a number of new strains taking in large sums from victims, as well as a few pre-existing strains drastically increasing earnings.
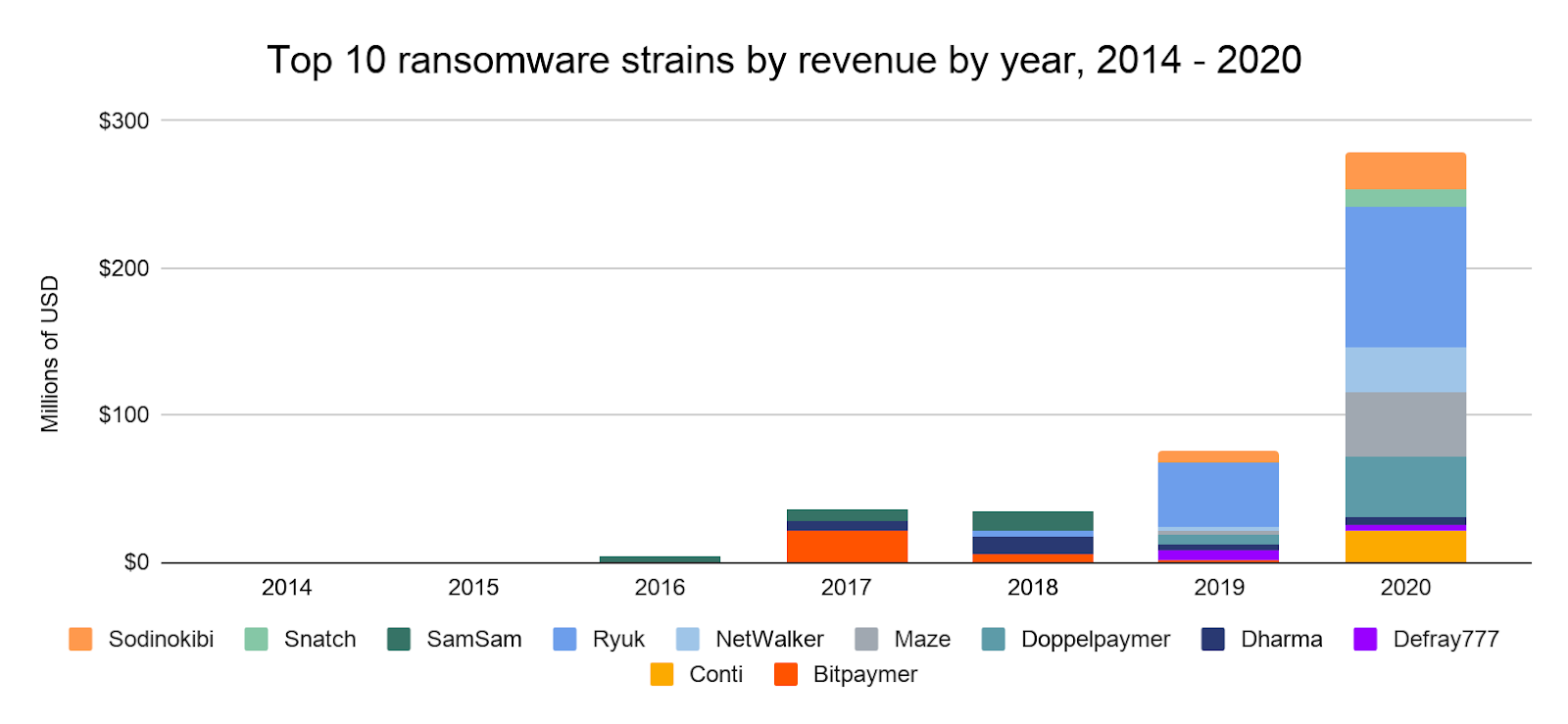
Ransomware strains don’t operate consistently, even month-to-month. Below, we see that the top-earning strains have ebbed and flowed throughout 2020.
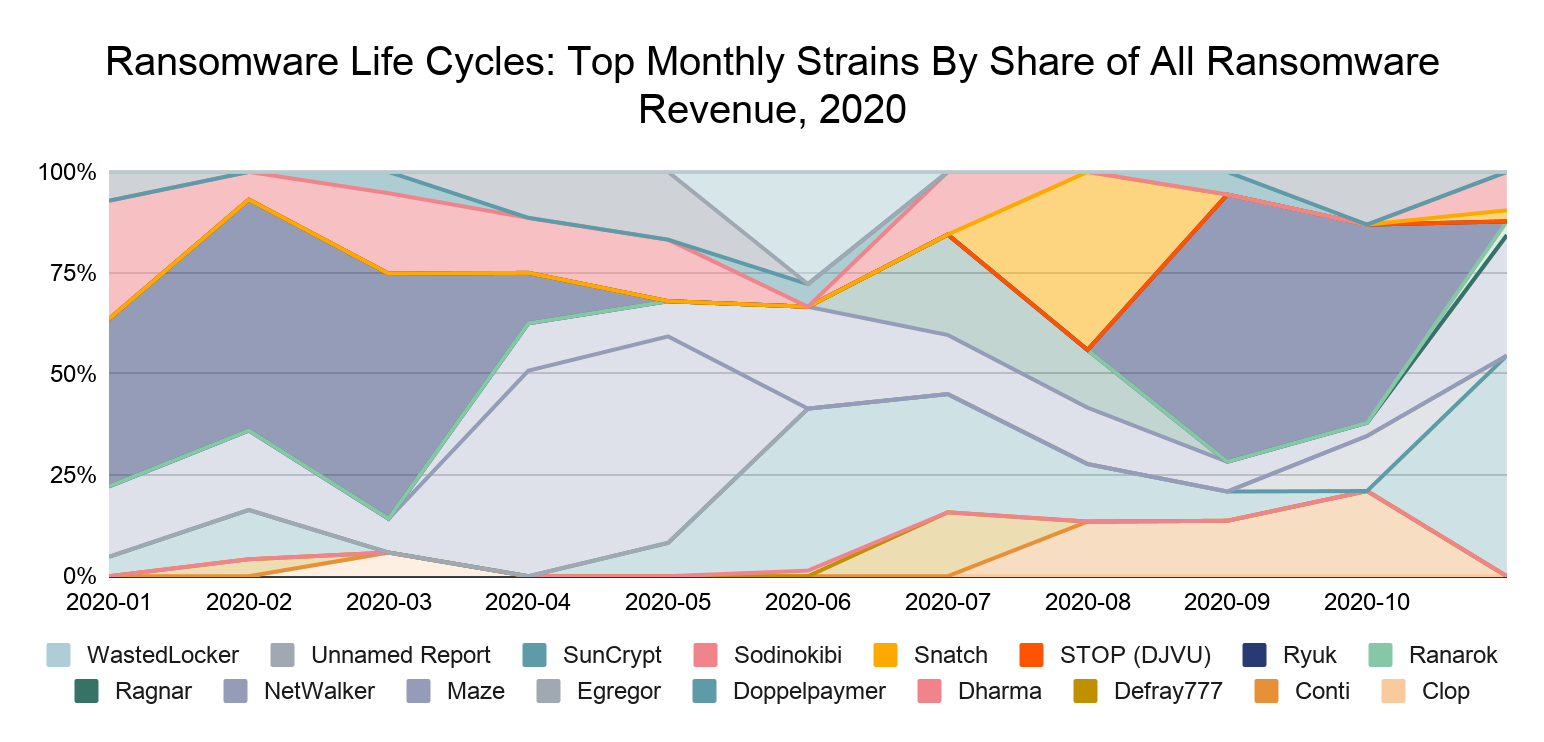
The number of strains active throughout the year may give the impression that there are several distinct groups carrying out ransomware attacks, but this may not be the case. As we explored in last year’s Crypto Crime Report, many strains function on the RaaS model, in which affiliates “rent” usage of a particular ransomware strain from its creators or administrators, in exchange for a cut of the money from each successful attack.
Many RaaS affiliates migrate between strains, suggesting that the ransomware ecosystem is smaller than one might think at first glance. In addition, many cybersecurity researchers believe that some of the biggest strains may even have the same creators and administrators, who publicly shutter operations before simply releasing a different, very similar strain under a new name. With blockchain analysis, we can shed light on some of these connections by analyzing how addresses associated with different ransomware strains transact with one another.
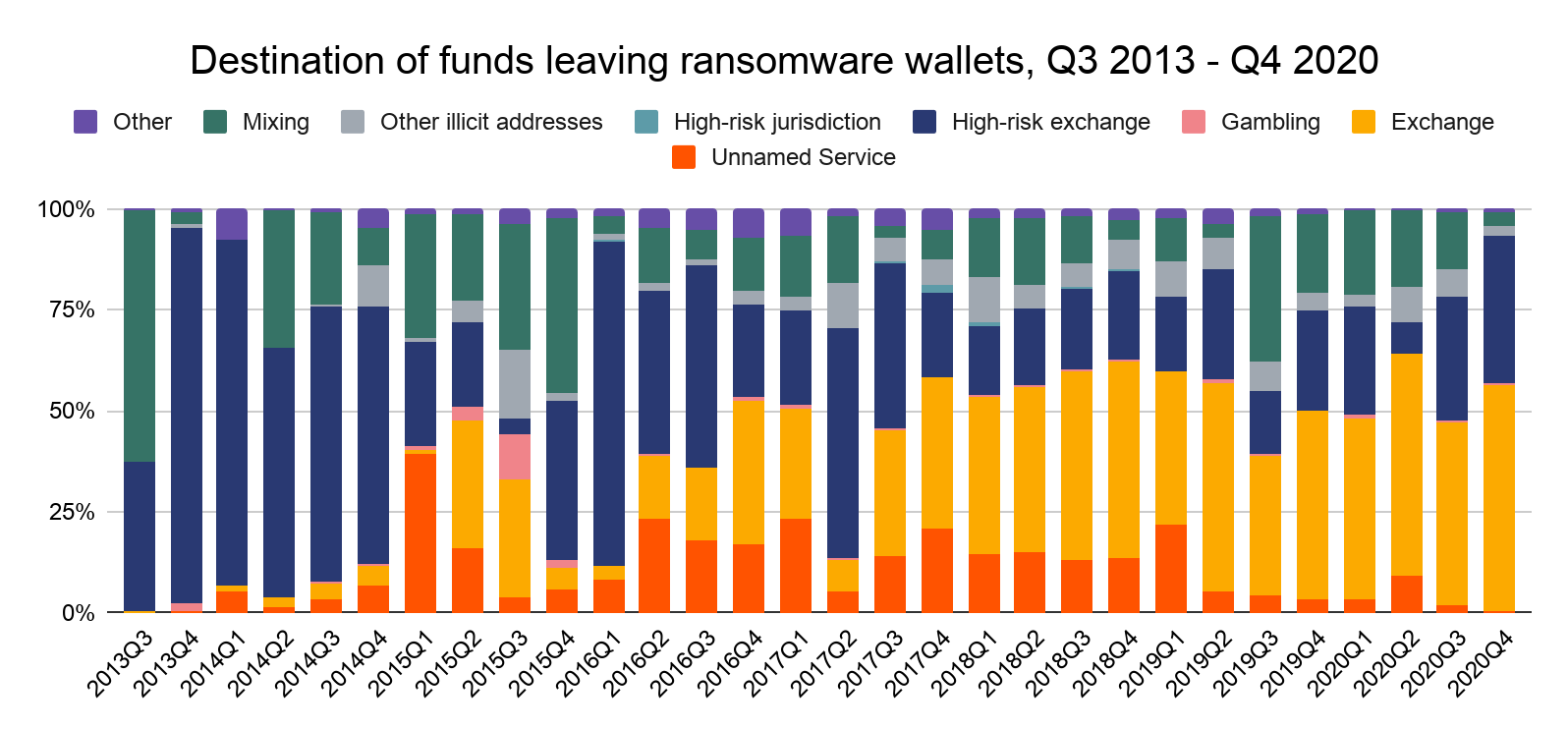
Ransomware attackers move most of the funds taken from their victims to mainstream exchanges, high-risk exchanges (meaning those with loose to non-existent compliance standards), and mixers. However, the money laundering infrastructure ransomware attackers may be controlled by just a few key players, similar to the ransomware strains themselves. We’ll explore the interconnectivity within the ransomware ecosystem below.
Mapping the ransomware ecosystem
We can find connections between ransomware strains by examining common deposit addresses to which wallets associated with different strains send funds. We believe that most of the cases of deposit address overlap represent usage of common money laundering services by different ransomware strains, as we posited in the example of transactions connecting Maze and Egregor. Again, instances of overlap in money laundering services is important information for law enforcement, as it suggests they can disrupt the activity of multiple strains — in particular, their ability to liquidate and spend the cryptocurrency — by taking one money laundering operation offline.
However, money launderers aren’t the only ones ransomware addresses send cryptocurrency to. Ransomware operators rely on several types of third party providers to conduct attacks. These include:
- Penetration testing services, which ransomware operators use to probe potential victims’ networks for weaknesses.
- Exploit sellers, who sell access to vulnerabilities in various types of software that ransomware operators and other cybercriminals can use to inject victims’ networks with malware.
- Bulletproof hosting providers, who provide web hosting customers can purchase anonymously and are generally lenient on the types of sites customers are allowed to host. Ransomware operators often need web hosting to set up command-and-control (C2) domains, which allow hackers’ computers to send commands to victims’ machines infected with malware.
Similar to money laundering services, law enforcement could theoretically disrupt several ransomware strains if agents were able to identify and act against service providers ransomware operators rely on to carry out attacks.
But just how concentrated are the deposit addresses receiving funds from ransomware addresses? Let’s investigate.
As we mentioned at the beginning of the section, the majority of ransomware funds move to cryptocurrency exchanges. This activity is relatively concentrated to just a few services — a group of just five receives 82% of all ransomware funds. But what about when we look at the deposit address level?
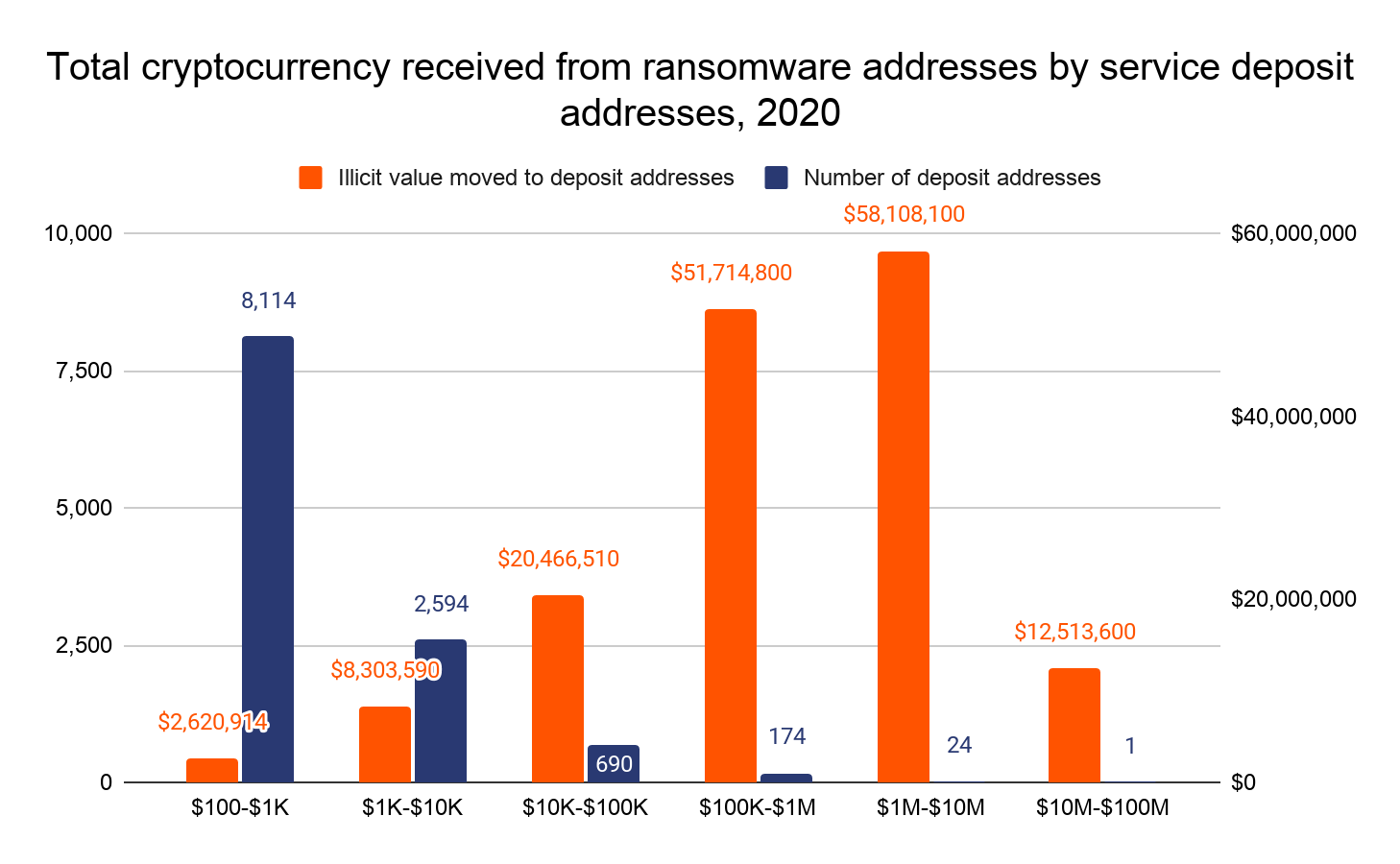
The data shows that ransomware money laundering is even more concentrated at the deposit address level. Just 199 deposit addresses receive 80% of all funds sent by ransomware addresses in 2020. An even smaller group of 25 addresses accounts for 46%.
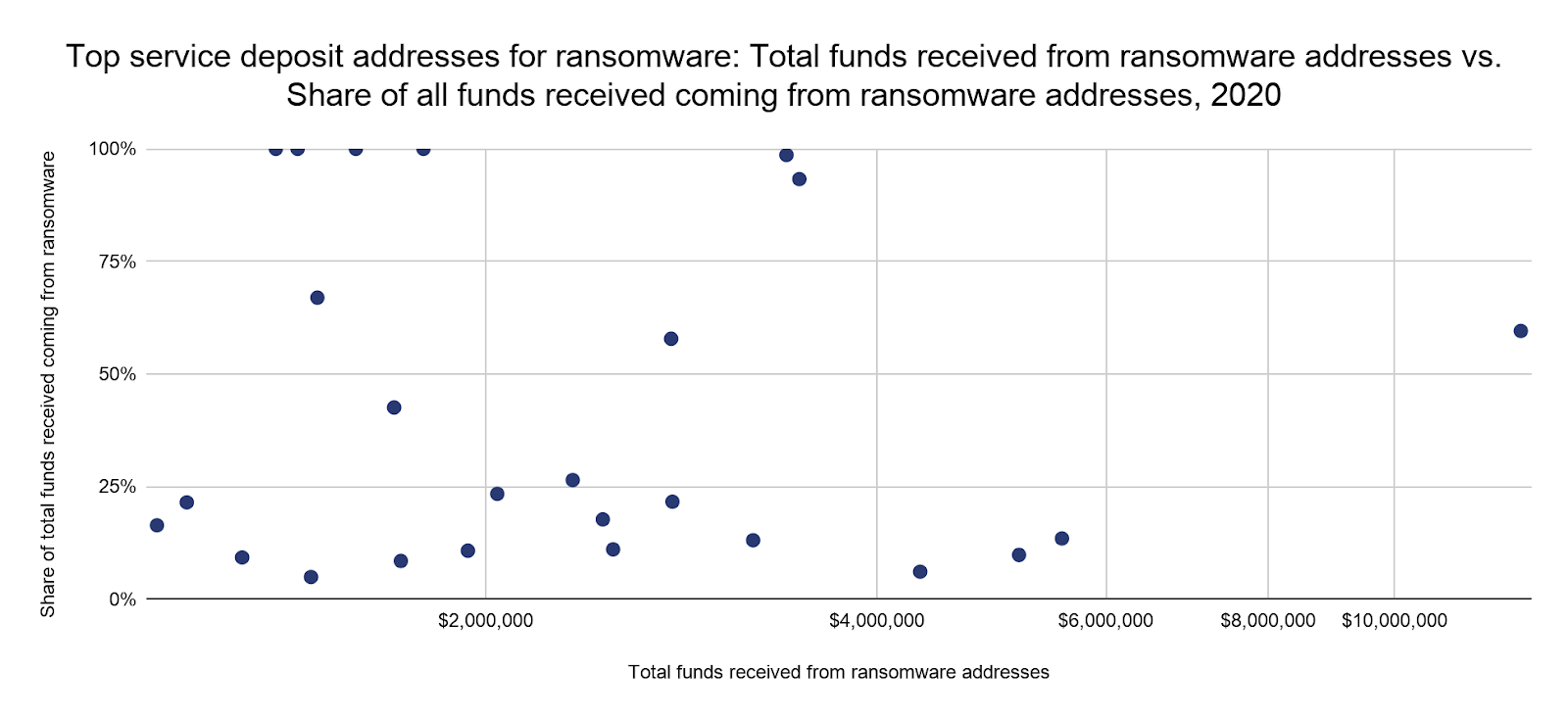
On the scatter chart above, we sort those 25 addresses by the total amount they’ve received from ransomware addresses on the X axis, and the share of total funds they’ve received that ransomware makes up on the Y axis. We see that save for a few outliers, ransomware makes up a relatively small percentage of all funds received by these deposit addresses. Below, we look more closely at the transaction history of one of those deposit addresses.
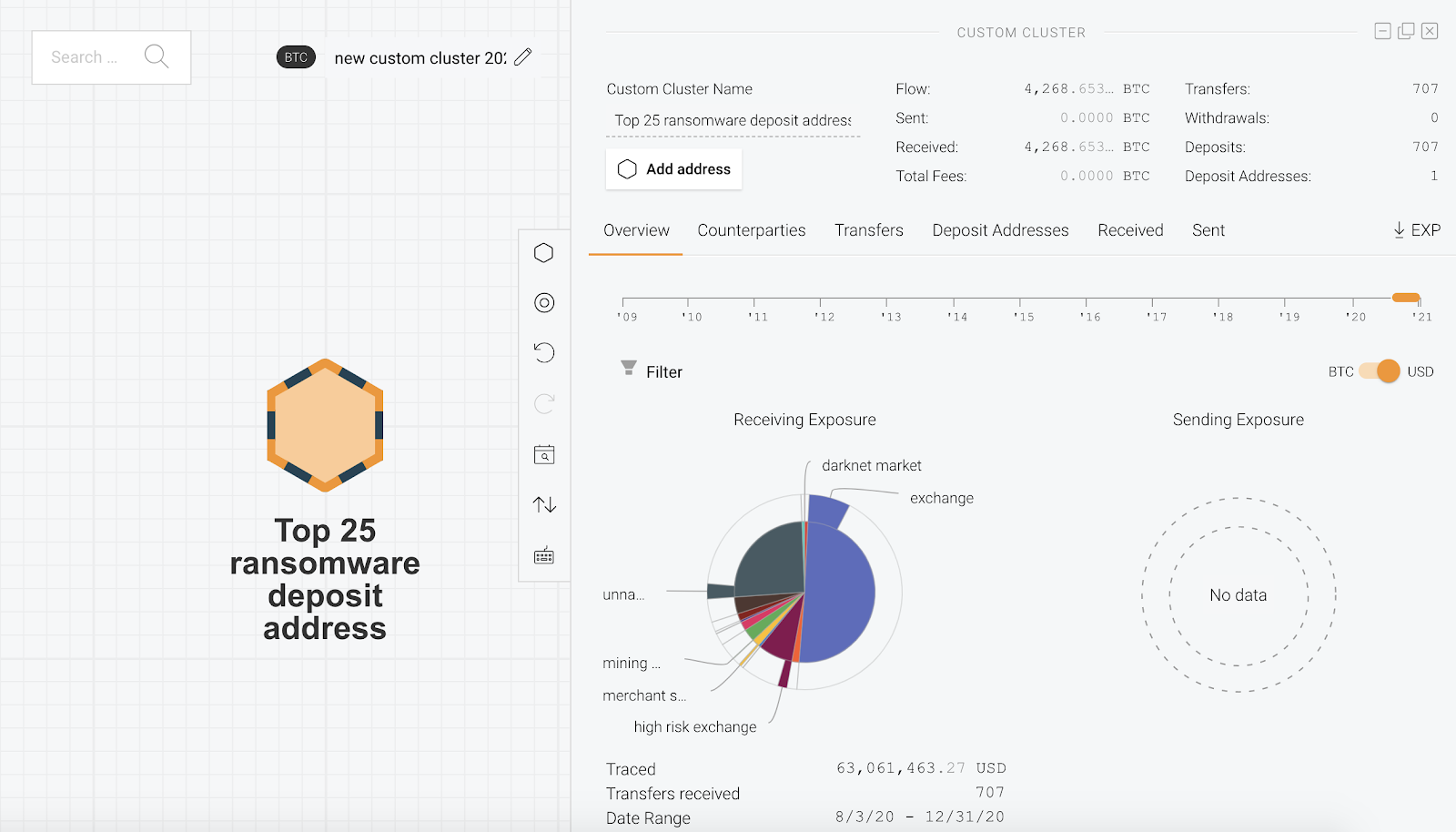
This deposit address belongs to a nested service hosted at a large, international cryptocurrency exchange and has been active since August 3, 2020. Between that date and the end of 2020, it received over $63 million worth of Bitcoin in total. Most of it appears to be non-illicit activity — nearly half of those funds come from other mainstream exchanges, though a quarter comes from unknown services that may be identified as linked to criminal activity at a later date. However, while the share is low, the address has still received over $1 million worth of Bitcoin from ransomware addresses, as well as $2.4 million from multiple scams. Overall, criminal activity accounts for 10% of the address’ total cryptocurrency received. Most of the other deposit addresses on our scatter chart with low shares of total funds coming from ransomware fit a similar profile.
Regardless of the differences in activity between individual addresses, the data makes one thing clear: The ability to cash out ransomware proceeds is supported by the owners of a very small group of deposit addresses. By targeting those deposit addresses, cryptocurrency businesses and law enforcement can work together to reduce ransomware attackers’ ability to turn their profits into cash.
This blog is an excerpt from the Chainalysis 2021 Crypto Crime Report. Click here to download the whole thing!
