We’re now six weeks past the Merge, as Ethereum underwent its switch from proof-of-work (PoW) to proof-of-stake (PoS) on September 15, 2022. In the leadup, we published a blog speculating how the Merge might affect the cryptocurrency ecosystem generally and the Ethereum blockchain specifically, and shared a few on-chain indicators to keep an eye on. One thing we highlighted was the possibility that scammers may seek to take advantage of confusion around the Ethereum Merge. Sure enough, that’s exactly what happened. Merge-related scams took in $1.2 million worth of Ether shortly before, during, and after the Merge took place on September 15, and briefly became the dominant scam type in the Ethereum ecosystem. We’ll examine this trend more in-depth below, and also look at who was most impacted.
How Eth Merge scams spiked in September
What exactly is a Merge scam?
Most Merge scams functioned similarly to the classic trust trade scam, in which the fraudster tells victims to send them some amount of cryptocurrency to receive more in return (typically double the victim’s initial payment), often impersonating celebrities to do so. In this case, scammers told victims they should send in cryptocurrency in order to “upgrade” to the new Ethereum blockchain and receive funds in return.
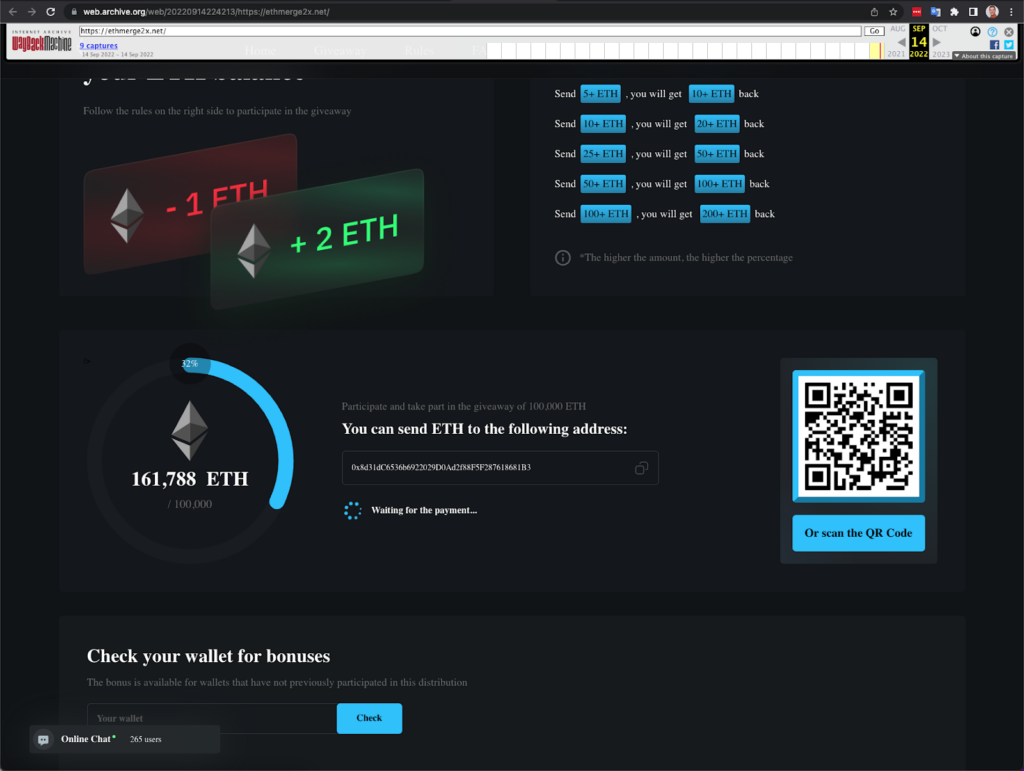
Caption: The scam invites users to send 1 ETH to an address and receive 2 ETH in return.
This strategy proved quite successful, as we can see on the chart below.
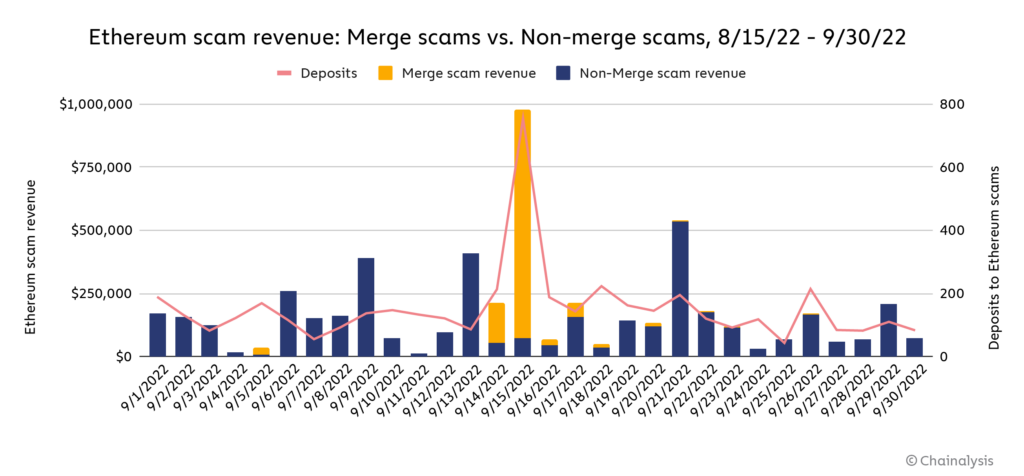
September saw massive spikes in scam revenue on the day of the Merge, the vast majority of which went to Merge scams. In fact, Merge scams crowded out virtually all other Ethereum scamming activity on the day of the Merge, collecting over $905,000 worth of Ether on September 15 compared to just under $74,000 for all other Ether scams. However, this activity dissipated as quickly as it appeared, with scamming activity returning to normal levels within days, and Merge-related scams all but disappearing by the end of September.
Still, it’s hard to understate how dominant Merge scams were on and around the date of the event. For instance, Merge scams made up eight of the top ten Ether scams on September 15, and all of the top five.
| Rank | Merge-related scam? | Scam name | Value received (USD) | Deposits received |
| 1 | Merge Scam | ETH-Merge.blogspot.com | $307,640 | 123 |
| 2 | Merge Scam | Ethereum-Merge2x.com | $213,751 | 120 |
| 3 | Merge Scam | Ethereum-Celebration.com | $208,649 | 109 |
| 4 | Merge Scam | MergeStarts.com | $95,616 | 52 |
| 5 | Merge Scam | MergeUpgrade.com | $31,154 | 12 |
| 6 | Non-Merge Scam | MintCastaways.com | $27,456 | 5 |
| 7 | Merge Scam | Rise2ETH.com | $21,928 | 15 |
| 8 | Merge Scam | MergeMoon.com | $15,514 | 13 |
| 9 | Non-Merge Scam | PacmanNFT.xyz | $15,452 | 57 |
| 10 | Merge Scam | ETHMerge2x.net | $9,436 | 4 |
In fact, the data suggests it was hard not to make at least some money if you were running a halfway decent Merge scam on and around September 15. Below, we compare the daily success rate for Merge-related scams compared to all other scams throughout the month of September. We define success by whether or not the scam made $100 or more on a given day that it was active, with active defined as whether the addresses associated with the scam transacted on the day in question. One caveat to this method is that it excludes scams that were active but simply didn’t transact on a given day — the least successful possible scams. But, since our goal here is to compare the performance of Merge-related scams and non-Merge scams, we believe the analysis is still revealing as the success rate for both scam types undercount complete failures.
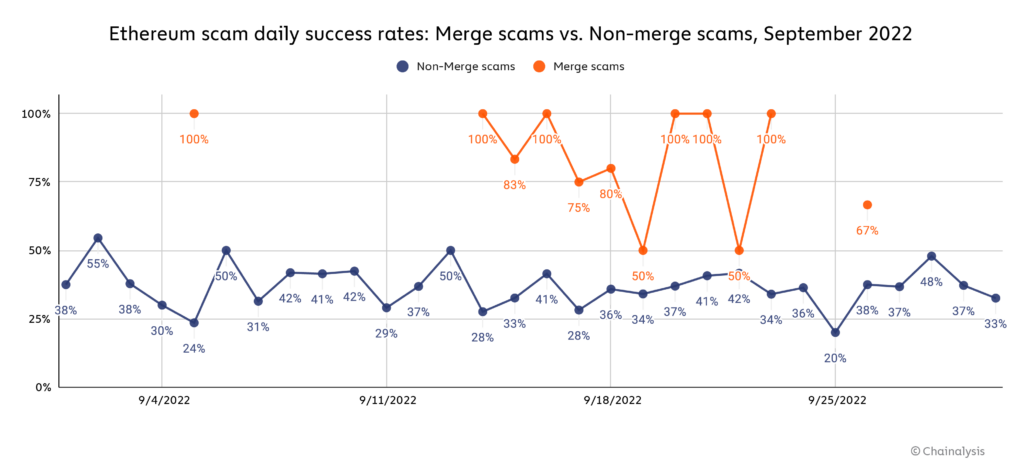
Amazingly, Merge-related scams had an 83% success rate on September 15, the day of the merge, and a 100% success rate on several other days before and after the Merge. Merge scams had a higher success rate than all other Ethereum scams nearly every day they were active, though there were many days that none were active. Overall, the data suggests that scammers were able to take advantage of lack of understanding around the Merge to fleece unsuspecting users.
Who was hit hardest by Merge scams?
We can also apply our geographic analysis methodology to look at the regional footprint of Merge scams. Overall, most Merge-related scams focused on a limited area, with a plurality receiving payments from users in just one country, and a majority from users in three or fewer countries.
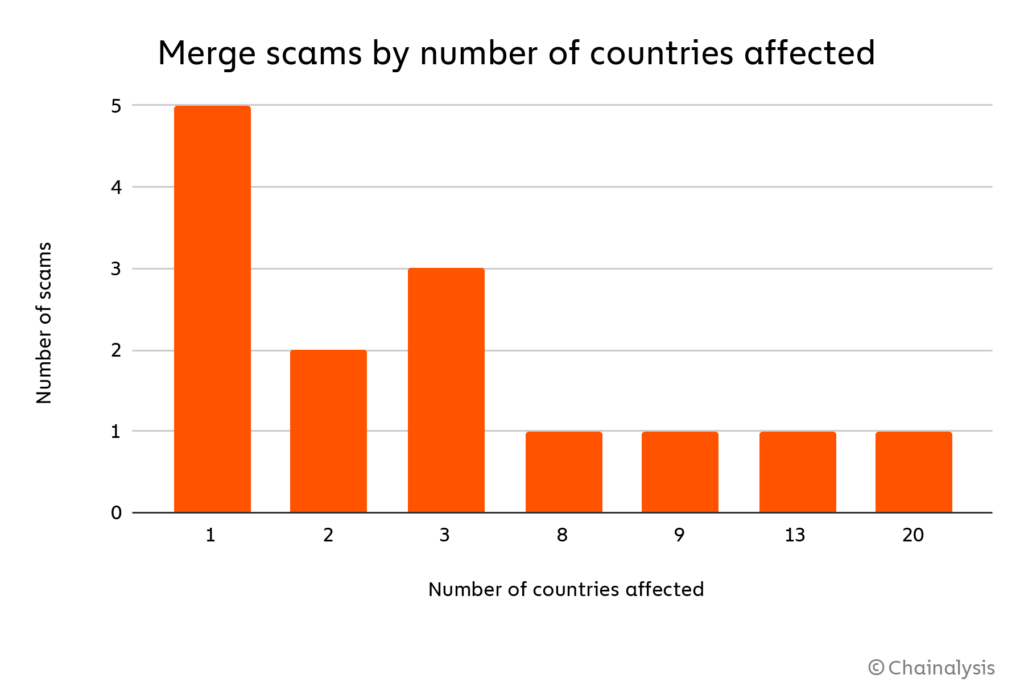
We think this pattern could partially reflect scammers’ preference to focus on countries they themselves reside in, possibly due to language barriers. On the chart below, we can see some of the countries most affected by Merge scams during the month of September, with a second axis showing engagement with other Ether-based scams for comparison.
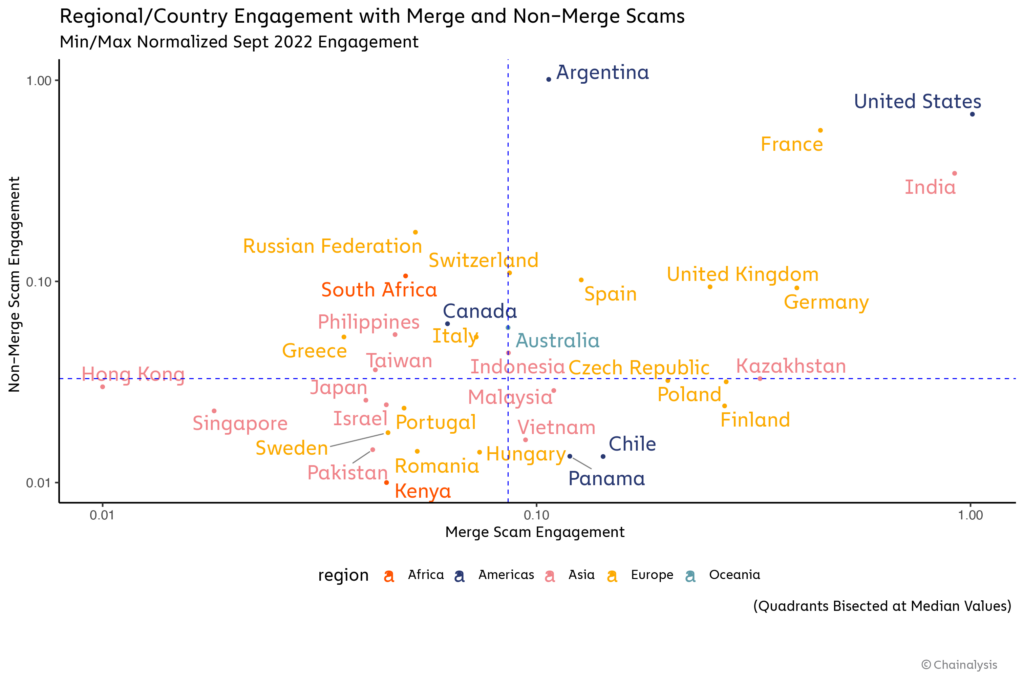
In the upper-right hand quadrant, we see countries that engaged heavily with both Merge and non-Merge scams more than the median country. The United States and India, which overall engaged the most with Merge scams, both fall into this category during the month of September.
Things get even more interesting in the bottom right quadrant, where we see countries that engaged with Merge scams more than the median country, but comparatively less with Ethereum scams in general. Why might these countries have fallen prey to Merge scams in particular? There are a few potential reasons. Some of the Merge scams we study appear to have targeted those countries specifically. For instance, Finland engaged with Merge scams at a surprisingly high level, but nearly all of that engagement was driven by three scams that only targeted Finland — one of those scams, “buterin-merge[.]com,” received more Finnish engagement than any other Ethereum scam during the month of September. However, other countries engaged with Merge scams that targeted several countries, so some set of additional country-specific features might be at play. One of those features appears to be wealth — scams are all about money, after all.
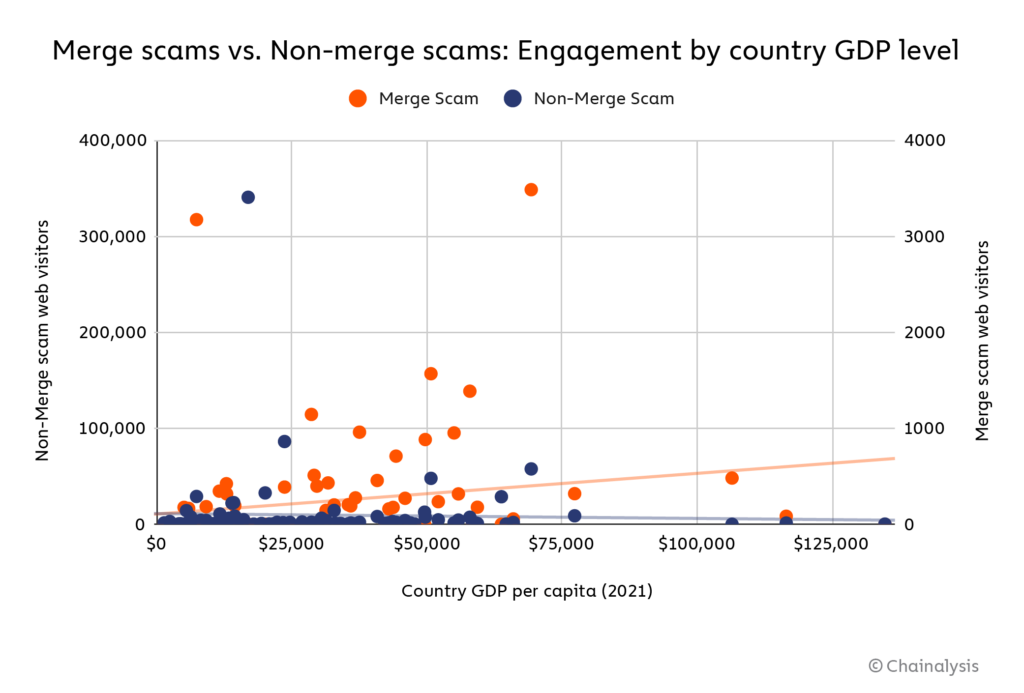
Looking at all the countries in our dataset, it is interesting to note that Merge scams were more likely than non-Merge scams to target users in countries with higher GDPs, by a small but noticeable margin. It’s possible that Merge scammers purposely targeted users in wealthier countries under the assumption they’d be more likely to invest more in the scam, but it’s unclear why Merge scammers would be more likely to do this (or do it successfully) than other scammers in the Ethereum ecosystem.
Big events like the Merge are a scammer’s best friend
With big DeFi hacks stealing headlines of late, it can be easy to forget that scamming is still and likely will remain the biggest form of cryptocurrency-based crime — one that’s uniquely damaging to cryptocurrency adoption because of the way in which scams prey upon the trust of users. And unfortunately, times of change for the industry such as the Merge are a boon to fraudsters, as confusion and lack of knowledge around them can be taken advantage of by bad actors. The spike in Merge-related scamming makes clear that the industry must work to educate users on what things like the Merge mean for them, as well as which common scam types to avoid generally.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.
All trademarks, logos and brand names are the property of their respective owners. All company, product and service names used in this website are for identification purposes only. Use of these names,trademarks and brands does not imply endorsement.
